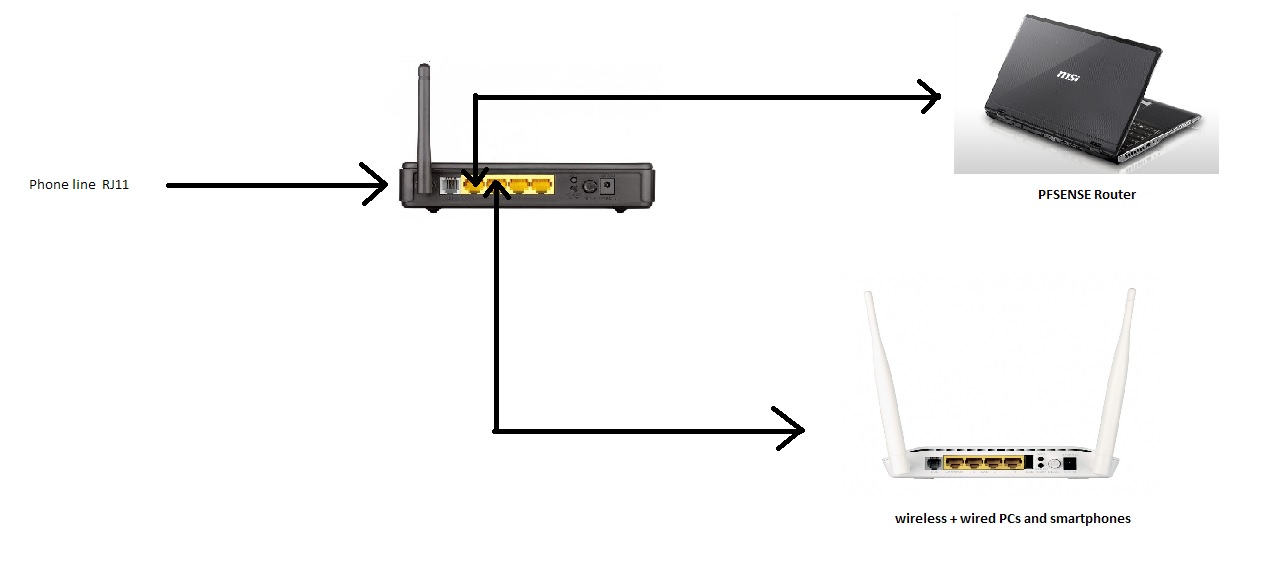
"Poor man" home network first try
-
Hello every one.
After spending the last week lloking around, watching youtube videos and what not, i decided to come here and see if i can manage to create my own home network with Pfsense as a router of course.
first things first this a prototype build that i'm trying theorically and then for real with what i have to see if it's possible to achieve or not.
Also, i know that what i'm using does not have AES-ni support, i live in a poor country with a mere 145€ per month, so buying new hardware or complementary hardware is not an option right now, but that's no problem, this is just a test subject to see if i can be accomplished.
And lastly i'm a total newbie in this kind of networks so go easy on me if i think in a stupid way about something here lol.
OK so here we go, i have in my possession an old fonctional laptop witrh a dual core p6100 and 4gb of ram that has only one ethernet port of 10/100 speed, and i have two modem/routers, a d-link 2640u(old) and a 2750u bought recently and is used as my current modem/router but it gives me absolutely no control and data over who is using what and who's sucking all the bandwidth ...etc.
i stumbled on a video one day about PFsense as a router and liked the idea of what it offered si i decided to give it a go and started looking around.
i've found a video that makes use of a computer with a single ethernet + a smart switch and i liked it and wanna do the same but i wanna try to get it to work with what i have right now, this is how it is theorically in my head.
phone line ----------> 2640U (bridge mode) -----------> PFsense (pppoe connection )lan +vlan over the same port like it's explained here https://www.youtube.com/watch?v=z59_MWWPL-Q&index=44&list=WL& )
the problem here is that if i wanna connect the 2750u as just some kind of an access point (wifi most but would like ethernet too if possible), i would have to connect it to the 2640U spare ethernet ports but i don't know if it would really work that way since i don't know if bridging it would disable every other networking option or not.
i would like to have your advices on this setup and if it may work (or not) for like 10 to 15 devices (2 or 3 ethernet most likely, the rest of them are wireless)
Additional information: our internet speed is just 4mbps so the 10/100 port will handle that without a problem.
for any additional informations you want, please ask me i'll gladly answer them
-
You can not do vlans like that without a smart switch..
-
Yes. The on-board switch in the 2640U is VLAN aware so will either just not pass the VLAN coming from pfSense or, worse, will strip the tags.
I would suggest you might be able to use an alternative firmware on that device to allow control of the switch and pass the VLAN correctly:
https://openwrt.org/toh/d-link/dsl-2640uHowever it looks like that would remove the ADSL support and I imagine you are using that. But you could potentially use that as a managed switch/access point if you have some other device to use as a modem.
Steve
-
Or just get a vlan capable switch to put between.. They are not expensive..
-
@stephenw10 said in "Poor man" home network first try:
Yes. The on-board switch in the 2640U is VLAN aware so will either just not pass the VLAN coming from pfSense or, worse, will strip the tags.
I would suggest you might be able to use an alternative firmware on that device to allow control of the switch and pass the VLAN correctly:
https://openwrt.org/toh/d-link/dsl-2640uHowever it looks like that would remove the ADSL support and I imagine you are using that. But you could potentially use that as a managed switch/access point if you have some other device to use as a modem.
Steve
thank you so much for your answer Steve.
There is a setting under the "internet setup" where i can choose between pppoe and bridge mode that has a connection with Vlan, so i thought maybe "just maybe" i can use the 2640u as a modem bridge AND a smart switch because it has some setting related to the ports that it is why i'm experimenting with this setup that i have in the picture.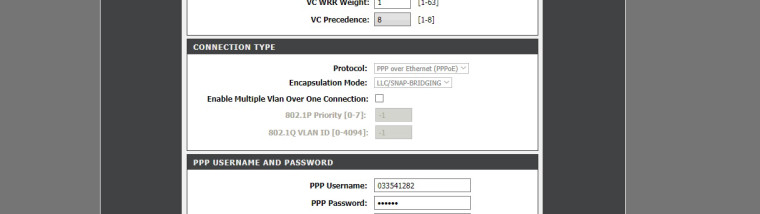
And yes, i need to use the modem part because our internet provider does not gives us internet through RJ45 or cable through RJ-11 phone line so.I did look into the custom firmware but unfortunately both my modem routers are not supported (there are different versions of the same router)
If it can't be done this way i may look into usb-to-ethernet adapter, that way i guess it would be easier to use the 2750u AFTER pfsense no ?
@johnpoz said in "Poor man" home network first try:
You can not do vlans like that without a smart switch..
yes that's whay the person of the video commented when i asked, but i was looking into maybe using one of the modem/routers (preferable the 2640 as modem since it had some issue with wifi)
@johnpoz said in "Poor man" home network first try:
Or just get a vlan capable switch to put between.. They are not expensive..
for 140€ per month to live off, that can be expensive lol, but yes that's what i'm surely gonna do in the future for the final installation
I'm sorry if i sound like an ignorant on the subject because i AM new to this kind of networking setup , and yes i'm not looking for miracles ^^"
-
Technically the 2640u can do it, the hardware is capable but I'd be amazed if they brought out the settings for configuring the switch in the default firmware.
It might pass the tagged VLAN packets through the switch but that would then require the 2750 to be able to use a VLAN which that too probably cannot.Steve
-
@aoikite said in "Poor man" home network first try:
@stephenw10 said in "Poor man" home network first try:
Yes. The on-board switch in the 2640U is VLAN aware so will either just not pass the VLAN coming from pfSense or, worse, will strip the tags.
I would suggest you might be able to use an alternative firmware on that device to allow control of the switch and pass the VLAN correctly:
https://openwrt.org/toh/d-link/dsl-2640uHowever it looks like that would remove the ADSL support and I imagine you are using that. But you could potentially use that as a managed switch/access point if you have some other device to use as a modem.
Steve
thank you so much for your answer Steve.
There is a setting under the "internet setup" where i can choose between pppoe and bridge mode that has a connection with Vlan, so i thought maybe "just maybe" i can use the 2640u as a modem bridge AND a smart switch because it has some setting related to the ports that it is why i'm experimenting with this setup that i have in the picture.
And yes, i need to use the modem part because our internet provider does not gives us internet through RJ45 or cable through RJ-11 phone line so.I did look into the custom firmware but unfortunately both my modem routers are not supported (there are different versions of the same router)
If it can't be done this way i may look into usb-to-ethernet adapter, that way i guess it would be easier to use the 2750u AFTER pfsense no ?
@johnpoz said in "Poor man" home network first try:
You can not do vlans like that without a smart switch..
yes that's whay the person of the video commented when i asked, but i was looking into maybe using one of the modem/routers (preferable the 2640 as modem since it had some issue with wifi)
@johnpoz said in "Poor man" home network first try:
Or just get a vlan capable switch to put between.. They are not expensive..
for 140€ per month to live off, that can be expensive lol, but yes that's what i'm surely gonna do in the future for the final installation
I'm sorry if i sound like an ignorant on the subject because i AM new to this kind of networking setup , and yes i'm not looking for miracles ^^"
both the 2640u and the 2750u have that Vlan thingy that i showed you on the bicture, i'll try setting it up and see if somehow i can make it work one way or another.
If you don't mind explaining to me one thing tho it's gonna be the "vlan" network that's gonna pass the internet to the rest of the network right ? that is if the 2640u does not disable all the rest of the evernet ports when in bridge mode hopefully
-
That setting is for the PPPoE connection only. Many DSL providers require traffic is tagged.
It looks like that is on a separate port on the 2640, eth0. The switch is on eth1 and in standard for will be unconfigured so it might pass VLAN tagged traffic. But you would still need an access point that can use a VLAN directly. I doubt the 2750 can do that with it's default firmware.
Steve
-
@stephenw10 said in "Poor man" home network first try:
That setting is for the PPPoE connection only. Many DSL providers require traffic is tagged.
It looks like that is on a separate port on the 2640, eth0. The switch is on eth1 and in standard for will be unconfigured so it might pass VLAN tagged traffic. But you would still need an access point that can use a VLAN directly. I doubt the 2750 can do that with it's default firmware.
Steve
alright, thank you very much for the patience and the answers with me, i'll give feedback after exêrimùenting with it ^^
-
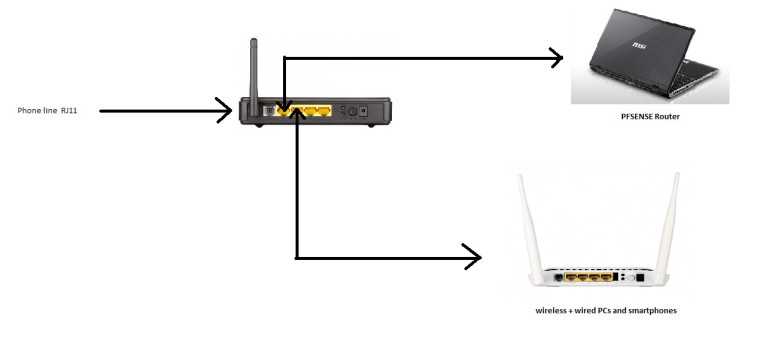
Ok so after some fiddling around i decided to swap it a little around so thatit's only one modem router , the 2750 with all the devices connected to it
i disabled its DHCP and did set it on adress 192.168.1.9 while pfsense is still on 192.168.1.1, tried connecting a laptop with ethernet, and a phone with the wifi, and they both got assigned an IP adress by Pfsense, so that's a step forward for my project.
Also i did setup the same modem as "bridge" for my internet access over the phone line, so i need Pfsense now to dial.
The question i have is, will this "bridging mode" work with my type of ISP way of giving us internet access (over phone line connected to the RJ11 on the modem) ? all the informations i find on the net are for people who gets a direct ethernet cable from their ISP.
and if it does work, can Pfsense establish the internet connection and the redistribute it to the rest of the connected devices ? since it is the the one DHCP that devices connects to THROUGH the modem/router which is acting as an access point so far. if yes, a guide to help me set that up (where to put the vpi//vci and username/password for it to establish the internet connection).
P.S: i can access both PFsense and the 2750 web interface through their respective IP adresses, but PFsense does not show the modem on its DHCP leases tab, whether i set it to 10 or 9, and the phone and laptop were assigned 100 and 101 in the leases tab.
-
Yes, the bridge mode should work. You can pass through the PPPoE connection from the DSL.
The modem should not show on the DHCP leases tab unless it's actually using DHCP which is unlikely. I imagine you set it statically. It will show in Diag > ARP though if pfSense has connected to it recently.
This is an interesting setup if it works. With the PPPoE session passed to pfSense it will have the public IP as it is terminating PPPoE. It will be using the same interface to talk to LAN clients.
The modem should not have any upstream connectivity since it does not have a public IP itself.Steve
-
Interesting is not the term I would use ;) your running your internet and local traffic over the same layer 2.. Doesn't matter that the internet is in a PPPoE or not..
-
Mmm, security wise it's poor.
Interesting in a 'can it work at all' sort of way though.. to me at least.

Steve
-
@aoikite said in "Poor man" home network first try:
And lastly i'm a total newbie in this kind of networks
So from such a statement why are we discussing BAD PRACTICE.. that no sane network person would ever do with someone that is new to the game.. Talk about instilling bad practice..
Yeah you can run multiple layer 3 over the same layer 2 - doesn't mean you SHOULD.. Especially when that layer 2 is the public side, etc..
Get yourself a vlan capable switch so you can correctly isolate your different networks. Even discussing how best to put together something with chewing gum and sticks that "works" is wasting everyone's time.. This isn't a topic about how can I get this to work since the network is DOWN and I need it UP with these shitty parts since the correct parts will be here tmrw, etc..
Sorry but I don't buy the "poor" excuse.. There is no excuse for doing something in a non secure ______ rigged fashion.. Use your network with the device your isp gave you until such time as you can correctly put in a different router/firewall that doesn't compromise security and isolate layer 2 traffic.
-
@stephenw10 said in "Poor man" home network first try:
Yes, the bridge mode should work. You can pass through the PPPoE connection from the DSL.
The modem should not show on the DHCP leases tab unless it's actually using DHCP which is unlikely. I imagine you set it statically. It will show in Diag > ARP though if pfSense has connected to it recently.
This is an interesting setup if it works. With the PPPoE session passed to pfSense it will have the public IP as it is terminating PPPoE. It will be using the same interface to talk to LAN clients.
The modem should not have any upstream connectivity since it does not have a public IP itself.Steve
thank you for your answers, i'll keep experimenting and see how it goes .
@johnpoz said in "Poor man" home network first try:
@aoikite said in "Poor man" home network first try:
And lastly i'm a total newbie in this kind of networks
So from such a statement why are we discussing BAD PRACTICE.. that no sane network person would ever do with someone that is new to the game.. Talk about instilling bad practice..
Yeah you can run multiple layer 3 over the same layer 2 - doesn't mean you SHOULD.. Especially when that layer 2 is the public side, etc..
Get yourself a vlan capable switch so you can correctly isolate your different networks. Even discussing how best to put together something with chewing gum and sticks that "works" is wasting everyone's time.. This isn't a topic about how can I get this to work since the network is DOWN and I need it UP with these shitty parts since the correct parts will be here tmrw, etc..
Sorry but I don't buy the "poor" excuse.. There is no excuse for doing something in a non secure ______ rigged fashion.. Use your network with the device your isp gave you until such time as you can correctly put in a different router/firewall that doesn't compromise security and isolate layer 2 traffic.
I'm sorry if i sound like a stupid person but all the terms you have used, as in layer 2 and layer 3 network are completely stranger to me, and i came here because i'm a person who "learn by breaking stuff and practicing", this is in no way an "optimal setup nor an "oh snap 0$ build you can do at home" kind of project, just a learning experimenting project, and the "poor excuse" is not there an excuse to not buy new hardware at all, new hardware will be used in the future project in 2-3 months when i'll wanna install afully functional network.
Maybe i failed to express that this is just a test subject, and not a permanent solution for a network at home, i'm sorry about that too.
Networking was never my forte in the IT side of things so i came here with the mindset of learning by doing, and if i'm doing something wrong, i would be told that is wrong in the way i'm doing it, learn from it keep on improving.
I did state in my first post that this is just a prototype and theorical project, done with the "junk" i have to see if it can be done, fiddling , reconfiguring and ultimately maybe killing everything is part of the fun fror it as i am learning how to do this in its good and bad sides.
I know that for a network advanced used like you, all of this seems like a waste of time, and getting the smart router and doing the Vlan thingy and call it a day would be time saving for everyone, but i would have learned zero things and for future installs, i would be in the same state of wondering how does it work, and why it is not working.
And in the end sorry if my post seems like a complete waste of time, i joined the community here as a person who wants to learn that's all.
-
This setup (if it works) is bad because your WAN and LAN traffic are traveling over the same connection and there is no separation between them such as VLANs which would create 2 layer 2 segments.
https://en.wikipedia.org/wiki/OSI_modelThat said it could be worse, at least one connection is PPPoE.
If this is just for your own use/experimentation then just be aware of that issue.
Steve
-
@stephenw10 said in "Poor man" home network first try:
This setup (if it works) is bad because your WAN and LAN traffic are traveling over the same connection and there is no separation between them such as VLANs which would create 2 layer 2 segments.
https://en.wikipedia.org/wiki/OSI_modelThat said it could be worse, at least one connection is PPPoE.
If this is just for your own use/experimentation then just be aware of that issue.
Steve
thanks for the article.
This is just a prototype for experimentation, i live in an appartment so it does not really need a network, i just felt like experimenting with what i have to get accustomed to the different things in it and what can be done with it, this is in no way a "red alert" critical thing, but a hobby instead.
i'm doing this to learn the basics and function of pfsense and networking in general since i'm planning to create a full fledged network in the new house for different devices with 2+ nics instead to not use this vlan but it's not the time to talk about hardware really now since it's too early ^^
-
Well break stuff and fix it.

Just be aware that what you're doing is not normal or recommended in a anyway. You will see things that you would not expect to in a correct network setup.
Steve
-
@stephenw10 said in "Poor man" home network first try:
Well break stuff and fix it.

Just be aware that what you're doing is not normal or recommended in a anyway. You will see things that you would not expect to in a correct network setup.
Steve
since you both said that going through the same ethernet port is a bad idea, i started exploring other solutions.
i'm exploring the idea of using the built-in wifi to act as either the lan or the wan part of this network but i doubt this will be functional in any way possible, i'm googling if it is possible in the first place lol.
The other option is somehow getting a second ethernet on this laptop (express34 or usb should suffice)
Any of these methods would fix the security problems right ?
P.S: the future setup will obligatory have a switch and access point to not overcomplicate stuff and for easy management i guess.
-
Yes, any of those options would separate the WAN and LAN of different layer 2 segments.
Wifi support in FreeBSD and hence pfSense is not great. But it may be possible if that is an older device.
What wifi hardware do you have the laptop exactly?Try running
pciconf -lvto see the exact pci vedot and device ID.Steve