Outbound NAT problem on OPT1 using OpenVPN
-
I've pfsense installed with three interfaces: WAN, LAN, OPT1. My LAN is 192.168.1.0/24 and all machines on LAN side are connecting to the internet through OpenVPN client which was set up on OPT1 interface. My problem is on Outbound NAT.
In my LAN network I have web service on 192.168.1.20 (port 80) and I try to connect to it from the rest of the world. The service is running (I can log in inside my 192.168.1.0/24 network) and it seems that firewall rules are ok because packets are passed on firewall (I enabled logs in Firewall settings to log it).
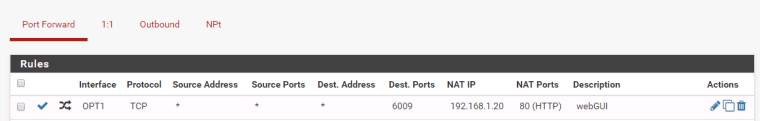
It looks like NAT works and firewall passes packets to 192.168.1.20 but there is problem sending response back.My Port Forward rule looks like this:
Interface: OPT1
Protocol: TCP
Source Address: *
Source Ports: *
Dest Ports: 6009
NAT IP: 192.168.1.20
NAT Ports: 80In Outbound I'm using manual Outbound NAT mode.
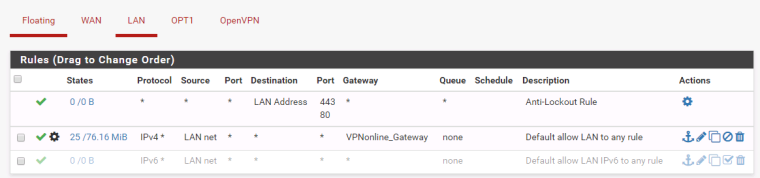
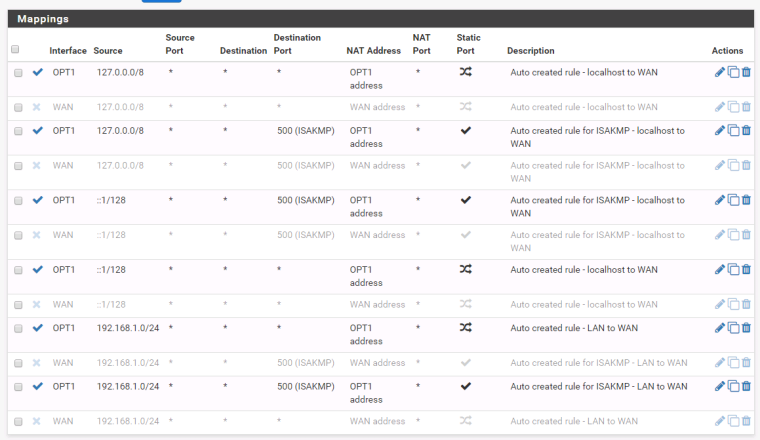
My Mappings (LAN to WAN and LAN to OPT1) looks like this:
Interface: WAN
Source: 192.168.1.0/24
Source port: *
Destination: *
Destination port: *
NAT address: WAN address
NAT port: *
Static port: Randomize source portInterface: OPT1
Source: 192.168.1.0/24
Source port: *
Destination: *
Destination port: *
NAT address: OPT1 address
NAT port: *
Static port: Randomize source portI've got localhost to WAN, localhost to OPT1 mappings also but I think they're not a problem in my case.
Can you help me?
-
@leszekkazmierczak I am far from being a guru,but you want to access your webserver from the VPN ip?that it should be inbound and "see" the VPN interface as a wan interface.When you created the forward rule for OPT1 did you select add associated filter rule?
-
Yes I did. Port Forwarding creates Firewall rules by default in my version of pfsense.
-
@leszekkazmierczak i never test to connect to my internal server using pfsense as vpn client ,i allways did from my ISP ip and was ok.
Now i try your way and i am not able to connect back,we miss some info(i will read more this night) or vpn provider has blocked incoming connections.
Your problem become mine also:)) maybe someone more skilled will give us a hand. -
It's not ISP problem in my opinion. I used TP LINK router connected with the same VPN service and everything worked fine, including port forwarding.
-
For starters actually post screenshot of your rules... If I had a nickel for every time user said they did X, when rules were actually Y, etc..
And then clearly state what you think is not working correctly... Which actual screen shots of your sniffs as the traffic hits your wan side interface and then doesn't get forwarded or is forwarded out your lan side interface to your IP, etc..
Or TLDR - RTFM!
https://www.netgate.com/docs/pfsense/nat/port-forward-troubleshooting.htmlThen come back with specific questions if you have some..
Why are you using manual nat? Just use hybrid to allow traffic to go out your vpn, etc. Post up your OUTBOUND nat tab..
-
Sorry, but I've been studying documentation for a couple of days till now where Im really stuck :(
Outbound rules:
Port forwarding:
and connected Firewall rule:
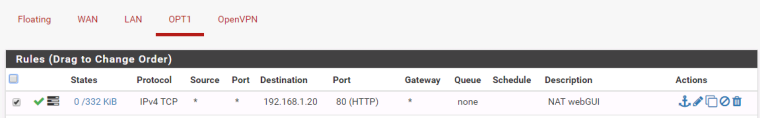
Firewall passes packets:
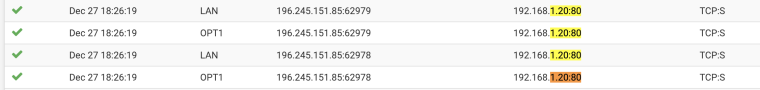
but blocks connections back:

and I dont know the reason because Im not filtering LAN to OPT1 connections: