Inter VLAN routing
-
Hi,
I'm new to pfsense. I am trying to setup VLAN routing. I have multiple VLANs setup but they can't communicate with each other. How do I allow for inter VLAN routing?
-
@sunruh said in Inter VLAN routing:
Hi,
I'm new to pfsense. I am trying to setup VLAN routing. I have multiple VLANs setup but they can't communicate with each other. How do I allow for inter VLARules on the vlan interfaces to allow any out?
The networks are directly attached so its not a routing issue.
-
@nogbadthebad I have firewall rules set for each VLAN as such, example for VLAN10
Action: Pass
Interface: VLAN10
Address Fam: IPv4
Protocol: Any
Source: VLAN10 net
Destination: anyAm I missing something?
-
No per what you stated you have done that would work. But then again we had a user just awhile ago that had also enabled blocking rfc1918 on his vlan interfaces and bogon ;) Which would be above any rules you create on the interface.
Did you set a gateway on these rules? If so that could be stopping it.
Do the devices in the other vlans have host firewalls? Those could be stopping it.
Please post up screenshot of your vlan rules.. Because its many times where the user says they put in rule X, but they really have Y... For example use state any for protocol but maybe you put in just tcp or just udp.. Or maybe vs vlan net, you put vlan address when dropping down, etc..
To be sure its just easier to see the rules ;)
-
Nope looks fine, normally when people post the same question its they've not created the firewall rules.
What happens if you do a packet capture on vlan 10 on pfsense and do a ping from a host on vlan 20.
You should see something like this:-
16:12:44.655402 IP 172.16.2.20 > 172.16.1.2: ICMP echo request, id 50436, seq 0, length 64 16:12:44.656579 IP 172.16.1.2 > 172.16.2.20: ICMP echo reply, id 50436, seq 0, length 64 16:12:45.655706 IP 172.16.2.20 > 172.16.1.2: ICMP echo request, id 50436, seq 1, length 64 16:12:45.656919 IP 172.16.1.2 > 172.16.2.20: ICMP echo reply, id 50436, seq 1, length 64 16:12:46.659663 IP 172.16.2.20 > 172.16.1.2: ICMP echo request, id 50436, seq 2, length 64 16:12:46.660846 IP 172.16.1.2 > 172.16.2.20: ICMP echo reply, id 50436, seq 2, length 64If you don't see anything on vlan 10 move the capture to vlan 20.
Is traffic even hitting the firewall interfaces, it could be your tagging on the switch ?
Also is the subnet masking correct, I've seen people use the wrong mask and the pc has thought its on the same subnet when it actually isn't.
-
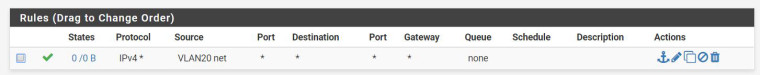
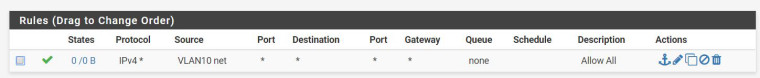
Here are screen shots of my rules:
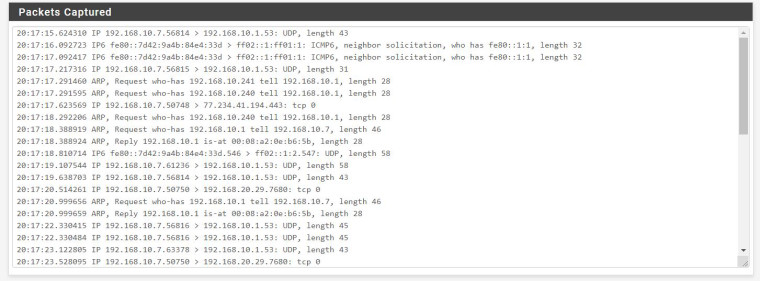
I did the capture and it looks like this:
I also captured vlan 20:
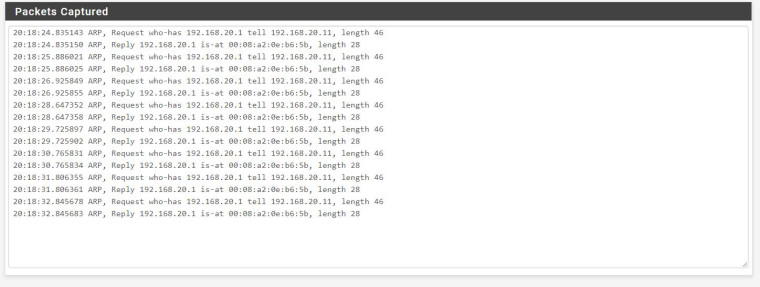
If I'm understanding the capture correctly they get to the gateway but not any farther. Am I reading that right?
-
There are no hits on your firewall rules.
Is the first rule you posted from vlan 20 or vlan 10?
-
The first rule is VLAN20 the second is VLAN10
-
I'd be looking at the switch config.
Do any mac addresses appear in the ARP table ?
-
Both of the Mac addresses show up in the ARP table.
-
I meant devices that aren't the router, i.e. PCs on vlan 10 & 20
-
There are zero hits on those rules... Can a device in a vlan even ping pfsense IP in that vlan?
-
Yes, there are other devices showing up in the ARP table from vlan 10 & 20.
I was able to ping the pfsense IP from each vlan. I just can't seem to ping/communicate from vlan to vlan.
-
Local firewalls on the hosts preventing traffic from other subnets?
-
@derelict
 yes, that was the issue. Thank you everyone for you help with this!
yes, that was the issue. Thank you everyone for you help with this! -
If you were hitting pfsense trying to go to another vlan, then the allow rules would show hits - or the default deny would log it, etc.
Do you have rules in your floating tab? Those are evaluated before the interface rules..
BTW - I stated host firewalls over 4 hours ago ;) heheeh
-
I have similar issue, 2 vlans, 103 and 203, I was trying to ping from iphone to printer or windows to printer or windows to iphone, no luck. All should be good imho. I even added extra rules to pass traffic between vlans but based you what you have here this is not needed.
rules for 103
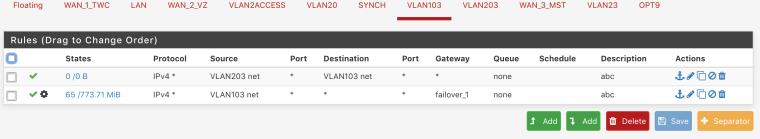
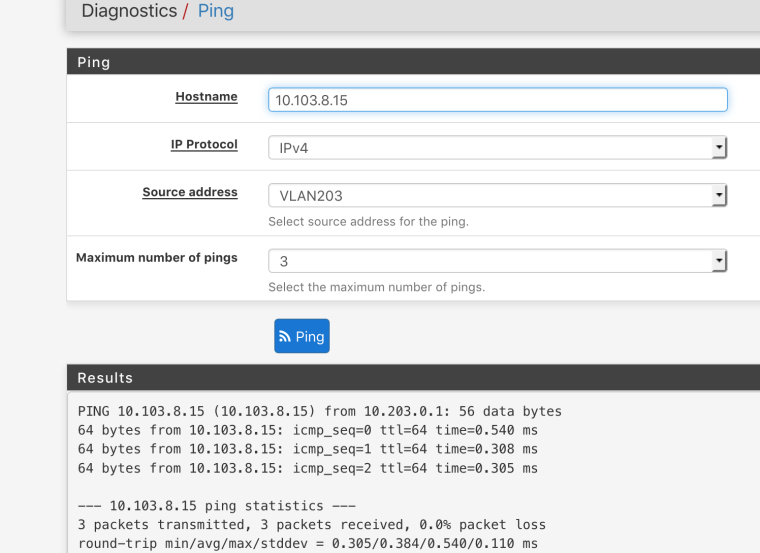
same logic for 203Diagnostics is a pass, weird
-
VLAN103 will never see traffic sourced from VLAN203 coming into it. That first rule is useless (note the 0/0 counters there since it's impossible for traffic to match it). If you want 203 to be able to ping 103, put the rule passing that traffic on 203.
That ping works because you are sourcing it from the firewall.
https://www.netgate.com/docs/pfsense/firewall/firewall-rule-basics.html
https://www.netgate.com/docs/pfsense/firewall/firewall-rule-troubleshooting.html
-
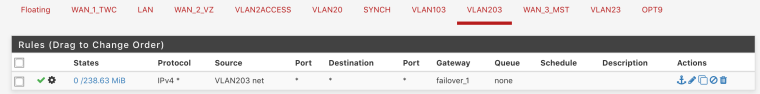
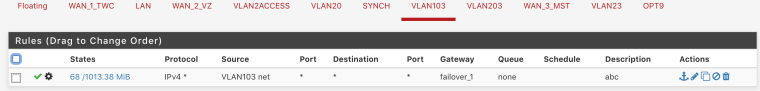
Both vlans 103 and 203 have imo correct rules
-
your forcing traffic out the gateway how can traffic from 1 vlan get to the other vlan - via that gateway your sending it out of.
If you want vlan 103 to talk to 203 then you need a rule that allows said traffic before you send traffic out some gateway. On the vlan 103 interface, and vise versa for 203 to talk to 103
You also have to be concerned that the device your trying to get to on the other vlan allows access from the source network IPs - ie the devices local firewall if any.