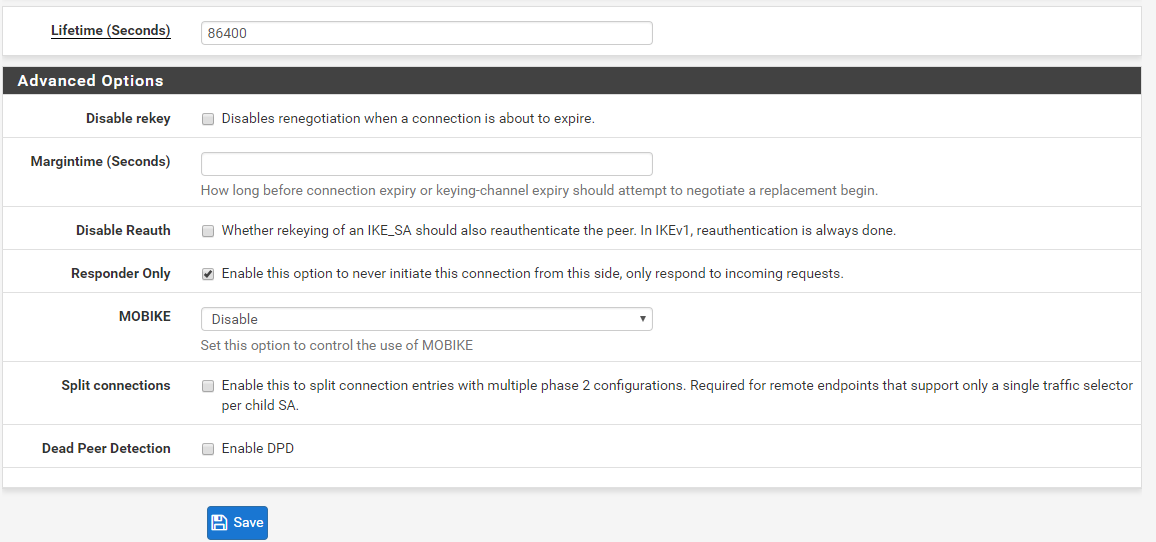
IPSec VTI to EdgeRouter
-
Hey there!
I'm trying to set up an IPSec VTI To EdgeRouter and I'm having some trouble.
I've read through:
https://forum.netgate.com/topic/132970/ipsec-vti-tunnels
https://www.reddit.com/r/PFSENSE/comments/9gqy27/pfsense_244_rc_ipsecvti_tunnel_to_edgerouter_lite/
https://community.ubnt.com/t5/EdgeRouter/No-traffic-between-VTI-based-IPsec-pfSense-amp-EdgeRouter-4/m-p/2550383And have installed the latest update to ensure the 0.0.0.0/0 route gets passed, but it seems the traffic from the VTI tunnel is not coming in on the ipsec6000 interface, but instead on the enc0 interface.
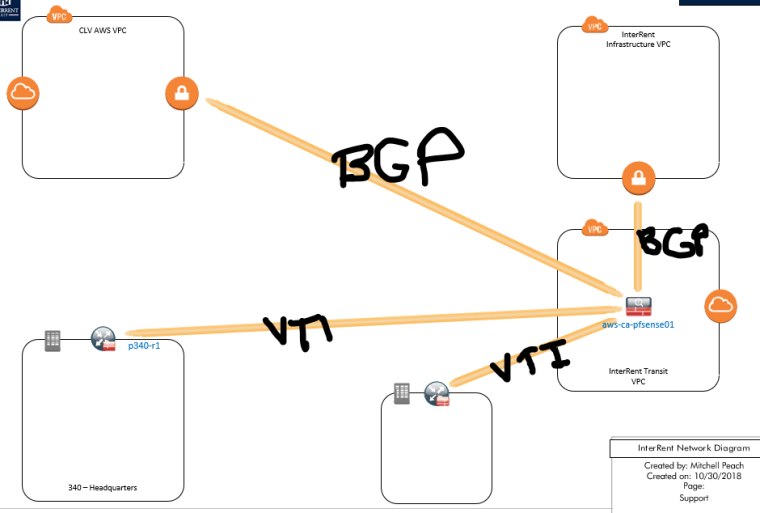
I have two VPNs to two different AWS VPCs using BGP and I'm trying to set up the router to use VTI to the pfSense. The following quick diagram is the network:
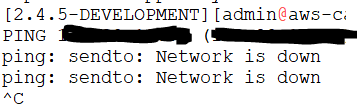
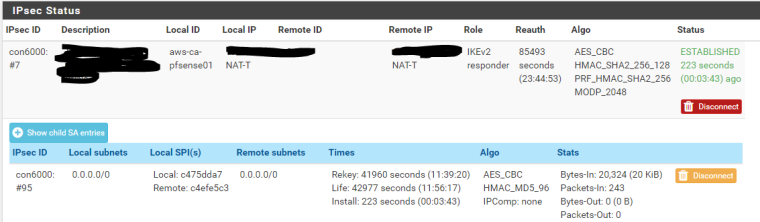
The tunnel has come up just fine on both sides and I can see traffic coming from the EdgeRouter, but I cannot get traffic to return from the pfSense. The pfSense when pinging the router states "sendto: Network is down".
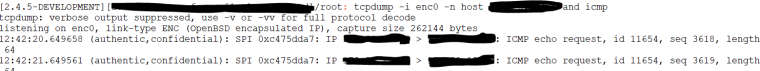
Packet Cap on enc0 while pinging from router - the filter is for the firewall address, the packets are router > firewall:
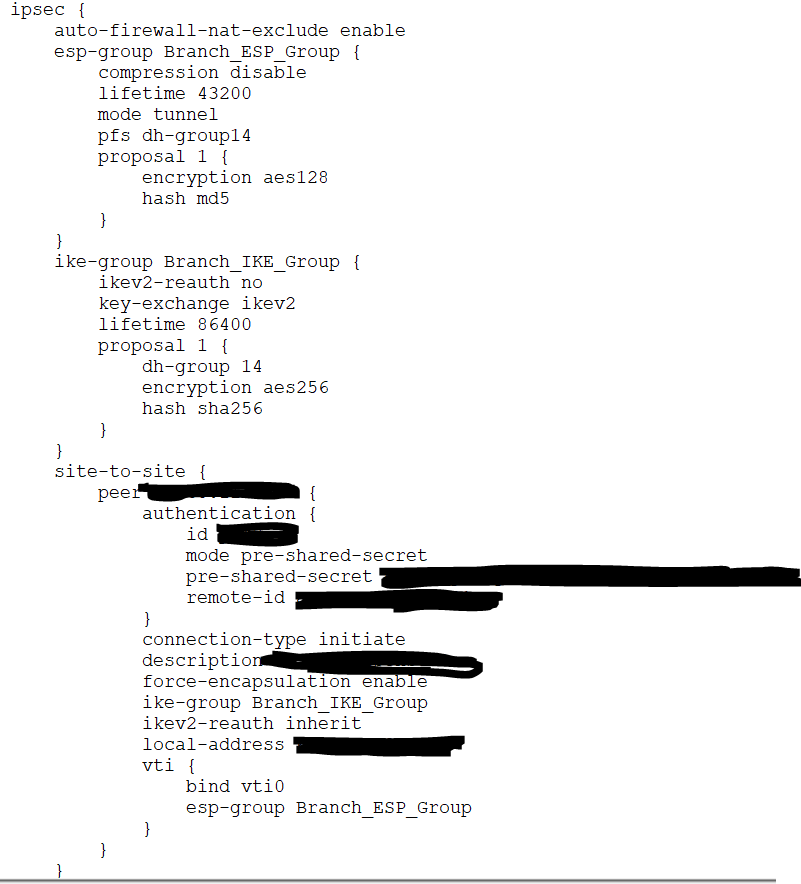
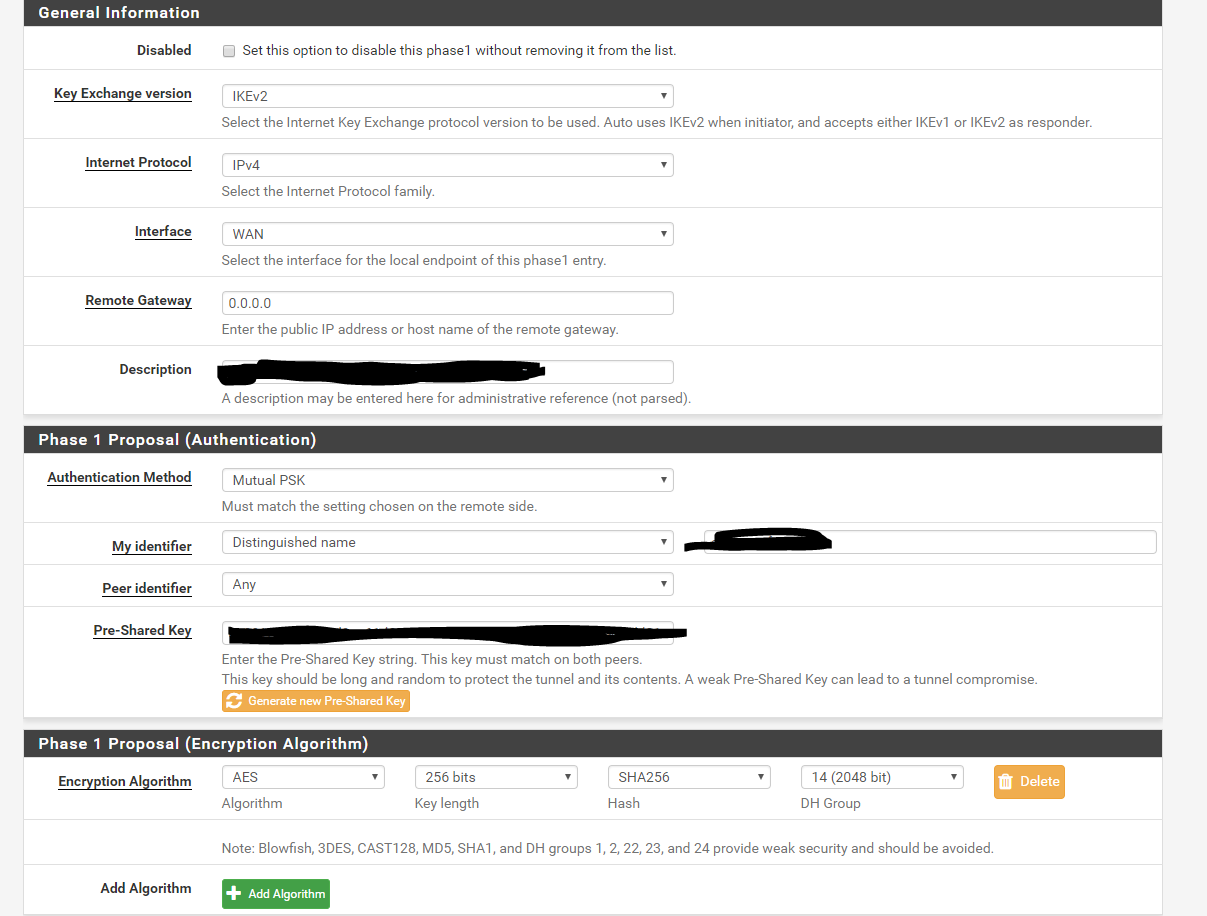
Here's the config on pfSense:
Phase 1 - 0.0.0.0 as our endpoints are dynamic addressing:
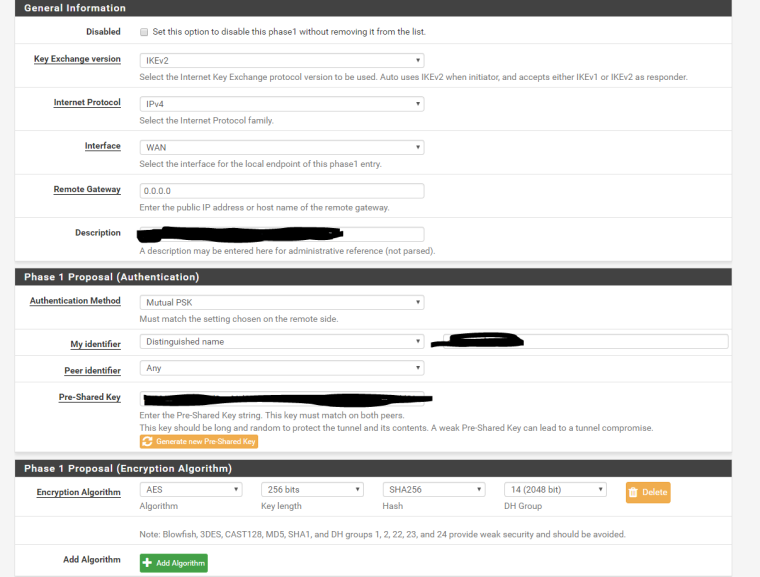
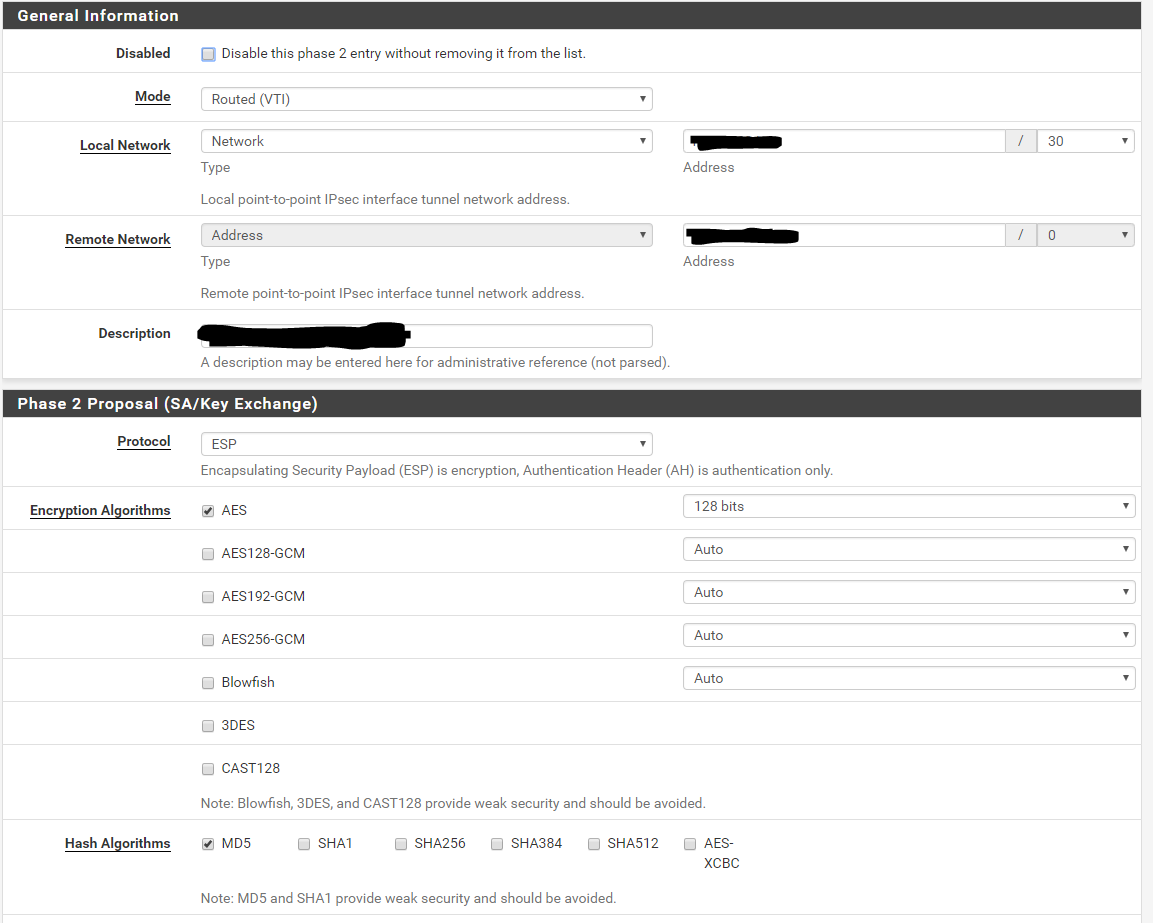
Phase 2:
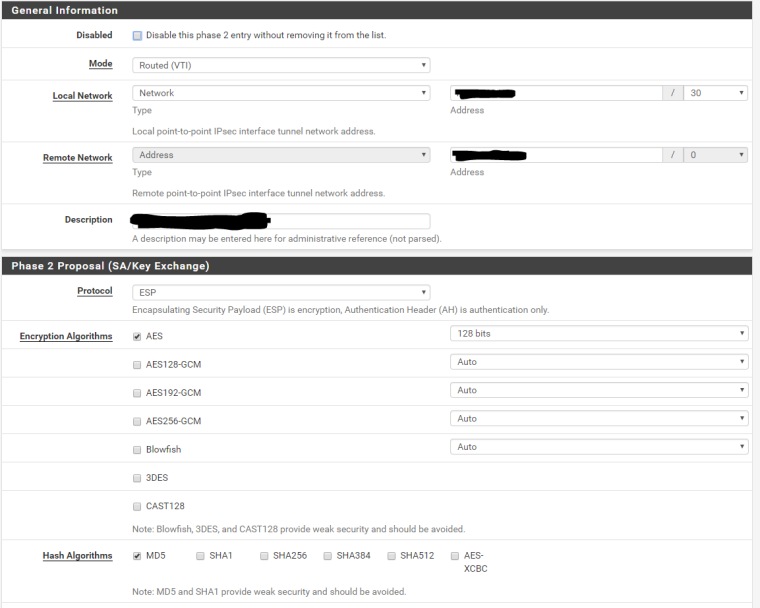
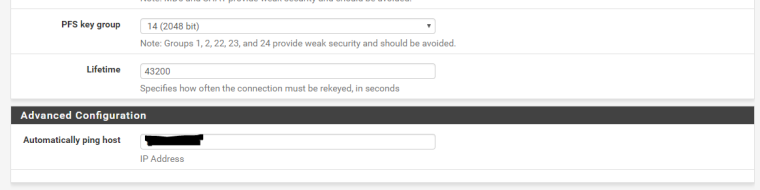
Interface:
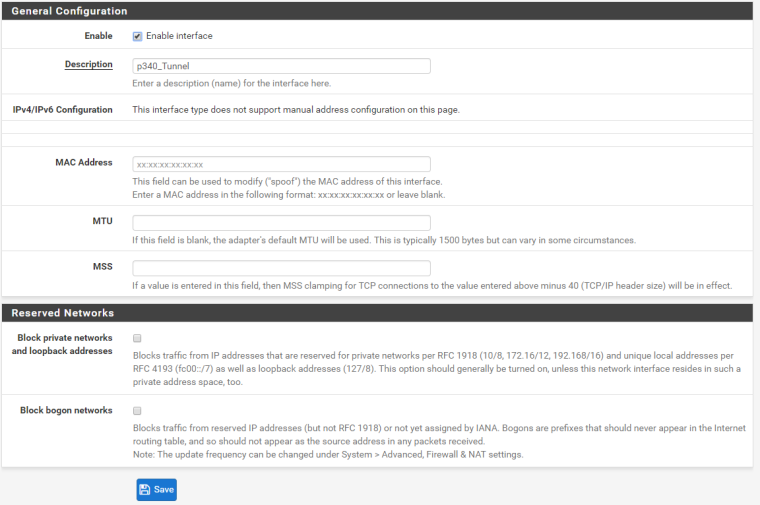
Route exists (.1 is firewall, .2 is router)

IPSec Status:
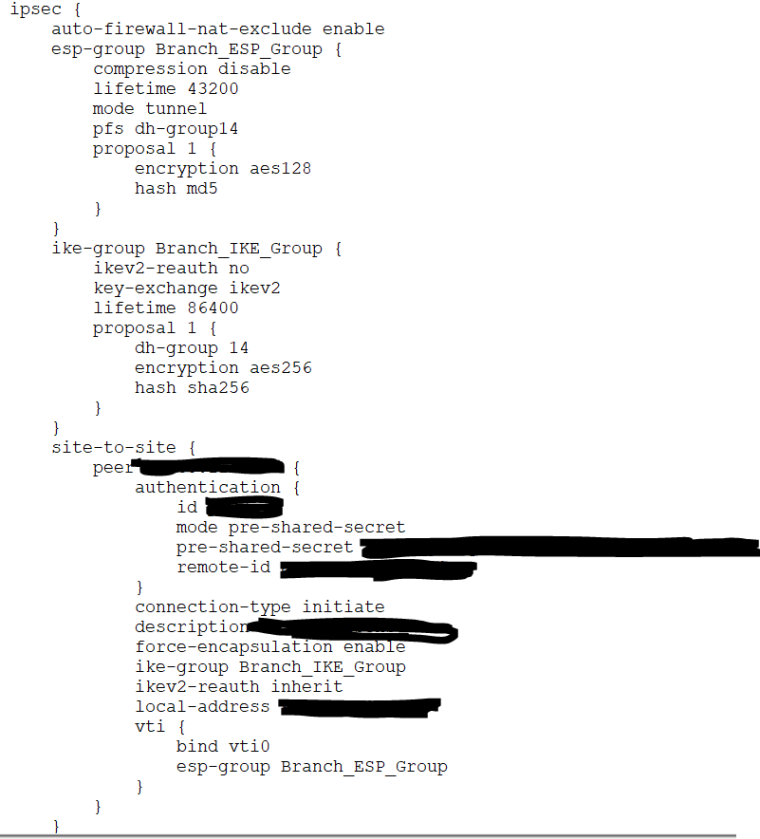
EdgeRouter Config (this editor is removing the tabs from config FYI so I had to use a snip):
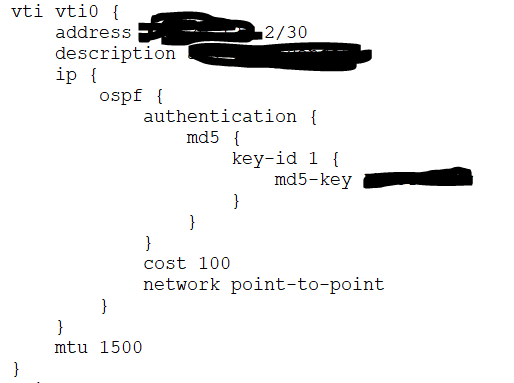
EdgeRouter SA:
router:~$ show vpn ipsec sa
peer-x.x.x.x-tunnel-vti: #1, ESTABLISHED, IKEv2, c895d3a75e6e4420:90d85a4da8e97efa
local 'x' @ x.x.x.x
remote 'x' @ x.x.x.x
AES_CBC-256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
established 366s ago, rekeying in 85359s, reauth in 84810s
peer-x.x.x.x-tunnel-vti: #1, INSTALLED, TUNNEL-in-UDP, ESP:AES_CBC-128/HMAC_MD5_96
installed 366 ago, rekeying in 41775s, expires in 42834s
in c4efe5c3, 0 bytes, 0 packets
out c475dda7, 33456 bytes, 400 packets, 0s ago
local 0.0.0.0/0
remote 0.0.0.0/0Any help would be appreciated! I have a little over 200 sites to deploy. :)
-
- correction:
And have installed the latest update to ensure the 0.0.0.0/0 route gets passed, but it seems the traffic from the VTI tunnel is not coming in on the ipsec6000 interface, but is on the enc0 interface.
The documentation states the OS should see traffic on both interfaces.
-
Upon further investigation I've noticed the following:
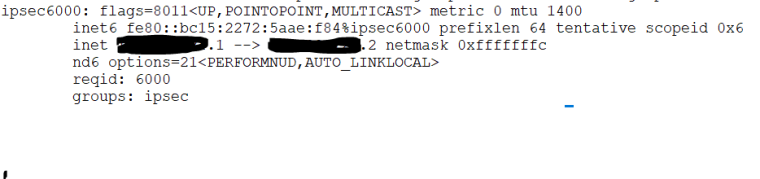
The interface is not showing a 'running' status, which explains my problem. Now to find out how to resolve it.
-
To answer my own question now:
VTI tunnels cannot be set up with 0.0.0.0 as the remote peer, you must use an IP address or domain name.