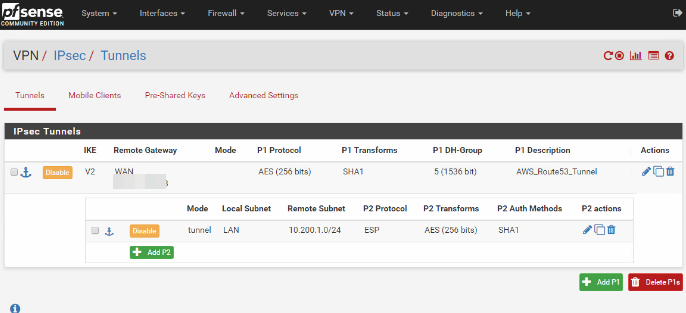
pfSense creating multiple P2 (child SA) entries
-
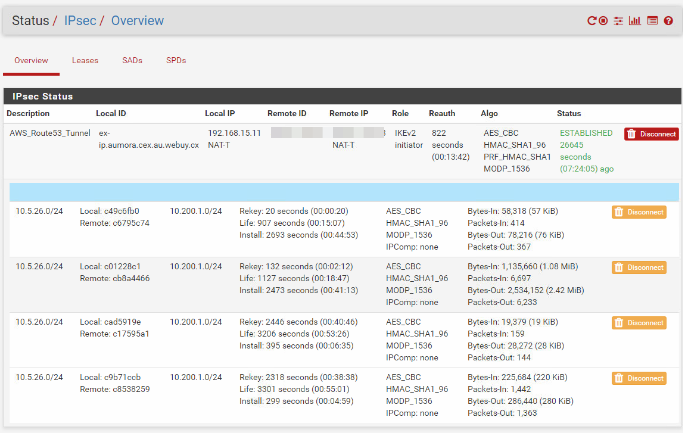
We have been having an issue with the IKEv2 protocol creating multiple child SA (p2) entries everytime the lifetime is renewed.
We have observed this issue with both the Pfsense version 2.4.3-RELEASE-p1 (amd64) & v2.3.5.
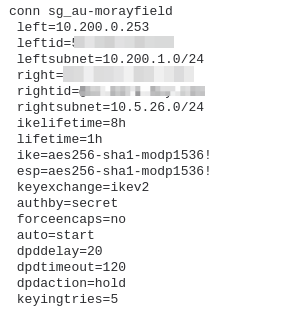
This is a site-to-site IPsec VPN setup between pfSense to Strongswan. The Strongswan is located in the Amazon Ec2 instance using Amazon Linux 2 OS.(StrongSwan U5.6.3/K4.14.62-70.117.amzn2.x86_64)
Attaching the configuration & logs of both the ends.
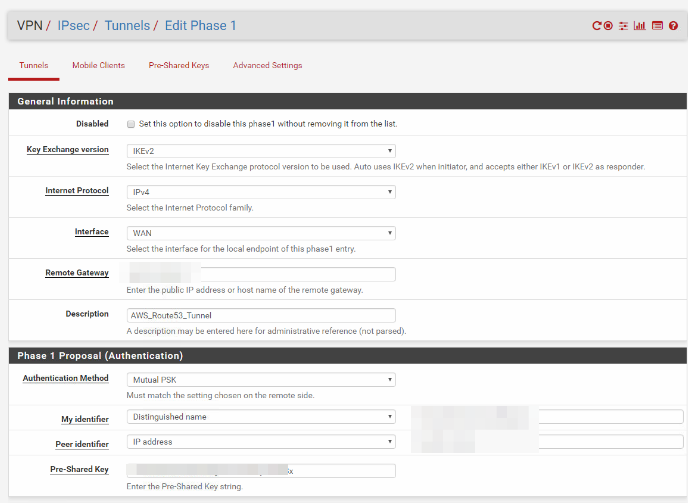
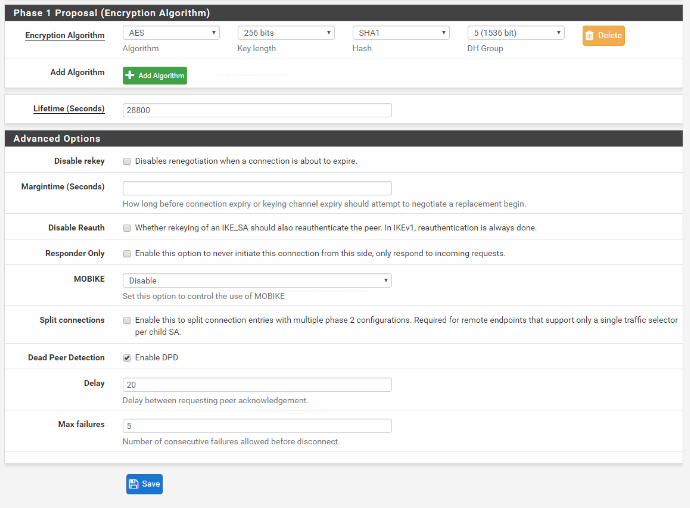
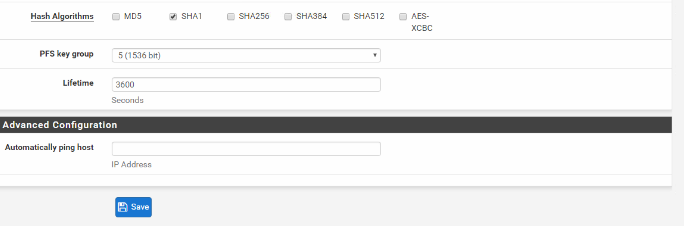

0_1542902059807_Pfsense Ipsec Logs.txt
0_1542902084215_Strongswan Logs.txt.gzPS: The Public IP mentioned in the logs will is not the original one as I have changed it for security reasons.
-
Hey guys,
We still continue to have the problem. Can you please help?
Regards,
Vijay Rao -
They are rekeyed tunnels. They are harmless.
They are kept around in case the other side sends traffic for the old SA, which sometimes happens with some IPsec implementations.
They are visible there for the time between the rekey and the full lifetime expiration.
Are you experiencing actual traffic flow issues or do you just not like to see them listed?