PFSense NAT 1:1 IPs over VPN
-
Hi all, been using PFSense for a long time and I'm a huge fan.
We have two locations, A and B. Location A has a large WAN subnet assigned to it, while location B does not.
We are moving computers from location A to location B. They currently have different IPs assigned to them. The goal is to have two or more computers hosted in location B to tunnel traffic through to location A and have location A NAT them different WAN IPs.
Right now the computers are simply connected to the WAN via a switch and have static IPs assigned to them, let's say it looks like this:
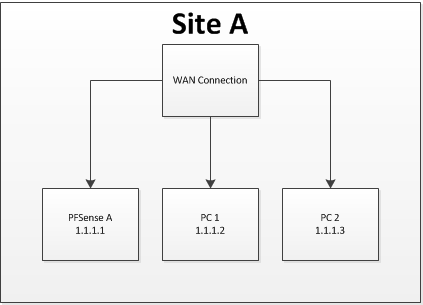
Using the numbers above, we want to move them to location B and tunnel "1.1.1.2" and "1.1.1.3" to those PCs via the VPN. This has proven challenging.
I assumed I could not just transit WAN IPs over the VPN and would need to NAT the traffic. So the idea then would be:
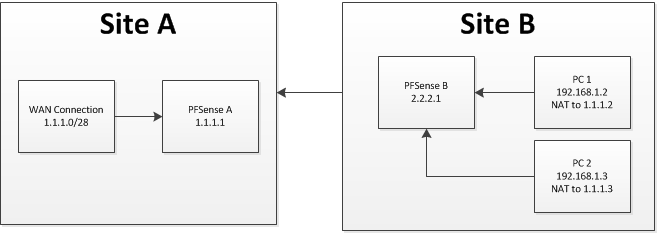
The only way I could see to route this would be through VTI tunnelling, which I was happy to see is now supported.
I created a test computer on site B. I set up a VPN connection and created a VTI Phase 2 tunnel. I created a local static route on either side to either subnet. Then I created a firewall rule piping all traffic through the VTI tunnel gateway for the test computer.
I can now confirm that traffic on the test computer is routed from site B over to Site A and given IP 1.1.1.1. that's where my success ends.
Setting it up I was sorry to see that 1:1 NAT is flagged as 'fishy' in the latest release. Sure enough if I try and change NAT to any virtual IP I just loose connectivity immediately.
Is there anything I can try or any additional suggestions anyone would have? Is what I'm experienced a known issue at this point or should I expect that to work?
-
I thought I'd try to RTFM on doing this via a tunnel interface rather than VTI as per https://www.netgate.com/docs/pfsense/vpn/ipsec/routing-internet-traffic-through-a-site-to-site-ipsec-vpn.html
I had not realized you could pipe 0.0.0.0/0 through a VPN tunnel.This config works without any issue, and considering the warning on the site: "There are also known issues with NAT, notably that NAT to the interface address works but 1:1 NAT or NAT to an alternate address does not work." - I would assume that this is a VTI limitation. Still if anyone has any additional info on this it'd be interesting to know.