Clients can't reconnect after pfsense reboot
-
@prophet I'm using 2.3.2 and its working like a charm so far. I will post again after 24 hours as I continue to monitor this
-
@kengo excellent!
does it also "remember" clients/users across reboot or do they have to sign in again?
-
I'm curious too.
I've been using 2.3.2 for a while, and I don't remember if users are all logged out. Normally, yes, they would have been.Most of the captive portal settings don't have anything to do with created entries in the related ipfw tables. Better yet : back then, there were no "tables" to hold the authorized devices, there were just rules.
Only this one : "Per-user bandwidth restriction" ( Default download (Kbit/s) and Default upload (Kbit/s)) are used when creating rules.I can imagine that, when FreeRadius is used to restrict "bandwidth restriction" or "Amount of Download and Upload Traffic" is counted, and the rule (and related limiter/pipe) vanishes a moment for a device, things really start to break.
So, saving the config == everybody has to start over. This is far more saver.Btw : Why should one want the captive portal setting regularly ? I didin't touch mine for weeks, if not months. Ones set up as needed, no need to change something.
-
hi everyone, sorry for the delayed response.
I can confirm that 2.3.2 has resolved the captive portal issue on one box. but what i am curious is why on another box, 2.4.4 still works fine.
@prophet upon reboot of the 2.3.2 machine, users need to login again. I think this is the intended behavior. captive portal works flawlessly now and doesn't kick machines off the internet after a period of time.
as for my setup, I added all the mac address of my routers/access points to the Mac filter in captive portal, not sure if that helped.
-
@kengo said in Clients can't reconnect after pfsense reboot:
as for my setup, I added all the mac address of my routers/access points to the Mac filter in captive portal, not sure if that helped.
I did the same thing.
Even basic access points could have NTP services (time keeping) or could need updates, so these should be able to communicate with the net.@kengo said in Clients can't reconnect after pfsense reboot:
upon reboot of the 2.3.2 machine, users need to login again. I think this is the intended behavior
Exact.
@kengo said in Clients can't reconnect after pfsense reboot:
captive portal works flawlessly now and doesn't kick machines off the internet after a period of time.
by default, a captive portal should kick of user after a certain time (hard or soft time out).
Except the ones listed on the MACs / Allowed IP / Allowed host names tabs -
@prophet I have same problem :(
-
I have the exact same problem of OP @kengo which he mentioned in the 1st message. I cannot downgrade now. Is there a fix or workaround? Does setting an hard and idle time out fix the issue? Is there a way we can automatically log all users out of the captive portal every time the firewall reboots? Please advice. Thanks.
-
@darkblack to solve problems after reboot i just customized pfSense-rc script to automatically truncate captive portal sqlite3 database.
Still looking for a way to automatically login devices after reboot, but i'm working with Fauxapi and i could be discovering something useful soon.
-
@prophet Thanks a lot for your response. Can you please tell me what piece of code you added and at what position (between which lines), it will be helpful and others who stumble on this rather frustrating issue
-
in /etc/pfSense-rc, at the very end just before "exit 0".
sqlite3 /var/db/captiveportalyourname.db <<EOF DELETE FROM captiveportal; EOFWhere "yourname" is obviously the name of your captive portal.
-
Instead of deleting files - and editing pfSense core fils, I prefer to use the API.
Consider this :
Install the Shellcmd package which permit us to execute 'commands' at startup.Place a file called "captiveportal_disconnect_all.php" in the directory /root
#!/usr/local/bin/php -q <?php /* Disconnect all clients on all captive portal instances */ require_once("/etc/inc/util.inc"); require_once("/etc/inc/functions.inc"); require_once("/etc/inc/captiveportal.inc"); global $g, $config, $cpzone, $cpzoneid; /* Are there any portals ? */ if (is_array($config['captiveportal'])) { /* For every portal (cpzone), do */ foreach ($config['captiveportal'] as $cpkey => $cp) /* Sanity check */ if (is_array($config['captiveportal'][$cpkey])) /* Is zone enabled ? */ if (array_key_exists('enable', $config['captiveportal'][$cpkey])) { $cpzone = $cpkey; $cpzoneid = $cp['zoneid']; captiveportal_disconnect_all(); } log_error("All users disconnected after system start-up"); } ?>Add a command in the Shellcmd package :

Done. -
@gertjan much better, thanks.
do you have something similar to programmatically login users? given that we already have mac address, last ip, username. -
@prophet said in Clients can't reconnect after pfsense reboot:
do you have something similar to programmatically login users? given that we already have mac address, last ip, username.
You were reading my mind

What you're asking for is the other way around : if a database exists with logged in user(s), why not rebuilding the ipfw rules for them ?!
Right ?I guess it's possible.
But : it's time out for me right now. I wrote the lines in the post above on a live system, throwning out users and restarting pfSense while testing : people are yelling all around me.
I'll have a shot at it tomorrow.Basically, it should be a loop that iterates the database, and for every user
function portal_allow($clientip, $clientmac, $username, $password = null, $attributes = null, $pipeno = null, $authmethod = null, $context = 'first') {should be called (see /etc/inc/captiveportal.inc, around line 2212)
Except that this function does all the work (a lot of work !), and adds the user to the database

Keep in mind : firewall states and stuff like that will be gone.
It should be something that is "voucher compatible", "Radius compatible", etc. -
-
@darkblack I'm using the captive portal for years, but yesterday, during testing, I saw for the first time that connected users during a Diagnostics => Reboot are still listed as connected, but the related ipfw firewall rules were gone.
My pfSense never reboots by itself - it has an UPS. I never saw the issue before.
So, for myself, I can't call it an urgent matter. This issue exists only in the latest version or two.I guess the pfSense authors should wipe the sqlite file during reboot, as @prophet proposed.
-
I understand. But our case is where, the entire office powers down at EOD (UPS, lighting, et al) and powers up the next morning. . So a major headache for us. Eager to try the solution today.
-
@gertjan said in Clients can't reconnect after pfsense reboot:
What you're asking for is the other way around : if a database exists with logged in user(s), why not rebuilding the ipfw rules for them ?!
Right ?Yes sir.
But which firewall rules are created for a succesfully authenticated client?
I notice ipfw creates these rules, output filtered with relevant tables:--- table(captive_auth_up), set(0) --- 172.17.17.11/32 18:65:90:82:81:c3 2004 181565 12852760 1542305056 --- table(captive_auth_down), set(0) --- 172.17.17.11/32 2005 418527 595361621 1542306032- I tried to manually recreate these but i couldn't figure out how to make mac address based rules in ipfw.
- Aren't these rules just doing some traffic shaping? How are they critical to the system?
Thank you
-
@prophet said in Clients can't reconnect after pfsense reboot:
I tried to manually recreate these but i couldn't figure out how to make mac address based rules in ipfw.
ipfw : you have 2 possibilities : the easy one : the manual. https://www.freebsd.org/cgi/man.cgi?ipfw(8)
How pfSense makes rules is not hard to find : it all in /etc/inc/captiveportal.inc ^^@prophet said in Clients can't reconnect after pfsense reboot:
I notice ipfw creates these rules, output filtered with relevant tables:
--- table(captive_auth_up), set(0) ---
172.17.17.11/32 18:65:90:82:81:c3 2004 181565 12852760 1542305056
--- table(captive_auth_down), set(0) ---
172.17.17.11/32 2005 418527 595361621 1542306032Exact.
Here are the details https://www.netgate.com/docs/pfsense/captiveportal/captive-portal-troubleshooting.html@prophet said in Clients can't reconnect after pfsense reboot:
Aren't these rules just doing some traffic shaping? How are they critical to the system?
Exact. Pipes, (queues ?) are build for every connection.
Because this option exists :
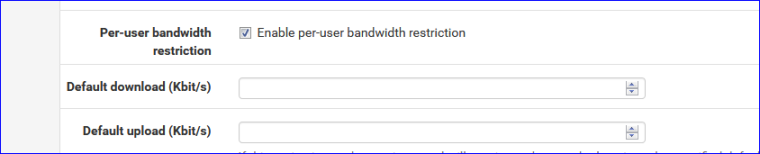
Pipes exists, wether you use them, or not.
These pipes have to be created when entering the IP's of the client into the two tables myzone_auth_down and myzone_auth_up. -
@prophet said in Clients can't reconnect after pfsense reboot:
Configured everything (I'll use pfsense as captive portal) and everything worked perfectly as captive portal without user authentication (a simple splash screen with login button and no auth is enough for me).
I had PFBox 2.3 and clean installed 2.4.4 and have the same problem i resolved it somehow by setting Idle timeout to 3 to 4 hours and it work like charm.
@Gertjan said in Clients can't reconnect after pfsense reboot:
Instead of deleting files - and editing pfSense core fils, I prefer to use the API.
Consider this :
Install the Shellcmd package which permit us to execute 'commands' at startup.Place a file called "captiveportal_disconnect_all.php" in the directory /root
#!/usr/local/bin/php -q <?php /* Disconnect all clients on all captive portal instances */ require_once("/etc/inc/util.inc"); require_once("/etc/inc/functions.inc"); require_once("/etc/inc/captiveportal.inc"); global $g, $config, $cpzone, $cpzoneid; /* Are there any portals ? */ if (is_array($config['captiveportal'])) { /* For every portal (cpzone), do */ foreach ($config['captiveportal'] as $cpkey => $cp) /* Sanity check */ if (is_array($config['captiveportal'][$cpkey])) /* Is zone enabled ? */ if (array_key_exists('enable', $config['captiveportal'][$cpkey])) { $cpzone = $cpkey; $cpzoneid = $cp['zoneid']; captiveportal_disconnect_all(); } log_error("All users disconnected after system start-up"); } ?>Add a command in the Shellcmd package :

Done.I wanna try @Gertjan API :)
-
do we still need this also for pfsense 2.5 sir? I'm using this also for my captive portal in 2.4.4 p3 before with the system patches fix for "You are connected". just recently upgraded to 2.5.