Mobile Clients with a entire Subnet
-
I am trying to establish an IPsec VPN between the main site and several probes. A "probe" should be a raspberry pi (with strongswan) which should build a site-to-site tunnel. It is important to know that I am behind a NAT with the Probe.
Main location 10.90.0.0/15
Probe001 sould be 10.94.1.0/24
Probe002 sould be 10.94.2.0/24
and so on ..I've found that I need to use Mobile IPsec on a NAT because my remote is complety dynamic.
I have now activated "Mobile Clients" and created a Phase1 correctly. As I understand it, I use Mutual PSK and define a ID+PSK for each Probe.
-> so far so good, I can also connect a Phase1 successfully.
My problem is that I can not get started with Phase2. Pfsense "Mobile Clients" always wants a Virtual IP. But I want a stati local and remote subnet for every Probe.
Strongswan also sends the "leftsubnet = 10.94.1.0 / 24" but the pfsense refuses.
(newest at Top)
15[ENC] <con-mobile|22> generating IKE_AUTH response 1 [ IDr AUTH N(AUTH_LFT) N(FAIL_CP_REQ) N(TS_UNACCEPT) ] 15[IKE] <con-mobile|22> failed to establish CHILD_SA, keeping IKE_SA 15[IKE] <con-mobile|22> traffic selectors 10.90.0.0/15|/0 === 10.94.1.0/24|/0 inacceptable ---> thats is not nice from you! 15[CFG] <con-mobile|22> dynamic 15[CFG] <con-mobile|22> proposing traffic selectors for other: 15[CFG] <con-mobile|22> 10.90.0.0/15|/0 15[CFG] <con-mobile|22> proposing traffic selectors for us: 15[CFG] <con-mobile|22> looking for a child config for 10.90.0.0/15|/0 === 10.94.1.0/24|/0 --> i need that !! pfsense get the proposed peer Subnet 15[IKE] <con-mobile|22> expected a virtual IP request, sending FAILED_CP_REQUIRED --> yeah, peer dont want to use Vitual IPs ... your are wrong pfsense 15[IKE] <con-mobile|22> maximum IKE_SA lifetime 28550s 15[IKE] <con-mobile|22> scheduling reauthentication in 28010s 15[IKE] <con-mobile|22> IKE_SA con-mobile[22] state change: CONNECTING => ESTABLISHED --> phase1 is goodhow can I set a remote subnet instead of Virtual IP?
thanks for the help
-
Dont use Mobile IPSec for a master. Use a classic IPSec with IKEv2.
Configure some fix IKE Identifiers like FQDN.The best way is to have a dynamic DNS on the dynamic site and use the dynamic DNS name for vpn connection.
Second Idea:
Maybe try to setup 0.0.0.0 as remote peer on your main firewall and activate "Responder only" Setting. -
@bepo
I tested it again,without mobile IPsec apparently there is a check of the "remote gateway" in phase1. The following works:- the current public IP of the peer behind the NAT
- DynDNS which resolves to the current public IP of the peer (behind the NAT)
- 0.0.0.0 as a peer
(anything else, a fake DNS, fake IP or fake Hostname will result in No_Proposel_chosen )
0.0.0.0 is not an option. I can only create one phase1 with that IP. Phase2 of Peer1 is overwritten by Phase2 of Peer2. Moreover, it is safety-critical because I would only have one PSK for all peers (probe).
But I do not understand the behavior of pfsense! if I have to use "responder only", why is the peer address relevant at all?
Do I really need to resolve to a DNS name just to get a valid "peer-address" check in phase1? because the peer ip is not needed, only in the UI
-
I still need a solution to this problem.
My current workaround is to create a dyndns-Hostname behind the remote-NAT for the remote-PublicIP that will be updated by the remote peer within the remote-network.although I never want to connect from local to the remote peer (because of the NAT) i need this dyndns because of the pfsense UI that requires me to enter the Valid-remote-PublicIP as gateway... (although I use responder only at local.... )
that is not prety but it works ...Now i have the same problem over again because i have a Remote-Network with a Loadbalancer that uses several diffrent PublicIPs for every new Connection. My workaround does not work in this case because the dynDNS approach is useless...
i need to be able to create multible Site-to-Site tunnels with "Responder-only" and remote-gateway "ANY" identifyed by Remote&Local ID
How is that possible???
-
@blackbinary
Hey
This is possible, but you must make changes to the PFsense configuration files (responder side)
As a result of these changes, PFSense will create a config file (ipsec.conf) that will allow strongswan to accept connections from any ip address
Here is an example of how it looks in practice after the changes
In the settings section of Remote Gateway you enter "any"
and the necessary config is ready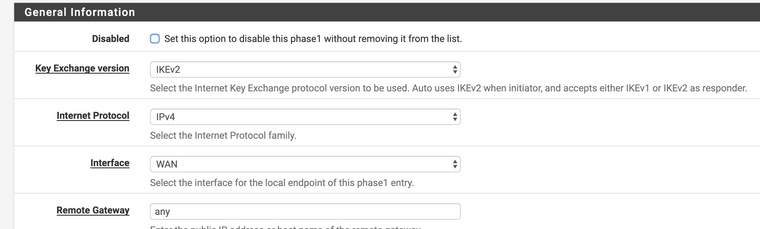
If you write me in the chat your email, I'll send you an email with all instructions