Inter-Network Blocking Question
-
Hey everyone I am somewhat new to pfSense and have been tasked to setup about 20 dedicated networks for conference rooms in an office. Setting up the Interfaces / DHCP / VLANs isn't an issue what I am trying to figure out is the best way to block each of the networks from seeing each other and of course accessing the GUI.
I know that I can do this with individual rules for each Network but was trying to figure out something a little easier like an alias or maybe even a floating rule?
With this in mind someone suggested that I created an alias with all of the networks listed in it. From there go to each of the networks firewall rules and set up the following two rules (using LAN100 as an example).
Rule 1)
Action - Pass
Interface - LAN100
Protocol Any
Source - LAN100 Net
Destination - LAN 100 Net
All other entries are the defaultRule 2)
Actio - Pass
Interface - LAN100
Protocol - Any
Source - LAN100 Net
Destination (Invert Match) Single Host or Alias - (Network Alias with all VLAN Networks Listed)
** All other entries are default**This does work in blocking access to each of the other networks as well as allow the network to access the Internet. I do however have some strange behavior where it seems like I can sometimes access the Web Interface of the pfSense box and sometimes I can not.
Am I going in the right direction with this? I am trying to avoid making an Alias for each of the VLANs with itself not listed but that obviously is an option.
Any help / suggestions would be greatly appreciated.
-
I also use the invert match rule @Derelict isn't too keen.
Ideally the rules should look something like this:-
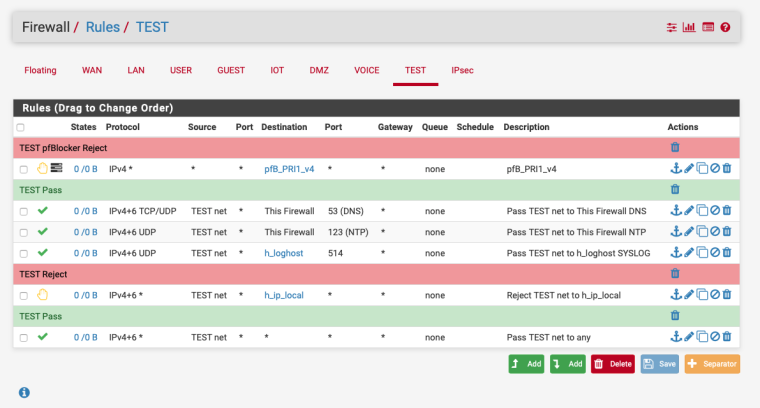
You can ignore the pfB_PRI1_v4 rule that's pfBlockerNG and the SYSLOG rule
You could use a floating rules and just not apply it to one of the interfaces that you use for switch and router management :-
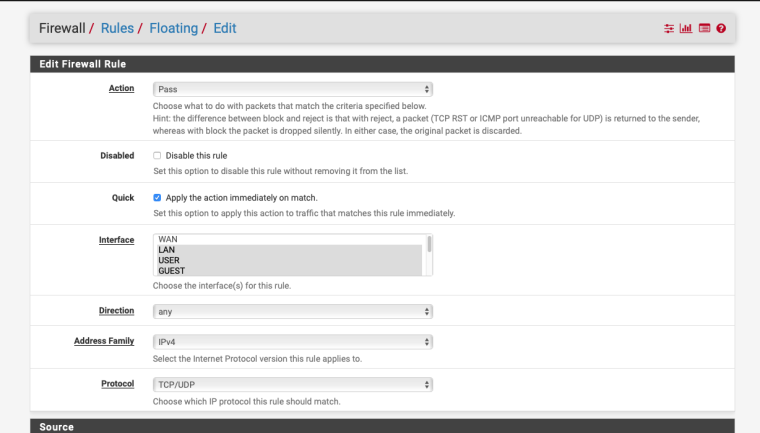
-
Instead of trying to block every network I would consider something like:
- Pass the local assets they need access to (DNS Server(s)s, NTP, etc)
- Pass ICMP to the interface address and DNS server(s) etc so they can ping those.
- Reject everything to RFC1918/All Unroutable networks
- Reject everything to This Firewall (self)
- Pass everything (The internet).
Is IPv6 a factor?
I would also seriously consider just using layer 2 port isolation if the only goal is to block them from each other. Then you could maintain one network instead of 20. It might be nice to have them all completely separate though, for accounting/troubleshooting purposes.
And, no, I don't like blocking traffic with pass
 rules. Traffic should be blocked with block/reject rules.
rules. Traffic should be blocked with block/reject rules. -
Thanks for the replied guys - These networks are are going to be wide open to the Internet which is why they want these to be on their on dedicated VLANs and not to be able to access each other or the firewall itself.
These are just "Guest" Networks and will never access any internal assets. This is the way they want it and I felt that VLANs and blocking would be the best way to go about it.
I am not really sure about the inverted pass rule... I tried this on 3 different devices and one two of them it seems to work perfectly and the 3rd for some reason I was still able to access the firewall itself from inside one of the VLANs. One thing worth mentioning I did reboot the other devices but didn't reboot the one that can still access but did reset the states on it.
Currently IPv6 is not a factor but never say never. =)
-
If IPv6 is not a factor now then you deal with that when it is.
So you're not providing local DNS or anything?
Then eliminate point 1. above.
-
Re accessing the firewall when you thought you’d blocked it.
Did you kill the firewall states after creating the block rule?
-
Create a interface group containing all of the networks for conference rooms.
On the interface group
Permit all traffic to public networks
Permit access to the GUI (PFSense web interface? in this case is better to allow access only from a few non dhcp addresses OR create and extra VLAN dedicatet to management only.)
Block all traffic to private networksThis should be fine.
-
Thanks for the suggestions guys - I tried the various things suggested but couldn't get it to work. Just to get it up and running I ended up doing what I didn't want to do which is create an alias for each of the Networks with all of the other networks in it but itself then added that in to each Interface Firewall Rule to block the Alias for that Network.
There has to be an easy way to do what I wanted to do originally without using the Inverted rule. Having a single Alias with all of the Networks that I want to prevent from seeing each other would make life a whole lot easier vs going in to each alias and adding any new network.
I tried the Interface Group but correct me if I am wrong when you go to add firewall rules to it you seem to be a little more limited then regular interfaces?
I thought that some kind of floating rule would / should also work but again it seemed like I would somehow end up blocking all traffic as in not being able to get out at all or still being able to access the other networks.
I have this setup running on a few test machines now and want to keep playing with it for sure.
-
If you dont what your other networks to talk to each other..
Then just create a alias for say all rfc1918 networks
Create rule(s) that allow access to what you want to allow on other networks, local access for say dns, ping to pfsense IP address in that network.
Then block/reject access to alias rf1918
Then allow any any (which will allow internet)
-
@johnpoz said in Inter-Network Blocking Question:
If you dont what your other networks to talk to each other..
Then just create a alias for say all rfc1918 networks
Create rule(s) that allow access to what you want to allow on other networks, local access for say dns, ping to pfsense IP address in that network.
Then block/reject access to alias rf1918
Then allow any any (which will allow internet)
Hi - Thanks for the information, in this instance I would have to an alias for each of the networks correct? If I list "All" of the private networks it would end up blocking itself before it hits the any rule.
This is what I am trying to avoid, I would like to have a way to have a single alias with ALL of the Networks that I don't want the others to be able to access. In this case this will be a series of Interfaces going to conference rooms 20 of them at this point.
I know I can create an Alias for each of the Networks / VLANs with all of the other networks listed except for itself but again I am trying to avoid that if possible.
Am I missing something?
-
@pete-man said in Inter-Network Blocking Question:
If I list "All" of the private networks it would end up blocking itself before it hits the any rule.
What, exactly, do you mean by this. Please be specific.
-
@derelict said in Inter-Network Blocking Question:
@pete-man said in Inter-Network Blocking Question:
If I list "All" of the private networks it would end up blocking itself before it hits the any rule.
What, exactly, do you mean by this. Please be specific.
Lets take a step back what I am trying to do it the following, as I mentioned I am trying to setup a number of Interfaces / Networks / VLANs that will be used for public access in various conference rooms. For ease of use I have set the networks up like this.
VLAN 20 - 192.168.20.0 / 24
VLAN 30 - 192.168.30.0 / 24
This continues on with VLAN 40 through 70 for now.There are a few more Networks / Interfaces including including the Local Private LAN, WAN and management Network.
The goal is to provide each of the about Networks / VLANs 20 through 70 Internet Access but block them from accessing any of the other VLANs as well as the Firewall itself (GUI).
To be clear I have no issues setting up the VLANs / IPs / Interfaces on within pfsense, the question is setting up the rules as follows.
How can I simplify blocking each of the Networks / VLANs 20 through 70. I was looking to make an Alias that included ALL of the Networks that I want to prevent the others from accessing including the Managements and Private Networks and putting in a few rules in each interface (or maybe even some kind of floating rule) to accomplish this vs created an Alias for Each of the Networks / VLANs which has all of the Networks listed except for itself and apply it to each interface as a blocking rule using the Alias and a Pass rule for everything else. I know this will work but can lead to some mistakes if say an additional Network is added.
Hope this makes sense.
-
No. What did you mean by that statement?
If you want to block a VLAN from accessing any other private resource, then block it to a destination alias containing:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16What are your concerns with doing that?
-
@derelict said in Inter-Network Blocking Question:
No. What did you mean by that statement?
If you want to block a VLAN from accessing any other private resource, then block it to a destination alias containing:
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16What are your concerns with doing that?
If I put a blocking rule in place that contains those networks isn't that going to end up blocking itself? How do I prevent it from blocking itself in that rule? I put a rule like that in place and of course it is the first rule it hits so it blocks itself, I can not access the internet and of course any other network.
If I put a pass any / any rule in first it will never hit the blocking rule.
-
Because it blocks traffic to those destinations, not sources. Traffic destined to the same subnet never gets sent to the firewall.
-
@derelict said in Inter-Network Blocking Question:
Because it blocks traffic to those destinations, not sources. Traffic destined to the same subnet never gets sent to the firewall.
Ok since I am somewhat new to pfSense I assume I am missing something here.
I just setup the following test install of pfSense
em0 - Wan - DHCP - Has Internet access
em1 - LAN - Default 119.168.1.1em2 - Set up with the following VLANs through a Trunk Port
VLAN 50 - 192.168.50.1 / Set up as DHCP Server
VLAN 60 - 192.168.60.1 / Set up as DHCP Server
VLAN 70 - 192.168.70.1 / Set up as DHCP ServerSetup an Alias with ALL of the Above VLAN Networks Listed in it including the LAN Network.
Currently all of the Interfaces so up / work and I get IPs from their proper Networks. Of course I can not access anything I haven't set up any rules as of yet.
Here is where I am wondering what the best practices are. What rules would you suggest I put in each interface so that I can do the following (I only need one example / Not all):
Allow access to the Internet
Prevent Access to All other VLANs mentioned in the Alias
Prevent Access to the firewall itself (GUI / Command line) -
So where were your clients get dns? Pfsense or external (internet)
As traffic enters and interface from the network its attached to rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Here just gave an example in this thread
https://forum.netgate.com/topic/138813/isolating-vlans-from-each-other-and-management-interface/2Vs sending it out the vpn connection, don't set gateway on last rule. Use your alias vs rfc1918 alias. But to be honest just create alias that contains all rfc1918.. That way when you add vlan 80 for example you don't have to worry about editing your alias ;)
-
@johnpoz said in Inter-Network Blocking Question:
So where were your clients get dns? Pfsense or external (internet)
As traffic enters and interface from the network its attached to rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
Here just gave an example in this thread
https://forum.netgate.com/topic/138813/isolating-vlans-from-each-other-and-management-interface/2Vs sending it out the vpn connection, don't set gateway on last rule. Use your alias vs rfc1918 alias. But to be honest just create alias that contains all rfc1918.. That way when you add vlan 80 for example you don't have to worry about editing your alias ;)
Hi and Thank you... This is exactly what I was looking for. I am not 100% sure but I think my issue was having my rules setup like you had listed in the example you linked to but I had all of my Rules sources set properly to the VLAN Net but I also had my my destination set as LAN vs and not addresses. This makes sense now and it seems to be working as I would like it to. Since all of my Networks are in the Private space and listed in my Alias do I need the implicit Block rules for access to this Firewall? I can't seem to access it from any of the VLANs I am testing from. I know it certainly will not hurt I was just wondering.
Thank you again
-
The "this firewall" includes ALL ips on the firewall.. For example your WAN IP that is normally not a rfc1918 address. So this rule makes sure that NO IP on the firewall can be accessed.