Unbound vs. Pihole
-
when i have to go to the supermarket to buy the toilet paper i always go with a ferrari

for the same reason even if the pi3 is more than enought for pihole i personally will buy the pi4,
the USB-C is not really a big problem, just don't buy any e-marked USB-C chargers, the official one or any chargers coming from a smartphone/tablet that can do 5v / 3a work without problem.
i didn't have any stability problem on my 3 raspberry pi 4, with kodi /ntp server/wireshark and other services i'm running, personally the only downside i see here is power consumption -
@kiokoman said in Unbound vs. Pihole:
personally the only downside i see here is power consumption
I do try and minimise power consumption as much as possible, but then again I'm running a server rack with pfsense router, QNAP NAS, 48-port Ubiquiti switch, Ubiquiti CK2+ controller/surveillance and 3 access points.... so doubt a Pi is gonna make a huge difference to that. Do you have a rough idea of Pi4 power consumption in watts for typical usage?
Also, how do you find piHole compares to pfblockerng-devel for protection against malware, ransomware, etc (as opposed to ad-tracking)? Are the lists easy to maintain? I really liked pfblockerng but I found issues with lists not downloading after a while and generally had issues with maintaining it after a while.
-
@occamsrazor

Idk, my network is more or less like what you have
I don't use pihole nor pfblocker, i have suricata on pfsense and bind9 on a server -
@occamsrazor said in Unbound vs. Pihole:
Do you have a rough idea of Pi4 power consumption in watts for typical usage?
To the power question, here I found this
https://www.tomshardware.com/reviews/raspberry-pi-4-b,6193.html
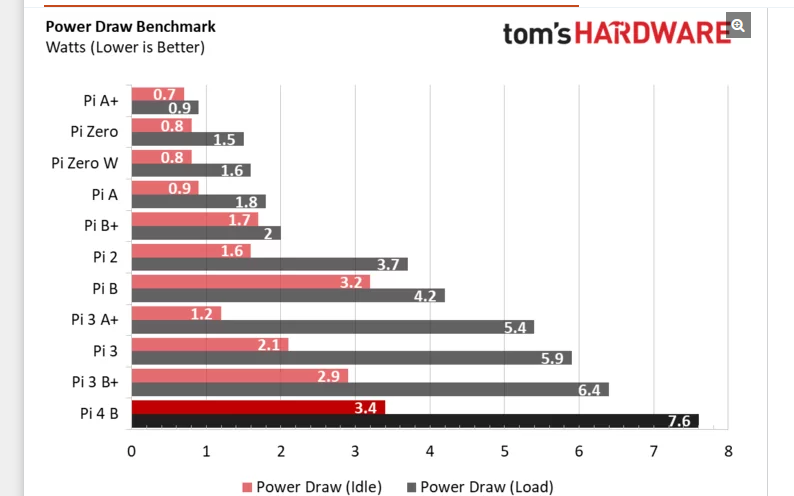
Compared to a pi3 b+ its almost not worth even discussing to be honest.. Especially when you compare overall performance differences.. I can not see for the life of my why anyone would buy a 3 vs a 4 currently.. Unless there was something very specific needed to use the 3.. Which off the top - not sure what that could be - maybe a hat a peripheral that didn't work with the 4?? Or maybe can not get a 4 because of out of stock or something, and you want the pi now, so you get just the 3
So lets say your pi4 was just balls out all the time drawing 7.6 watts.. Lets call it 8.... If you do the math...
Assuming your elec cost you 12 cents per kwh
Electricity cost per day: $0.02304
Electricity cost per month: $0.70128
Electricity cost per year: $8.41536So worse case its going to cost you something like $8 a YEAR to run your pi 24/7/365 with it just balls out running 100%..
For it to be just doing dns.. your prob going to be real near the idle usage.. So what like $4 a year.. Not sure what you pay for elec... But adjust for your cost... For each cent difference from the 12 cent, about 0.70 a year difference.. At the full balls out 8 watt number.
If your really wanting to lower the elec cost - just get a zero.. It can more than handle running pihole..
-
Thanks @johnpoz.
If you have a pihole which is set to resolve against pfsense which is DNS resolving from root servers, will the Redirecting all DNS Requests to pfSense rule still work?
ie. the rule described here: https://docs.netgate.com/pfsense/en/latest/dns/redirecting-all-dns-requests-to-pfsense.htmlDo you just need to change the Redirect Target IP to the pihole internal IP?
Does the Redirecting all DNS Requests to pfSense work with DNS over TLS, port 853?
-
I am not a fan of "redirecting" anything - I would just block anything from talking to anything other than pfsense for dns..
But sure you can still redirect anything that might ask something other than pfsense or pihole on 53 to go to pihole - but you prob need to put pihole on a different network than the client is on or you run into some weirdness... There was a thread not that long ago where this came up.
As to redirecting some client that tries to go to 1.2.3.4 on 853 for dns via dot.. While you could have have something listening on 853 for dot.. unbound can do this - you never know what the client might be doing to validate - maybe the end dns they are trying to talk to via dot has to be using a specific cert? etc..
-
Hi @johnpoz,
yes that makes sense. So maybe use this method instead to block both ports 53 and 853, and enforce only using pfsense for DNS:
https://docs.netgate.com/pfsense/en/latest/dns/blocking-dns-queries-to-external-resolvers.html
-
yup that is how you would do it..
-
There’s a simpler way to do it combined in a single rule, with an alias for the two DNS ports (if you need more than one) and a “!” to invert the meaning, see this post:
https://forum.netgate.com/post/791318
Hope am remembering/linking correctly, am on my phone at the moment...
-
@occamsrazor said in Unbound vs. Pihole:
There’s a simpler way to do it combined in a single rule
Wouldn't call it simpler exactly, but sure you could do it with a bang rule as well.. As long as no vips running that might mess up the ! rule... Is always cleaner and easier to read when your explicit with what you block and what you allow.
-
@johnpoz I just find it cleaner because it is one single rule, rather than the two in the docs but I guess either is fine. Could you explain "As long as no vips running that might mess up the ! rule" am not sure I understand what "vips" is here....
Also, thanks for finding that Pi power consumption chart - very useful indeed, and yes - power consumption differences virtually insignificant compared to what else I am running.
FYI for piHole users, not sure what to think of this? https://www.zdnet.com/article/pi-hole-drops-support-for-ad-blocklists-used-by-browser-based-ad-blockers/
-
Here
https://redmine.pfsense.org/issues/6799And here is thread where me and derelict discussed it.. I am a fan of using the ! rule, but if your going to use them you have to make sure to double check your not running into any issues.
https://forum.netgate.com/topic/128202/invert-match-doesn-t-work