Setup for trunk via OPT1 port of SG-3100
-
Hello
I'd like some help to configure a trunk port on my sg-3100. I have read a ton of the guides here / watched netgate youtube videos on the subject but still have a few lingering questions.
-
I setup lan 1- 4 as discrete ports ( vlan 4081 : lan, vlan 4082 : iot, vlan 4083 guest, vlan 4084 : fios dmz). If I intend to trunk it all to a downstream switch ( unifi 24 port poe switch), is there any benefit to setting them up as discrete vlans ?
-
noob question: since I am using a trunk to the unifi switch, all connections are now plugged into ports on the unifi switch, nothing directly on any of the sg-3100 lan ports, correct?
-
how do i setup the opt1 port as a trunk to the switch for all 4 discrete lan ports? I know have to assign the vlans to the mvnet0 interface ( instead of mvneta1). then what? setup dhcp for opt1?
I have zilch background in this but willing to learn. some guidance will be appreciated.
-
-
Anyone? Will appreciate some help.
-
What are you trying to do? Your wanting to add opt1 to an existing vlan that you have already put on port in your switch ports?
Doesn't work that way.. You can put multiple ports in the switch on the same vlan.. That is the point of the switch ports. But opt1 would not be part of any of those vlans without creating a bridge - which is not a good idea when you have switch ports for that.
You can for sure run different vlans on opt1.. If that is what your asking.
-
@johnpoz said in Setup for trunk via OPT1 port of SG-3100:
Your wanting to add opt1 to an existing vlan that you have already put on port in your switch ports?
Hi johnpoz - I am not trying to do that. I am looking to :
-
confugre LAN 1 - 4 as discrete ports
-
use the opt1 as a trunk to my donwstream unifi siwtch.
I am not sure how to setup the trunk. I know i have to assign the vlans to mvneta0 .
-
-
There is no trunk function - you would just add your vlans to the physical port.
So create your vlans - put them on the opt1 interface. You would then configure the port of your switch to be "trunk"... IE use the same vlan IDs you used when you created the vlans on pfsense as tagged.
If you want help on how to do that on the unifi switches you prob get better help on their forums. They are quite active... And I know for sure there are plenty of people over there using pfsense as well. But there is really nothing to do special on pfsense other than create the vlans and add them to your physical interface. All the "trunking" is done on your switch.. I can show you how to do it in on cisco or other switches that have laying about - but don't have any unifi switches to use as example... I do have AP..
Are you going to plug the AP directly into this port and want to have multiple vlans per different SSIDs? If so can for sure show you examples of that..
-
Like this ?
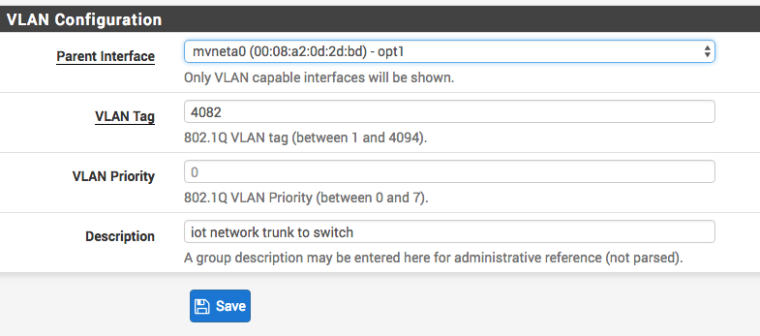
My question relates to what to do with the opt1 port - enable it, assign dhcp server ?
-
You don't have to put any IPs or anything on it unless you want untagged native traffic on it - ie not tagged vlan.
-
So just enable the opt1 port ? I dont have any questions about how to setup things on the unifi side.
-
I would assume you would need to enable it if you want to put vlans on it yeah ;) Just use none for ipv4 and ipv6 for the interface.
I would assume the interface doesn't get turned on unless enabled - but I always run native on my interfaces along with vlans.
-
Got it. Thank you!
And on the pfsense switch side of things, does this look ok to you? I will like devices on the lan to talk to the others but not vice versa.
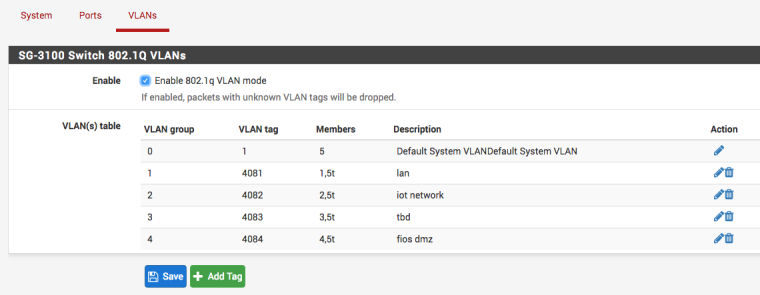
-
No it doesn't since you said you were going to put 4082 on opt1.. But you have it listed in your switch.
-
I am lost a bit. So there is no need to enable 802.1q ? What should it look like then?
-
Dude if your running vlan 4082 on your opt1 interface how are you also going to run that on your switch? Are you planning on bridging opt1 into your switch - WHY?
We went over this in my first post!
-
johnpoz - I have no networking background - just learning here. will appreciate if you point me in the right direction. Some guides I read did something like this whilst sending their traffic to the unifi switch.
-
Opt1 is a normal interface - its is not a switch port... The only way to connect a interface to another interface or switch is to create a BRIDGE... Which make no sense for your scenario..
You can use say vlan 4080 on opt1 if you want... But you can not use vlan 4082 on opt1 and on your switch at the same time... Without creating a bridge... Which WHY would you want/need to do that??
How many different networks/vlans do you want or need? Why does opt1 need to be in 4082? When your other vlans only have 1 port... If you need multiple ports in some specific vlan on pfsense device then use switch ports for those vlans. And your vlan where you only need 1 port since your going to have your other devices in your switch then use the opt1 interface for that..
I would be happy to explain the best way to do this if had some clue to what your actually wanting to accomplish... Can you draw up your network and how you want everything connected and we can discuss the best way to accomplish that... And if running a bridge on pfsense is the best way... I will freaking donate 10$ to your favorite charity ;)
-
johnpoz:
I went back to reassess everything. I think i'd like to take a different approach now due to your input. heres what I'd like to do on the sg-3100.
- WAN
- OPT1 ( use for management interface).
- LAN1 ( discrete port : main home network)
- vlan 10 - hardwired items
- vlan 11 ( wireless clients)
- LAN2 (discrete port with : fios)
- vlan 20 all fios boxes
- LAN3 (discrete port for iot)
- vlan 30 ( secure iot devices )
- vlan 31 (insecure iot devices)
- LAN4 (discrete port :dmz)
- vlan40 ( guest network)
So i will have a separate connection on each of these ports to my unifi switch with similar vlans setup on that end.
My qeustions:
-
is the above a good setup on the sg-3100 ?
-
lf it is, can you guide on exactly how to setup things on /interfaces/switches /vlans page? what is tagged and what is not tagged ?
-
will it be possible to get devices on one network to talk to others - like home wireless clients (172.20.11.0/24) browsing stuff on the fios boxes on 172.20.20.0/24 ? What are the rules to enable that?
this should get me to where i wanted to go in the first place. jsut got mixed up trying to send everything down one pipe. thx
-
So you want to run all of these ports to your switch.. So you are using them as router interfaces and not switch ports. Why would you get the 3100 and not a model with discrete interfaces..
How much traffic are you using between these vlans... Why are you breaking them out?
Why are you putting your main home network devices on 2 vlans? Curious.
Secure iot and insecure iot? I doubt there is such a thing as secure iot ;) hehehehe
What exactly are you going to be dongi witht he opt1 interface? Your interfaces with only 1 vlan on them do not need to be tagged. The interfaces with 2, 1 could be tagged the other could be native untagged.
As to that being a good setup for the 3100.. Off the top I would say no to be honest... The point of the 3100 is comes with switch ports.. And you don't seem to be using for that - you want to seem to leverage them all for uplinks..
As to browsing from 1 vlan to another.. Sure you can allow for access... Simple rule to allow the port you want to allow.. But "browsing" if you mean discovery or a broadcast then no.. They are 2 different layer 2 networks. So if you want to say use SSDP to find a box on another vlan then no its not going to work... Or like windows network neighborhood discovery shit.. No doesn't work like that. You can allow for some multicast discover with avahi package..
But if you have devices that "require" layer 2 discovery you might want to determine if easier to just put them on the same layer 2.
Example of this... My printer - for airprint to work it is easier for it to be on the same layer 2 as devices that will use airprint to print to it. This is my secure wireless vlan.. Which is a eap-tls secured network.. My wired devices on my normal lan and such that need to print can just point to the printers IP they do not need to use discovery to find the printer, etc. But my tablet my phones and such its just easier for them to use the airprint discovery.
-
hello jonpoz
You are right, I dont need to split them up like that. I was following the guide in the video here : https://www.youtube.com/watch?time_continue=1&v=NgRy14rYhV8
Regarding devices talking to each other across subnets, I have:
- I will need access to the fios dvr from devices on the home lan but dont want fios to be on the same subnet.
- some of my iot designated devices ( nest hello ) will need access to my lan.
other than that, nothing complex. The netagte video I linked to got me confused about how to setup the ports. If the setup I am showing is not ideal, what do you recommend ? My goal is to simply create several vlans to segment off the traffic as shown above then use my unifi switch to connect all devices downstream. Thanks
-
You can split them up if you NEED too... But unclear on your actual NEED?
Sure its normally a good idea to isolate stuff like DVRs, TVs, etc.. But you need to understand the discovery or method of access if you want to access them from another network. You can for sure access them via a tcp or udp port from another network. But if your client is going to use some sort of broadcast or multicast discovery protocol your going to have problems - just so we are clear.
Why does your nest hello need access to your lan? I wouldn't think nest hello creates any sort of unsolicited access to something on your lan.. But I could see your lan devices access it. So you can view the video when someone rings the bell.. Do you have some NVR or something on your lan that the doorbell will be writing video too?
Are you going to connect devices directly to switch ports? Or just going to run all the ports to your switch? The point of the switch ports is more to leverage them for devices to directly connect to vs uplinking to a switch for vlans.. You could put say a couple of them in a lagg and use that as uplink to your switch.. Or depending on the amount of devices and bandwidth requirements between vlans you could just put all your vlans on 1 of them as uplink and put the other ports on vlans for devices directly connected that you want on vlan vs connecting to your switch.
If your only going to connect switch ports to pfsense, unless they have some high bandwidth requirements between the vlans doesn't seem optimal to use all of the switch ports as uplinks. Keep in mind that their is only 2.5gig uplink from the switch ports to the routing functions of pfsense..
-
@johnpoz said in Setup for trunk via OPT1 port of SG-3100:
But I could see your lan devices access it. So you can view the video when someone rings the bell..
Yep this is what I meant - lan devices accessing clients on the other subnets ( phone to nest hello, phone to fios dvr ).
My need is just to segment out my network into the parts below and put in appropriate rules, depending on which two vlans, to limit access .
Again, I got confused with that video because I assumed i had to setup vlans by using the 802.1q setup as shown. Otherwise my needs are pretty simple!
- lan / wired client
- lan wireless clients ( will do this with unifi ap )
- fios
- iot "secure"!
- iot "insecure"!
- guest wireless
Thats as complex as it gets! Maybe you can help me understand what was being done in that video and how it does not apply to what I am looking for .... thx again!!