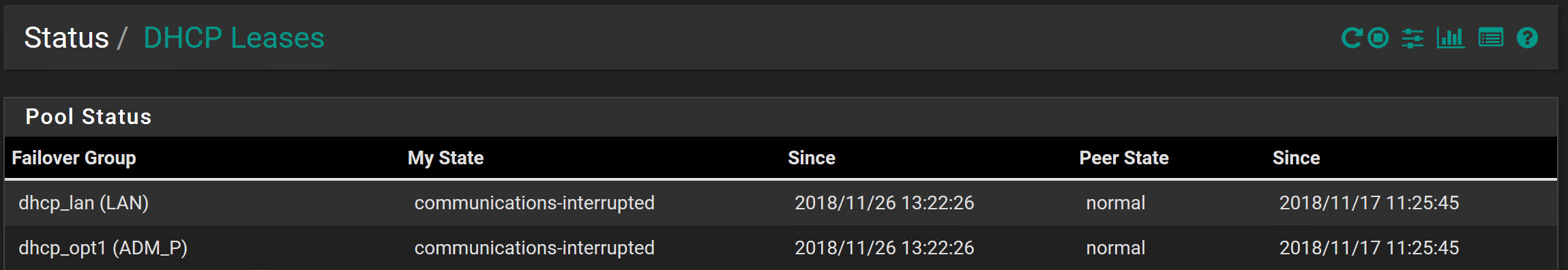
communications-interrupted in Failover group
-
hello
My current setup have 2x pfsense in HA
I got something that I don't know if it is normal or not in Status--DHCP Leases --- Pool Status
Any suggestion !!!!
EDIT :
Communications error occurredA communications error occurred while attempting to call XMLRPC method restore_config_section: @ 2018-11-28 12:43:41 A communications error occurred while attempting to call XMLRPC method restore_config_section: @ 2018-11-28 12:44:41 -
anyone?
-
Not normal, as 'My State' suggests.
Verify the settings- they should be the same, except for the failover peer, which should be the ip of the other box, on the listening interface. If everything looks good, stop the dhcp service on both boxes, start on the master, then start on the backup. -
@dotdash Hello
I did as you suggested all was looking normal
my VIP is xx.xx.xx.1
my Master is xx.xx.xx.2
my Backup is xx.xx.xx.3each interface have following config
DNS servers because I use pfSense unbound all the same xx.xx.xx.1
Gataway also xx.xx.xx.1
Failover peer IP Master xx.xx.xx.3
Failover peer IP Backup xx.xx.xx.2Then I stopped and started the DHCP service as you suggested and I am still getting the same in "My State"
I have tested by adding rules on the Master seems the rule appear on Backup as well
Don't see any problem thereThank you
-
OK it is all back to normal now I don't know what I did exactly but "My State" is normal
Some how when I disconnect the master all traffic should go trough the backup with almost not notable by the hosts, but it is not happening
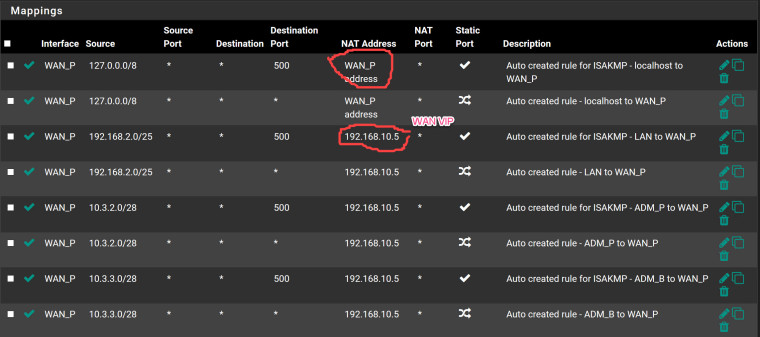
Here is what I did for NAT-Outbound
I put all interfaces except the loopback into my WAN VIP address like so
-
You'll probably need to post the DHCP Server pages on both nodes.
The communications between the DHCP servers occurs on the interface DHCP is running on. It has nothing to do with outbound NAT, the sync interface, or anything like that.
There are automatic rules placed in the firewall to pass this traffic between the nodes on that interface on ports TCP/UDP 519 and 520:
# allow access to DHCP failover on LAN from 172.25.236.3 pass in quick on $LAN proto { tcp udp } from 172.25.236.3 to 172.25.236.2 port = 519 tracker 1000002644 label "allow access to DHCP failover" pass in quick on $LAN proto { tcp udp } from 172.25.236.3 to 172.25.236.2 port = 520 tracker 1000002645 label "allow access to DHCP failover"I have seen people place floating rules that ended up blocking this traffic in the outbound direction.
-
Hello
The problem was fixed all "My State" says "Normal", but today I had to add an other interface VLAN now I am getting "My State" says "recover" - "Peer State" says "unknown-state"
I had followed a few post here from people having the same issue and I couldn't fix that.
I tried
ping from Master to Backup and failed and from Backup to Master also failed
ping from host to both nodes on the new interface I added also failed I ping just to make sure I can ping from this host my other interfaces without issue 0% loss
I stopped DHCP on both nodes and started firs the Master then Backup node problem still exist
I rebooted both nodes still nothing
ANY suggestions ?
-
Have you made any floating rules?
-
@derelict YES
just blocking IPv6 traffic on all interfaces nothing else
-
It still sounds like you have a connectivity issue on that network between the two nodes. Are the CARP VIPs MASTER/BACKUP?
-
@derelict Sorry because my HA interface is a VLAN I forgot to added into the switch
That was the problem
Thank you