Sonos speakers and applications on different subnets (VLAN's)
-
@Rai80 bingo!
That was it. Once I enabled that option in Firewall Rules for each VLAN segment configured in PIMD, I started seeing a lot more traffic in PIMD debug.
One more thing - all the above works with existing setup. Creating new Sonos network or adding new speakers doesn't work, as I read somewhere that pressing Play/Pause and Volume+ buttons doesn't get propagated between segments over multicast.
Since I already reset the controller, I needed one more step: I brought up a temporary WiFi SSID on the same VLAN as Sonos speakers, connect my Android phone to that WiFi and setup the Controller. After that, moving it back to the main WiFi SSID works and it still sees and controls speakers on a separate VLAN with PIMD running.
Now I'm happy. Thanks everyone for all the help!
PS. Would be nice to figure out how to setup new Sonos speakers w/o using the temporary SSID...
-
Nice that it works, but then I have to adapt the how to, as I explicitly mentioned that "allow IP options" was not needed and I can confirm that here I don't need to allow it, but my Sonos applications are not running on Andriod. Well, personally I don't understand why this is needed be that as it may, but the proof is in the pudding.
I added a second note to file.
Note 2: below is reported that on Android devices "Allow IP options" in the Advanced Options of the firewall rules is needed to enable to make it work, so if you don't have success, please try to enable it.
@denix now that it is working, can you confirm that when you quit PIMD, you can still connect to the Sonos speakers?
-
@Qinn yes, seems to be still working w/o PIMD running.
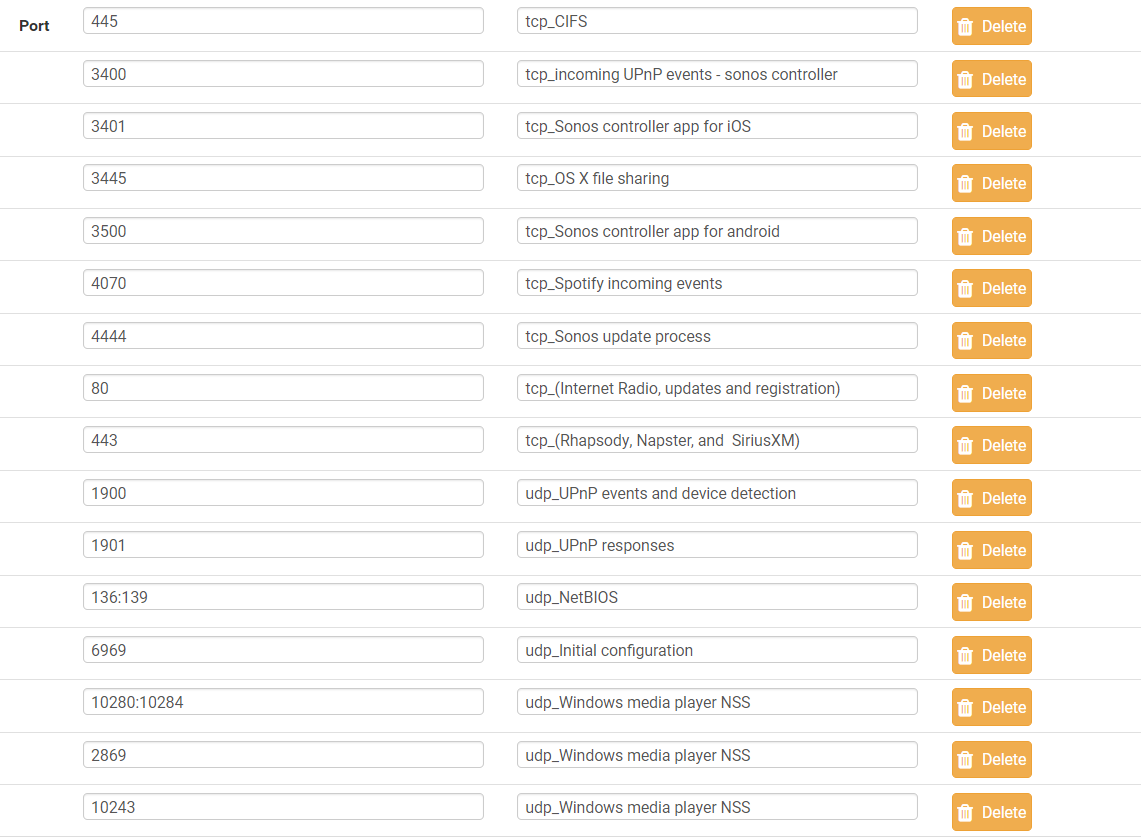
I also need to lock down the firewall between VLANs - currently I have those completely open to each other. Need to close and punch holes according to this list:
https://support.sonos.com/s/article/688TCP/IP:
80 (Internet Radio, updates and registration)
443 (Rhapsody, Napster, and SiriusXM)
445 (CIFS)
3400 (incoming UPnP events - Sonos Controller App for Mac or PC)
3401 (Sonos Controller App for iOS)
3445 (OS X / Windows File Sharing)
3500 (Sonos Controller App for Android)
4070 (Spotify incoming events)
4444 (Sonos update process)UDP:
136-139 (NetBIOS)
1900 (UPnP events and device detection)
1901 (UPnP responses)
2869, 10243, 10280-10284 (Windows Media Player NSS)
5353 (Spotify Control)
6969 (Initial configuration) -
@denix That was my conclusion also, thanks you have tested it, it seems that the applications save the addresses of the Sonos speaker for unicast, it's been 3 months that PIMD has been running and I can still access the speakers.
-
I'm at a loss... I think my issue is related to the TTL being set as 1 coming from the device sending the SSPD multicast. PIMD is setup exactly how you have it above and I'm still not seeing the traffic get through.
Does anyone know if there is a way to change the TTL for this type of traffic?
-
@pr3dict said in Sonos speakers and applications on different subnets (VLAN's):
I'm at a loss... I think my issue is related to the TTL being set as 1 coming from the device sending the SSPD multicast. PIMD is setup exactly how you have it above and I'm still not seeing the traffic get through.
Does anyone know if there is a way to change the TTL for this type of traffic?
Why do think this and what does a debug or log show?
-
This post is deleted! -
I tried to follow your guide (which is very clear and detailed), but I can't get it to work (not seeing any traffic).
Do you think it could be related to this https://forum.netgate.com/topic/140596/multicast-routing (TL;DR No IPv4 MROUTING kernel support.)?
-
@alexbond93 can you see pimd is running and config it so that, the interfaces carreing the vlan's containing speakers and the one containing Sonos software, are not disabled? Btw did you take a look at the remark @denix Apr 2, 2019, 12:57 AM I personally not needed it, but it seems to help him?
-
unfortunately i couldn't get this to work. from my pfsense i have a wired vlan to a wireless AP to which all IOT including Sonos speakers are attached. main LAN VLAN goes to a unifi edgeswitch and then onto all other devices either wired or through another wireless AP.
i got pimd installed and configured it just to disable the WAN interface. i could see pimd in top but couldnt ever get the Sonos speakers to show up in the Sonos app on a pc on LAN.
i didn't set anything related to ip settings on the firewall rules as suggested. my guess is its something in the edge switch blocking it but i've given up for now. hopefully Sonos fix this in a future update
-
@pr3dict said in Sonos speakers and applications on different subnets (VLAN's):
m at a loss... I think my issue is related to the TTL being set as 1 coming from the device sending the SSPD multicast. PIMD is setup exactly how you have it above and I'm still not seeing the traffic get through.
If TTL is set to 1 it's because the packet is not intended to be routed. This is often the case with multicast. So, when that packet tries to go through a router, the TTL will decrement to 0 and the packet discarded.
-
Thanks for the work here everyone!
I have a couple of cases where I need to traverse multiple routers with multicast. There might be a way to use pfsense for this after all. Right now its Cisco.
Think simulcast audio. https://www.gatesair.com/products/transport/public-safety-govt-communications
There are at least a couple other systems in the radio world that utilize multicast across subnets to distribute ROIP.
-
@chpalmer Nice that you appreciate this thread, I hope it helps many, but I don't understand what's your question. The main thing here is, that I have seen, using Wireshark that the default IGMP proxy pfSense uses, does not traverse Multicast 239.255.255.250 (SSPD) across subnets and PIMD does, so it is a more reliable when you want to "spread" local multicast over subnets/VLAN's, when it's multicast that comes from internet I think the IGMP proxy, that's by default present in pfSense it will suffice.
-
This post is deleted! -
@Qinn said in Sonos speakers and applications on different subnets (VLAN's):
I don't understand what's your question.
No question. Just a statement. :)
-
@chpalmer clear ;)
-
Qinn
Happy to report I got it to work! Took me months to sit down and take a look at this. It turned out to be much easier and simpler to implement than I thought.
Some notes:
- l have a netgate sg-3100 box. So the amd64 pkg threw an error. but it prompted me to use the armv6 package
pkg add http://pkg.freebsd.org/FreeBSD:11:armv6/quarterly/All/pimd-2.3.2.txz-
I didnt have to use Putty at all. I logged into the pfsense GUI and executed all the commands via diagnostics --> command prompt. This includes copying the pimd conf file over to /var/etc/ and starting it after editing.
-
To edit the conf file at /var/etc/pimd.conf, I used diagnostics ---> file edit. You can browse to it. very easy.
-
After starting pimd, it threw an error in the logs - permission denied. I figured it had something to do with the rules on my Iot vlan - where the sonos devices live. So i simply created the rule below, where home_devices is an alias of specific devices the sonos controller is running on - all assigned with static ips, of course. Dont know if I need ipv6 there or not but i added it in anyway. The, sonos_ports is a list of all the ports shown in the link you provided. I threw it all into one big bucket.
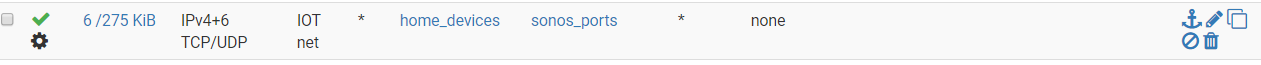
- I also enabled "allow ip options" under advanced options in the rule above.
Thats it!
Some issues:
-
I rebooted my pfsense box after I was done. When i logged back in, the pimd package in /var/etc/ was gone! I tried to start it but couldnt find it. So i copied it over again, edited it and started it. But haven't rebooted my box again! Not sure if I did something wrong the first time.
-
I'd like to clean up that list of sonos ports. I think some of them are intended for outbound to sonos servers and some jsut for the internal lan. No need to open all those ports to my internal lan devices. So, id like to identify which ones are outbound and which ones are for the devices on the lan only.
-
A bit of a pain to have to redo this everytime there is a pfsense upgrade. I hope pimd makes it as an official package.
-
I have upnp enabled. Not sure if turning it off will impact any of this.
Anyway ... thought i should check in to report my progress after your excellent work to get things started!
-
@vacquah Great, that you finally got it to work and thanks for reporting back and sharing the how you did it. Also, nice that you pointed out, one can also make use of the Command Prompt which is in the GUI of pfSense . I didn't know that, apart of the Amd64 version there is an Arm version, pointing it out will help many

As this thread is getting bigger, I would like to emphasis on something, I noticed that once the Sonos apps and speakers have found each other, there is no more need for running PIMP (maybe after a reboot, I have tested that) to be running. It seems the addresses are somehow stored and as these are closed source apps and devices, I have not much chance of finding out on the "how to". I just say this, not that I don't trust PIMD, but somehow introducing a not approved piece of software on a firewall/router, just doesn't feel right.
News:
https://forum.netgate.com/topic/139352/pimd-a-lightweight-standalone-pim-sm-ssm-v2-multicast-routing-daemon/2 -
This is a great little tool for testing of multicast streams.
https://support.singlewire.com/s/software-downloads/a17C0000008Dg7AIAS/ictestermulticastzip
Simply launch the program one on the transmit side and one on the receive side and set accordingly. If multicast is making it then you will see the packets on the screen.
-
I have also tried to enable multicast with pimd, but when I try to run the command
pimd -c /var/etc/pimd.confusing Diagnostics-> Command Prompt, but in return I get
pimd: 09:35:36.449 Another multicast routing application is already running.I don't know which application it is referring to. I have disabled imgp proxy. Avahi is running for Bonjour/Airprint.
This is the output of command
top:PID USERNAME THR PRI NICE SIZE RES STATE C TIME WCPU COMMAND 56564 root 1 23 0 100M 45504K piperd 2 0:14 1.56% php-fpm 342 root 1 52 0 125M 45056K accept 3 0:20 0.00% php-fpm 44824 root 1 52 0 98M 43360K accept 3 0:11 0.00% php-fpm 92301 root 1 20 0 6400K 2596K select 1 0:09 0.00% syslogd 13534 root 1 20 0 6600K 2384K bpf 2 0:08 0.00% filterlog 31176 root 5 52 0 6900K 2328K uwait 0 0:06 0.00% dpinger 343 root 1 52 0 96212K 40816K accept 2 0:05 0.00% php-fpm 7830 root 1 52 0 102M 46028K accept 3 0:04 0.00% php-fpm 10260 root 1 52 0 98196K 42616K accept 3 0:04 0.00% php-fpm 48403 root 1 20 0 23592K 8956K kqread 2 0:01 0.00% nginx 20083 root 1 52 20 6968K 2656K wait 2 0:01 0.00% sh 49387 nobody 1 20 0 11524K 5248K select 0 0:01 0.00% dnsmasq 48583 root 1 20 0 23592K 8540K kqread 1 0:00 0.00% nginx 49607 root 1 20 0 12396K 12500K select 1 0:00 0.00% ntpd 94937 squid 1 20 0 99928K 35228K kqread 0 0:00 0.00% squid 77963 root 1 20 0 6324K 2324K select 3 0:00 0.00% pimd 86583 dhcpd 1 20 0 12580K 8300K select 1 0:00 0.00% dhcpd 1370 squid 1 20 0 9948K 5088K select 0 0:00 0.00% pingerHow can I identify the conflicting application?

