[SOLVED] SMTP notification error (SMTP: Failed to connect socket: fsockopen()...) with TLS and private CA
-
Thank you for your reply. The mail server is an internal one - that's why it does have an internal PKI certificate. I can send and receive email using any mail client, and other devices using internal SMTP notifications as well.
The certificate isn't self signed, the internal PKI structure is as follow:
"Internal CA" -> "Internal intermediate CA" -> "mail server certificate"
There are different intermediate CAs depending on the type of certificate issues (the CA issuing server certificates doesn't issue users or code signing certificates, for example). I was planning to add another intermediate CA to issue VPN certificates.
My first attempts were made after I imported the "internal CA" into pfSense (and a server certificate for pfSense itself, no issues)
Then I tried again after importing the "internal intermediate CA" as well. pfSense does recognize that the "internal intermediate CA" is issued by "internal CA". But SMTP certificate check still fails.
I'm starting to wonder what CAs list the SMTP process is using, and if CAs imported into pfSense are available to all processes or not (i.e. stored in FreeBSD CAs store) - and how the SMTP process performs the certificate chain check.
I didn't try with an external service yet, I believe it would work, but it's not an option in this case.
-
https://forum.netgate.com/topic/125582/solved-need-to-add-an-upstream-certificate-for-my-fw
-
Thank you for the link, it confirmed my suspicions.
I was looking into the OS CA lists and I didn't find the CA I uploaded into pfSense. So it looks they are stored elsewhere, and aren't used for verification by some of the processes/services - which IMHO looks like a bug to me, or at least lack of proper documentation, if the CA imported into pfSense are used only for some tasks and not others.
Adding them to the OS lists is not a problem, it needs to be done just once until the expiration date - I just hope an update won't reset the lists.
-
Test also with :
openssl s_client -CAfile /chemin/vers/ton/ca-certificates.crt-connect mail.ton-server.tld:465 -
Solved.
After adding my CA to /usr/local/share/certs/ca-root-nss.crt the mail message was properly sent. I dumped the certificate contents using:
openssl x509 -in ca_certificate.pem -textAnd added the output to the end of the file.
Evidently that is the CAs list used by the SMTP sending code.
Thank you everybody for pointing me in the right direction.
-
I didn't see it before, or 2.4.4-p1 added an option to disable certificate validation?
-
This one
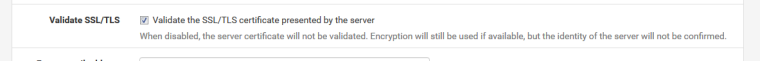
?
-
Yes. Was it added in the latest release, or I was so blind I didn't see it before?
-
It's new : https://github.com/pfsense/pfsense/commits/master/src/usr/local/www/system_advanced_notifications.php
-
Not fixed as of 2.4.4-RELEASE-p3 (amd64)
built on Wed May 15 18:53:44 EDT 2019
FreeBSD 11.2-RELEASE-p10.Only after appending the text dump of my ca cert to /usr/local/share/certs/ca-root-nss.crt was I able to send test messages.
"Validate the SSL/TLS certificate presented by the server" had no effect.
Package captures verified that pfsense was rejecting the certificate being returned by my email server.