VPN IPsec site_to_site with Cisco router issue
-
Hello everyone,
I'm trying to establish a VPN connection between pfSense firewall and cisco router 2811 series.
Infrastructure on pfSense side:
#1.Dedicated server running ubuntu 18.04 (The firewall allows traffic by default).
#2./29 subnet public IPs.
#3.VirtualBox installed on ubuntu running two virtual machine:
A-->pfSense firewall with two vNIC, one for the WAN connection with public IP 23.238.115.213, and the other for LAN network with IP 192.168.90.1/24.
B-->Windows Server 2016 (Windows firewall is of) with two vNIC, one take the public IP 23.238.115.214/29, and the other configured as local network and take it's IP through DHCP 192.168.90.10/24.
############################
Infrastructure on Cisco side:
Peer public ip: 196.29.171.33
remote ip: 196.29.171.6
############################
VPN Configuration:
The peer using NAT over IPsec to NAT it's private IP to 196.29.171.6.
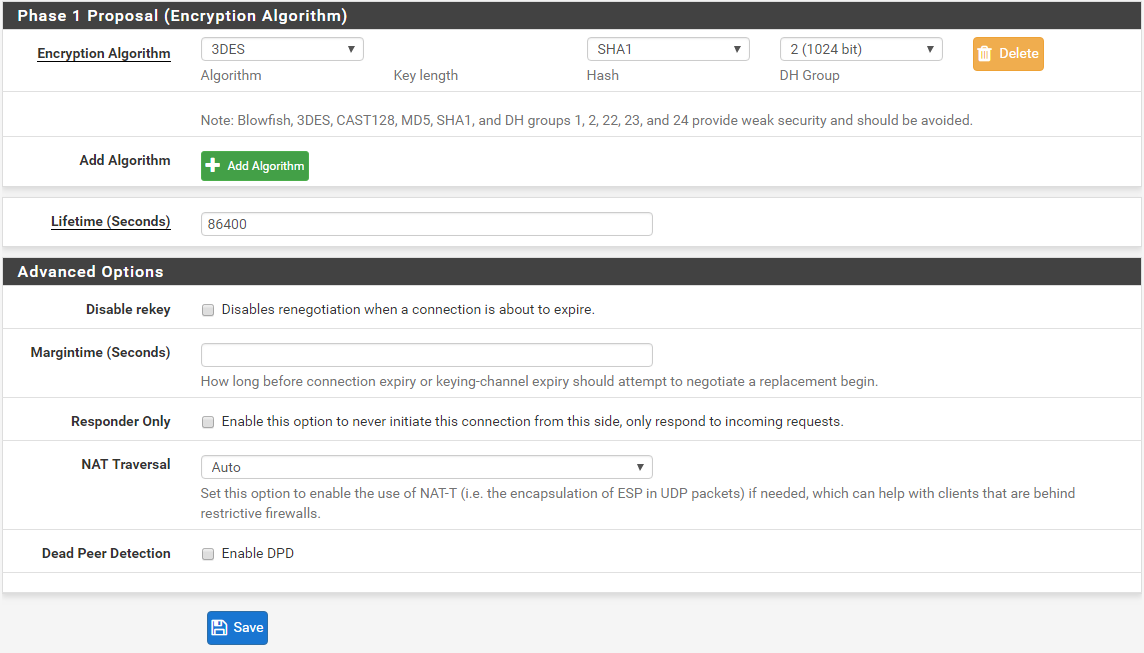
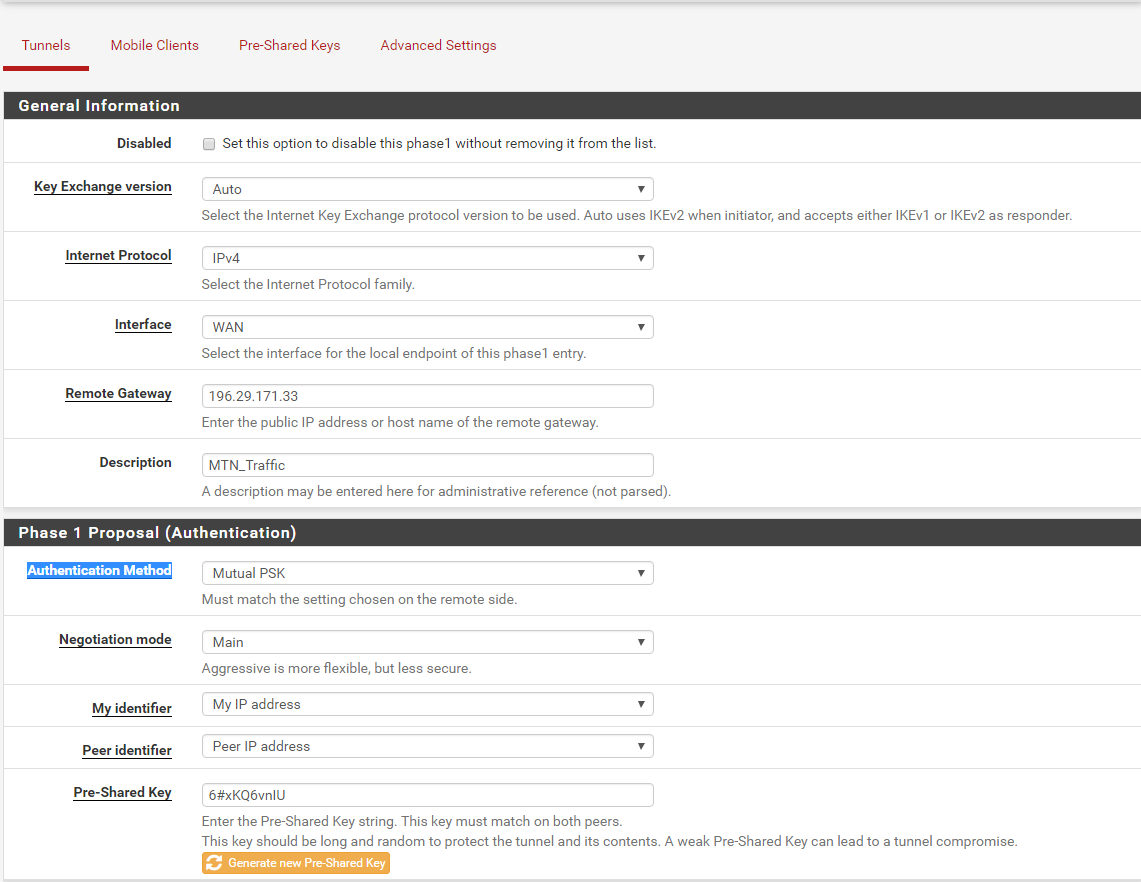
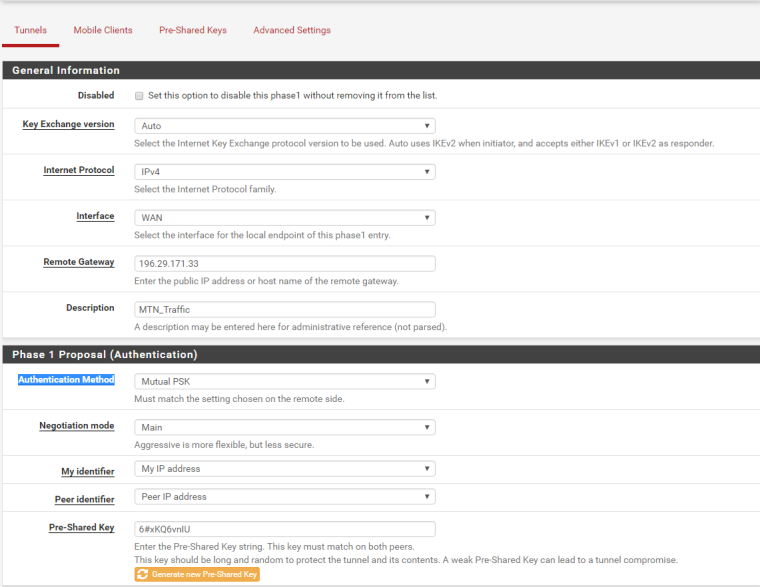
Phase 1 configuration:
Peer IP: 196.29.171.33
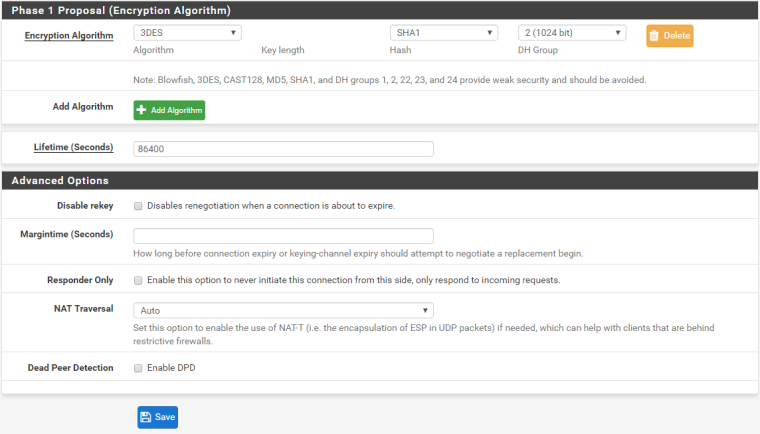
Encryption Algorithm: 3DES.
Hashing: Sha1
Authentication Method: PSK
DH: Group 2
Lifetime: 86400
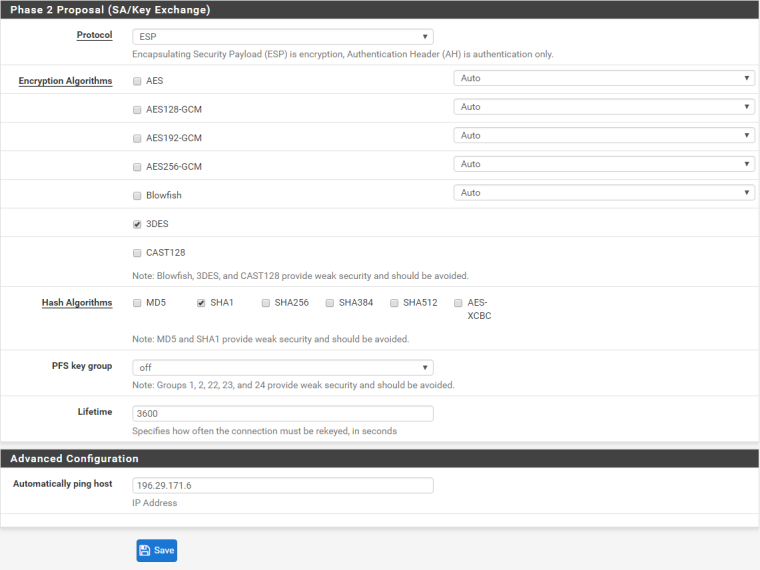
Phase Two configuration:
Traffic IP: 196.29.171.6.
Transform-set: 3DES-Sha1 esp-3des esp-sha-hmac
Below my configuration:
#############################
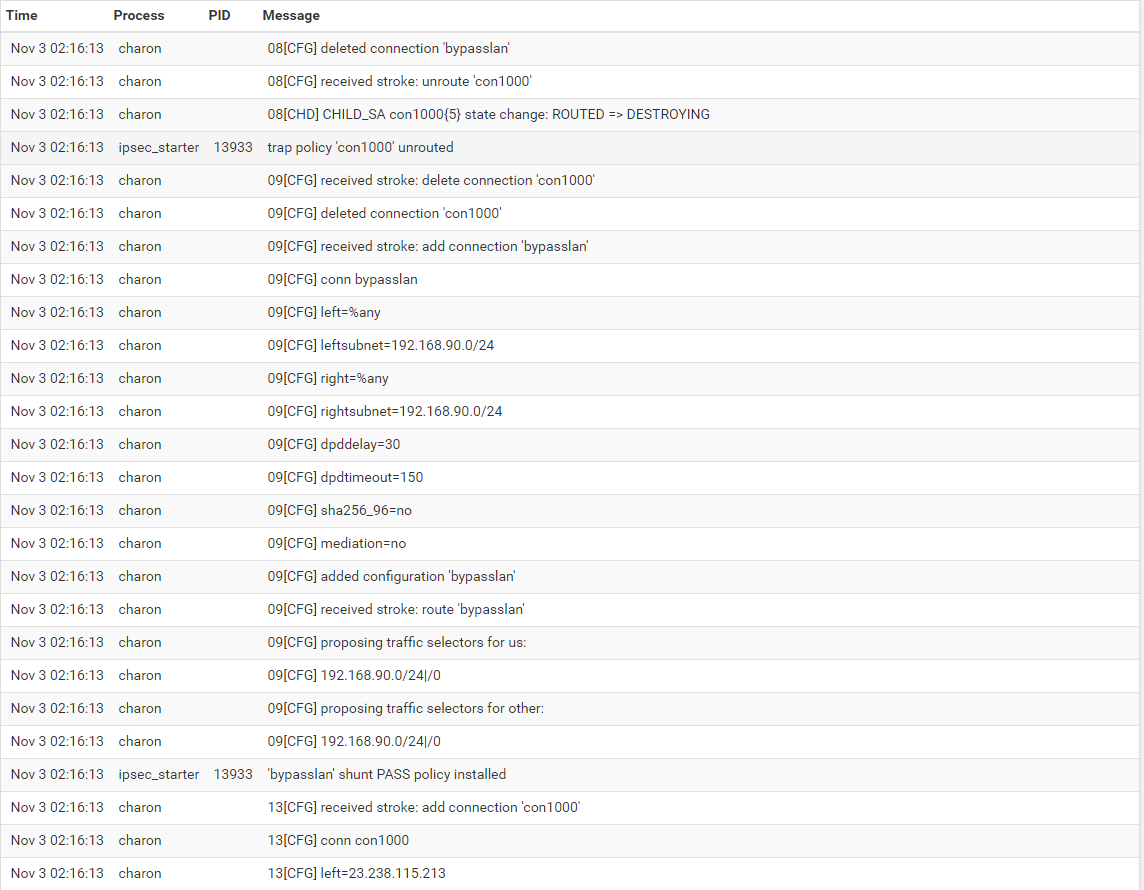
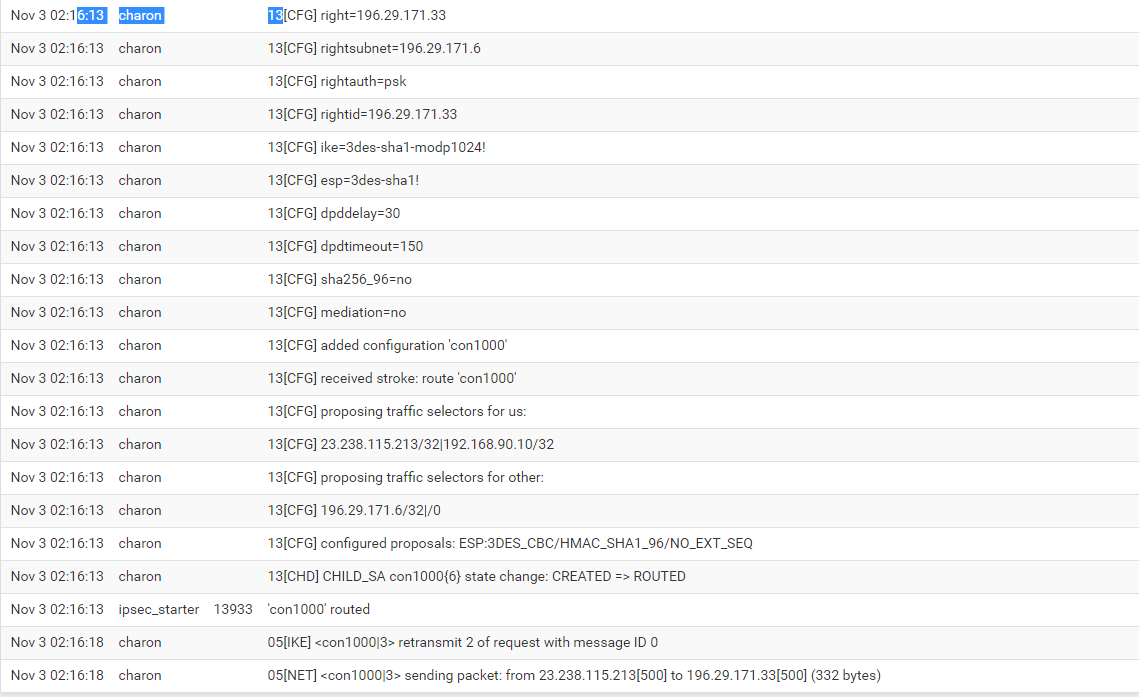
My log file shows:
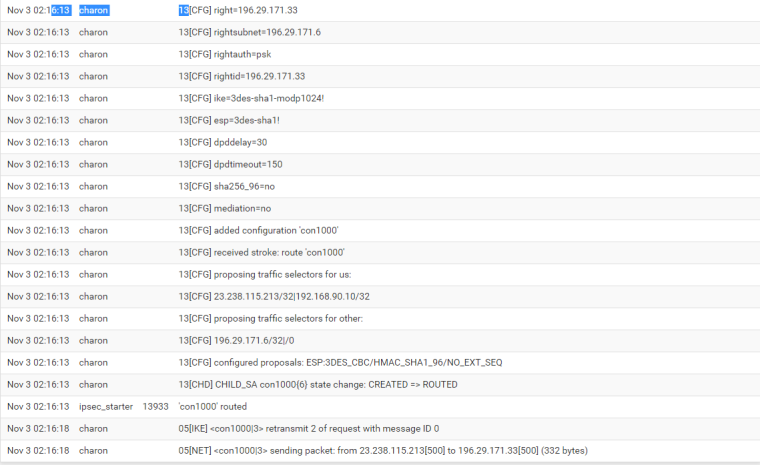
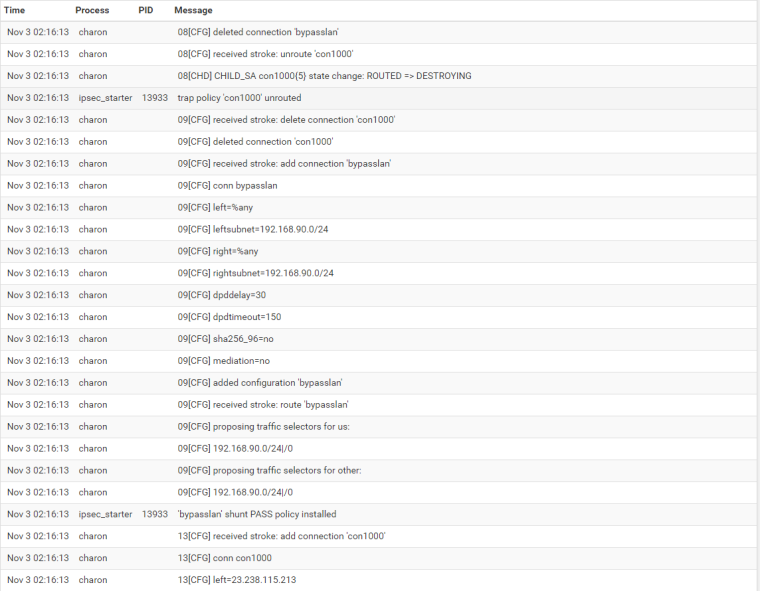
Thanks alot.
-
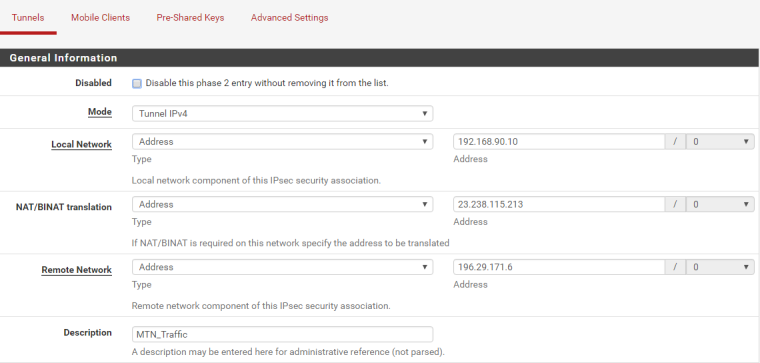
Phase Two configuration:
-
For Key Exchange version Auto uses IKEv2 when initiator, and accepts either IKEv1 or IKEv2 as responder. If Cisco side does not support Auto but requires Key Exchange version to be specified then select IKEv1 or IKEv2 (preferably if cisco supports).
In Phase 2 you have selected 192.168.90.10 (Windows Server 2016) as Local Network, If you want any device in LAN can send or accept IPsec traffic then select LAN subnet as Local Network.
Make certain that at both sides Pahe 1 and Phase 2 Proposals (Encryption Algorithms, Hash Algorithms, groups and Life Times) are equal.
Firewall rules must exist (Firewall > Rules, IPsec tab) that govern traffic allowed to pass on the VPN tunnels. At a minimum, an allow all rule (Pass protocol any, src host any, dst host any) is needed. That said, more restrictive rules are better to enforce proper network security protocols.
-
@e066377 Thanks for the response.
I did what you say and i still there, not working.Thanks for your help bro.
-
C2811 is not Cisco ASA but try to follow this guide:
IPsec between pfSense and Cisco ASA: Setup cross vendor IPsec VPN sometimes is tricky, due differences in protocols implementation. There are several important nuances here:
- Do not use auto-negotiation at all. Set certain parameters manually. Usually it is aes128-sha1 and pfsgroup 2 or 5
- Make sure P2 settings describes exactly the same networks, because ASA demands IPsecProxyID has to be the same on both devices, one is composed from P2 networks, so that they must be the same. E.g. local:10.0.0.0/24 remote:10.1.0.0/24 on one side and local:10.1.0.0/16 remote:10.0.0.0/24 on another is wrong, even formally network connectivity is possible for them in some way.
- Cisco ASA uses list of policies for matching possible policy. This might make additional problem. Set certain policy on top of list, e.g. esp-aes128-sha1 pfsgroup 2 has to have 1st sequence number.