SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui
-
@jimp said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
/var/etc/nginx-webConfigurator.conf
Just checked /var/etc/nginx-webConfigurator.conf on one of the 4 PF Appliances, it appears that it ONLY set up for HTTP even though we have HTTPS enabled right now, so something is not updating the actual configuration files when changes are made in the GUI. So this might be some other issue, that is adding to this mess.
server {
listen 80;
listen [::]:80;
However the GUI says HTTPS is enabled on port 443, so I am expecting that it should be listening on port 443, but the file is not reflecting this change, and yes, I did commit the change in the gui, and restart webConfiguratior via SSH.Also tried the same process on another Appliance and getting the same thing. So wonder if some update script within the CGI of the gui is broke? maybe?
We might be in need of a rebuild I am thinking....sigh
-
Are you sure there isn't another block in there? It will have port 80 declared if you have the redirect on that sends users from 80->443
-
We are using two management VMs, which have nothing but Windows Defender (and it is turned OFF, and NO Windows Firewall.) to rule out AV on the laptops. We are still seeing HTTPS issues, but as said with @jimp above, we are also seeing that configurations files are differing than what the GUI is reporting.
-
Also if you want to bump it, use options 16 then 11 from the ssh/console shell and that will force it to reconfigure the GUI and PHP.
-
Just tried that, and I now can confirm that /var/etc/nginx-webConfigurator.conf is not being updated....the files time stamp has not changed since 10/1/2018, and I JUST made changes today via the GUI so the time stamp should have changed if it was touched by a CGI script or manually....so I think something is broke in our appliances.
This is the entire file.....nothing with port 443, even though the GUI says port 443 is being used.
nginx configuration file
pid /var/run/nginx-webConfigurator.pid;
user root wheel;
worker_processes 2;
error_log syslog:server=unix:/var/run/log,facility=local5;events {
worker_connections 1024;
}http {
include /usr/local/etc/nginx/mime.types;
default_type application/octet-stream;
add_header X-Frame-Options SAMEORIGIN;
server_tokens off;sendfile on; access_log syslog:server=unix:/var/run/log,facility=local5 combined; keepalive_timeout 75; server { listen 80; listen [::]:80; client_max_body_size 200m; gzip on; gzip_types text/plain text/css text/javascript application/x-javascript text/xml application/xml application/xml+rss application/json; root "/usr/local/www/"; location / { index index.php index.html index.htm; } location ~ \.inc$ { deny all; return 403; } location ~ \.php$ { try_files $uri =404; # This line closes a potential security hole # ensuring users can't execute uploaded files # see: http://forum.nginx.org/read.php?2,88845,page=3 fastcgi_pass unix:/var/run/php-fpm.socket; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; # Fix httpoxy - https://httpoxy.org/#fix-now fastcgi_param HTTP_PROXY ""; fastcgi_read_timeout 180; include /usr/local/etc/nginx/fastcgi_params; } location ~ (^/status$) { allow 127.0.0.1; deny all; fastcgi_pass unix:/var/run/php-fpm.socket; fastcgi_index index.php; fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name; # Fix httpoxy - https://httpoxy.org/#fix-now fastcgi_param HTTP_PROXY ""; fastcgi_read_timeout 360; include /usr/local/etc/nginx/fastcgi_params; } }}
-
The formatting on that got messed up. Maybe try attaching it as a file.
Also, what do you have in your config.xml for the GUI? It would be under
<system>and then<webgui>.Would look something like this:
<webgui> <protocol>https</protocol> <loginautocomplete></loginautocomplete> <ssl-certref>5b7777344d771</ssl-certref> <dashboardcolumns>2</dashboardcolumns> <port></port> <max_procs>2</max_procs> <nodnsrebindcheck></nodnsrebindcheck> <nohttpreferercheck></nohttpreferercheck> <authmode>Google Cloud Secure LDAP</authmode> <disablehttpredirect></disablehttpredirect> </webgui> -
Thanks all! I think at this point our PF Appliances are so messed up that it is pointless at this point to keep beating a dead horse. I am going to take down our secondary PF Appliances, and rebuild them, see if all works as it should, and if it does swing traffic to the the secondary, then rebuild the primary PF appliances. We only have 4 (2 Primary and 2 Secondary), so it shouldn't take to long, and I have backups of the configurations so that should speed up rebuilding.
-
Well if you throw your hands up in the air when we're finally getting closer to finding out what's wrong, it'll never be fixed, if it does turn out to be a bug.
I did find one issue that wouldn't have triggered a restart when toggling some of the checkboxes that need an nginx restart (like the GUI redirect), but it isn't quite what you are hitting.
-
Can't post our config.xml file as it errors on here as "Detected Spam" and won't post it.
-
I can fix that, just need to spam the thumbs up on your posts so Akismet will pass you through.
Also don't need the whole config.xml just the
<webgui></webgui>tags and what's inside. -
Should be good to post now.
-
Also, FYI, clicking Save on system_advanced_admin.php will not trigger a rewrite of the nginx configuration unless something changed that requires it. For example, changing the web server port, protocol, etc. So opening the page and clicking save won't help, but if you switch the port to something else (say, 4433) it would restart with the new settings, then you can change it back. But doing option 11 from the console should always rewrite the nginx config from the contents of config.xml and then restart the web server.
-
I have changed the port to 4433, switch from http to https and save : the webgui is accessible via https on port 4433, from there I have explicitly set the port to 443 and again : get error SSL_ERROR_NO_CYPHER_OVERLAP.
I am staying on 4433 for now...
-
@xenicle said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
I have changed the port to 4433, switch from http to https and save : the webgui is accessible via https on port 4433, from there I have explicitly set the port to 443 and again : get error SSL_ERROR_NO_CYPHER_OVERLAP.
I am staying on 4433 for now...
You must have port 443 taken over by some other daemon or NAT that isn't the GUI.
-
I might have some more insight regarding the issue.
I was playing around in pfsense v2.4.4 and I've somehow ran into the same/similar issue again

When I access
192.168.1.1(pfsense box) over HTTPS I get theSSL_ERROR_NO_CYPHER_OVERLAPerror, however when I got topfsense.localdomain(HTTPS or HTTP - which redirects to HTTPS) it works fine.
Maybe this means the SSL certificate isn't bound to the IP but the domain name only?Does this mean pfsense was setup incorrectly by the user (e.g. me)? But that doesn't explain why it initially worked

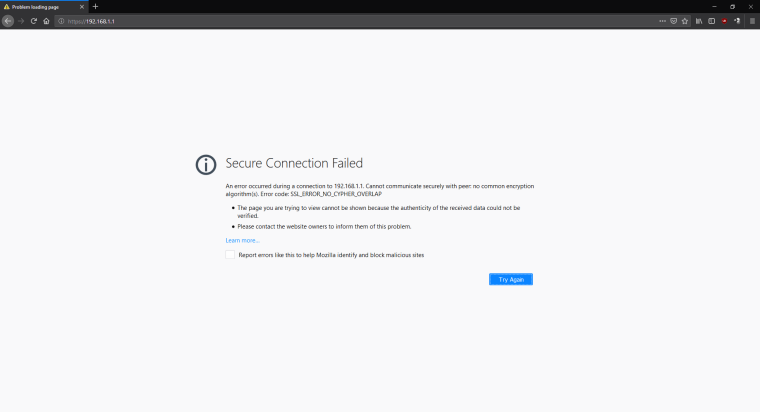
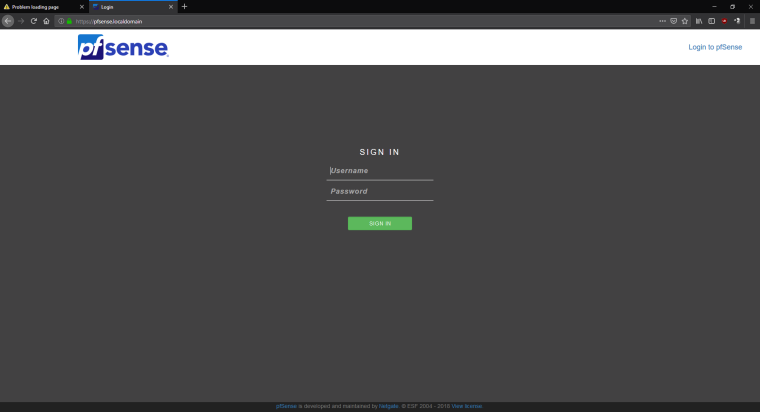
-
Are you certain your workstation is hitting 192.168.1.1 when going to pfsense.localdomain? Try to open a command prompt and ping pfsense.localdomain, see what it's actually hitting.
-
I ran into similar trouble recently. I responded to an old post on the forum as to a solution.
Have you tried this solution? https://forum.netgate.com/topic/123072/ntopng-https-redirect-protocol-error-after-configuration-in-version-2-4-1/2
EDIT: Certificate attributes > Alternative Names could be the issue as to why you can connect via FQDN and not the IP.
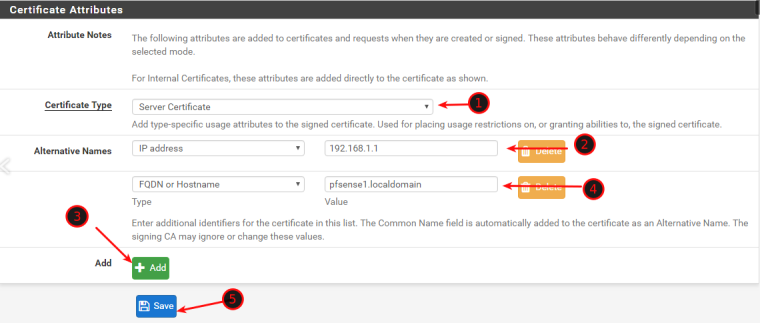
-
@jimp pfsense.localdomain is definitely resolving to 192.168.1.1 (in my case, as per above images)
-
@crbon said in SSL_ERROR_NO_CYPHER_OVERLAP when trying to connect to webgui:
@jimp pfsense.localdomain is definitely resolving to 192.168.1.1 (in my case, as per above images)
The images don't prove that, however. Try a ping and see what happens. Maybe your computer is resolving that hostname to the WAN IP address, for example, or another local interface. It could explain the discrepancy.
A mismatched SAN/CN wouldn't have anything to do with the cipher. It would still work, but complain that the certificate didn't match the host. It would not affect encryption.
-
@jimp Sorry I wasn't clear. I just did ping pfsense.localdomain and it does resolve to the 192.168.1.1 address.
Windows 10 has crapped itself, I cannot do windows search to get the snipping tool to show it