NAT is enforced on my pfSense in Azure
-
I have setup pfSense on one end (Azure) of a site to site VPN. From my local network I can reach the other hosts on the Azure side, however when traffic flows through pfSense, it is NATed and the IP seen by the hosts in Azure is the pfSense LAN IP as source.
This is not what I expect to happen. However, when I Disable the NAT in pfSense, it simply drops the traffic and does not forward it to my hosts.
Here's more context:
Local network: 192.168.8.0/24
Azure network: 10.0.5.0/24
pfSense LAN: 10.0.5.10
MyPC: 192.168.8.5
Azure host: 10.0.5.22Tunnel established between both networks.
If traffic is initiated from host in Azure network to host in my local network, the address is not NATed. However, when traffic is initiated from MyPC to host in Azure, this is the source IP address 10.0.5.10 seen by the Azure Host (10.0.5.22).
Looked into Outbound NAT in pfSense, tried disabling it. On disabling it, it turns out no traffic makes it to the Azure host, it is just dropped by PfSense.
Does anyone know a fix for this?
-
Does no one have an idea how to stop NAT and prevent my traffic from getting dropped/ disappearing into oblivion in pfSense?
If the traffic arrives in pfSense via the VPN tunnel, why does it have to be NATed before leaving pfSense?
I can see the traffic arriving in pfSense via tcpdump, and if I enable NAT it arrives at the destination host. But if I disable NAT, it arrives in pfSense but never makes it to the destination host.
-
Pfsense is only going to do what you tell it to do... If you setup outbound nat to nat to your vpn interface that that is what will happen.. Post your outbound nat listings.
Did you change it to hybrid or manual? Or leave it on auto?
Your going to have to give more details of how you setup this tunnel... Is it site to site? What are you using for the tunnel network? Guessing this is a openvpn?
-
It is an IPSec tunnel.
All the rules were auto created by pfSense using Hybrid Outbound NAT rule generation (Automatic Outbound NAT + rules below)
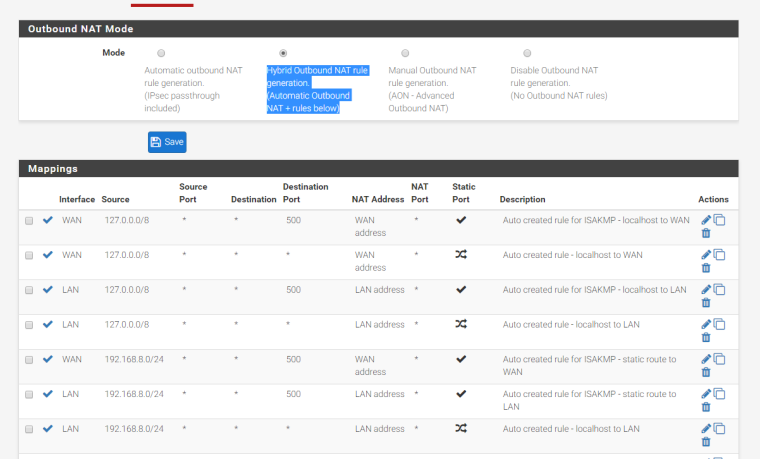
When Outbound NAT (Automatic, Hybrid, Manual) is enabled, in the Diagnostics > States
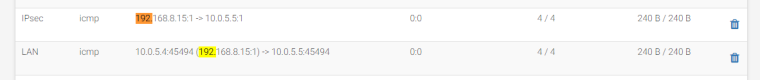
When I Disable Outbound NAT rule generation. (No Outbound NAT rules), Traffic arrives on the pfSense, but it never leaves (assumption, it gets dropped).
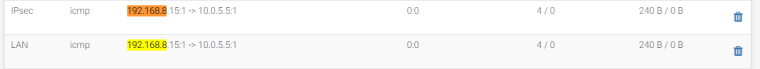
As I mentioned earlier, it is a Site-to-Site VPN tunnel, one end is our Office (Fortigate) and the other end is Azure (pfSense).
My goal is to have traffic reach my host without it being NATed in pfSense.
-
It is probably not being dropped by pfSense but by Azure. Azure will have to be told to send the traffic that is destined for your local network to pfSense for processing. There might also be things you have to enable in Azure. In AWS there are settings like "source/dest check" that have to be disabled so the instance can receive traffic that is not sourced from nor destined to itself.
-
I don't see why Azure should drop the traffic. A Forti setup with the same Azure configuration (routing) has no issues. Traffic goes through from source to destination with no issues.
Appears pfSense is not sure how to reach the host which it shares the same network as. Is there a way to see the traffic that arrives through the tunnel attempt to exit the pfSense and what happens after in Azure side?
-
@steinermarshall I have exactly the same problem with Azure. Have you been able to advance the solution?
-
Enabeling IP-forwarding under IP-configuration for the pfSense Nic in Azure does the trick. Also remember to associate the relevant subnets with the routing table.
-
@ralftar Thank you very much. This works for me!