Pfsense Firewalls Rules
-
hello guys
i've made a default deny rule from LAN to Wan at the bottom of the rule set and trying to permit only the sites that the company need for work
i've made also a host alias for our domain and made a permit rule to access it and it's already working successfully
but i've tried to permit gmail , i did a permit rule to access google.com(host alias) and we can access google but we cant access gmail
the same issue with yahoo mailwhat is the best way to do that, please??
-
Deny to WAN is just that WAN, that is not the internet..
Post up the pic of the rules you created and we can discuss.
-
@johnpoz
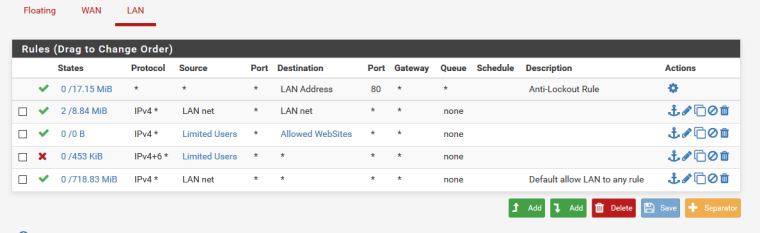 here is the pic
here is the pic -
Yeah your rule there that is lan net to lan net is pointless nonsense..
When something on lan wants to talk to something else on lan it doesn't need to talk to its gateway pfsense.. Pfsense will never see traffic to its lan IP dest for some other lan IP that it needs to allow.. That you show hits on that rule, is that allowing dns to pfsense lan IP?
Ok what is in allowed websites... And how exactly are limited users suppose to resolve where to go, are their dns servers listed in the allowed websites alias.. Do they use dns on the lan other than pfsense? I don't see any hits on the rule even.
-
@ghanosh said in Pfsense Firewalls Rules:
hello guys
i've made a default deny rule from LAN to Wan at the bottom of the rule set and trying to permit only the sites that the company need for work
i've made also a host alias for our domain and made a permit rule to access it and it's already working successfully
but i've tried to permit gmail , i did a permit rule to access google.com(host alias) and we can access google but we cant access gmail
the same issue with yahoo mailwhat is the best way to do that, please??
-
Create Host Alias and call it as Gmail_Allowed_Users and add users IP allowed to access Gmail.
-
Create Network Alias and call it as Google_Cloud_Subnet and add below list of net blocks:-
35.190.247.0/24
64.233.160.0/19
66.102.0.0/20
66.249.80.0/20
72.14.192.0/18
74.125.0.0/16
108.177.8.0/21
173.194.0.0/16
209.85.128.0/17
216.58.192.0/19
216.239.32.0/19
Note: this is the complete list of net black for google. i.e gmail,drive, smtp, pop, imap, apis , everything will be inside this block only.
now you can create rule using both Alias to allow.
PASS TCP Gmail_Allowed_Users * Google_Cloud_Subnet 80,443(http_ports)
Below this rule you can deny All.
Delete existing rule number 2 , 3, 4, 5
You can setup proxy to manage these type of request in proper manner.
-
-
As every big provider uses CDNs and CDN IPs may vary and change over time, using Aliases to allow huge sites like Google or Gmail may not be the best approach there is. If you really want to limit internet access to THAT extend, you should perhaps think about using some L7 technique as squid/squidguard to limit access?
-
@jegr said in Pfsense Firewalls Rules:
As every big provider uses CDNs and CDN IPs may vary and change over time, using Aliases to allow huge sites like Google or Gmail may not be the best approach there is. If you really want to limit internet access to THAT extend, you should perhaps think about using some L7 technique as squid/squidguard to limit access?
Most of the google traffic apart from gmail /youtube/drive goes directly via firewall , for example smtp , postman, etc .working with api calls is problematic .
Also configuring and running squidguard is little hectic. in this particular situation only google traffic can be managed via firewall polices itself. network range for google hasn't changed for a long time. user can redirect output of dig command to some text file hosted somewhere or inside firewall and use as alias. -
@vallum No, network range may not have changed, but IPs in it have changed around quite a bit. So yes, you can use a big hammer just try and hit everything with it, trying to match the correct IPs for the services. Or you can use a finer tool like a knife and cut out the services you actually want. Proxies are not that "hectic" but a finer tool for limiting access. And if that's what the OP is wanting to do, I'd have a look into it. Of course one can dismiss it as not worth the work and just go with IPs. Didn't say a thing against that. Just know, that blocking internet services today via brute-force IP usage, you'll get false positives, side effects etc. in blocking networks or hosts that are in use for multiple purposes.