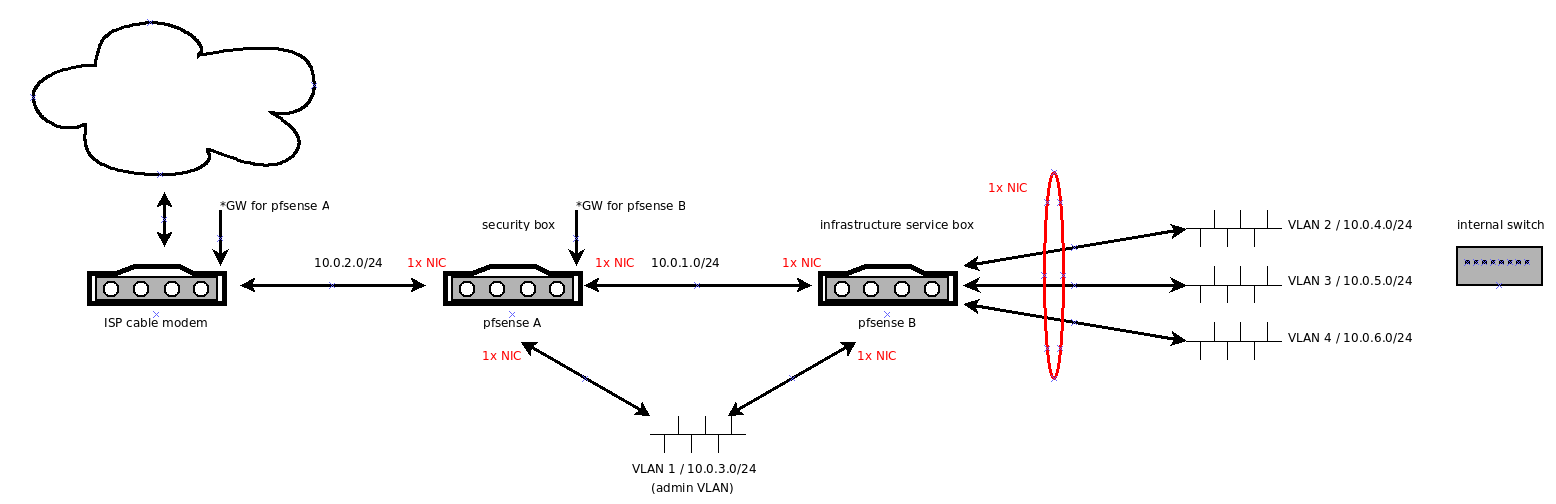
routing issue between subnets
-
Hi, i am out of (proper) ideas and need your advice.
I have a setup which looks like this:
As should be visible from the picture, the idea is to let 'pfsense B' handle the routing between the VLAN 2/3/4.
But to my frustration everything except routing between those VLAN works.- members of the VLANs have internet access (those that should have)
- members of VLANs can reach the 'pfsense B' IP of their VLAN
- pfsense box web UIs are only accessible via admin VLAN as intended
- ISP modem is accessible
- a HAproxy chain (one instance on each pfsense box) proxies services from one VLAN to the internet
- ACME service works on 'pfsense B'
... but i am too blind/inexperienced to get the (intra-VLAN) routing working.
Could you please point me in directions to investigate? I have to admit, i am unsure about the gateway setup and my netmask idea (many /24, connected by pfsense B).
Thank you very much!
-
Ok, i have to call this one closed.
It turns out to be rather important to have your switch configured correctly, who could have guessed that.
Maybe things work after i have rebuilt my configuration.Hint:
"router on a stick"-VLAN-setups with pfsense require the switch port of the stick to be configured as trunk in addition to allowing (only) tagged packets for the VLANs of your stick. In my case, without the trunk part everything except the routing worked. -
What is actually the point of this? Why do you not just use 1 pfsense box?
Are did you disable natting at B or now you have a triple nat for clients on your downstream vlans.. Sure you can set it up like that - but what exactly does it get you other than over complexity?
-
B replaced a legacy box which ran the internal services (DNS, DHCP, CA,...). It simply wasn't planned from ground up as it is now. I just thought that pfsense makes a good job at those things, too.
Considering merging the boxes A and B.. does it make a difference security-wise?
- having a <service> not sitting around on the IDS box? (could be countered by assuming same exploits work on both boxes)
Is this setup really so strange? I thought of it as natural. Ouch.
Edit: I did not knowingly deactivate NAT. I exposed box A to the net via 1:1 NAT but A->B and VLAN->VLAN should use regular NAT if i understand it correctly.
-
No vlan to vlan would NOT nat... But what good is your IDS, which you did not state you were running on pfsense A btw going to do if all it sees its the pfsense B wan IP since its natting as well.
No to be honest its not a very common setup.
Sure if you have a LARGE network and need to route at speed between your vlans then sure you might use a downstream router, ie a L3 switch.
But in a SMB or home setup - no that is not all that common.
So your thought process is that pfsense is doing the IDS, and can not handle doing the other services like dhcp and dns?
Also - that is not really a "modem" if its also natting which you show.. Why not just use a real modem.. Have pfsense get public on its wan and get rid of pfsense B? Hang your vlans off the 1 pfsense box.. Which sure could do IDS/IPS and your dhcp and dns.. It greatly simplifies the setup.
-
Correct. I was thinking in terms of building sort of "security domains". The (potentially wrong) assumption was, that having some sort of sacrificial anode to the net was something good.
But no big deal, i am not seriously attached to that idea if it makes no sense.