Best Practice for Guest Network
-
@mecjay12 said in Best Practice for Guest Network:
I have all the rules that allow unpriv/Internet access to the priv network on the WAN.
Huh? Rules on WAN have zero to do with a user on one of your networks going to the internet... Rules on the WAN have to do with unsolicited inbound traffic FROM the internet.
If you are creating rules on the WAN to allow your users to access the internet your doing it wrong!!
-
@NogBadTheBad Thanks for your time. I didn't think of that. Floating rules will be better than what I have now but not ideal. If I add a new interface/vlan, I have to go through and modify every rule to add the new interface. I will make a note but keep looking for a better solution.
@johnpoz You misread. Mu unpriv networks all have one rule that says "accept all, gateway wan". They cannot access the other networks at all because all their traffic is shuffled out the WAN regardless. It was originally setup this way because my thought process was that if it goes out the WAN then it has to come back in the WAN to get to the priv network. If it comes in the WAN it goes through the rules that I want it to go through. Clearly this is incorrect. Once the traffic gets shuffled to the WAN it won't return.
The quote you took is referring to states that I want all traffic to go through the rules on the WAN interface before it gets to the priv network. Since I want my unpriv networks to be treated the same as Internet traffic I want my networks to follow the same rules as I have on the WAN before getting to the priv network. -
You could just copy an existing rule and change the interface.
To be honest I like to see firewall rules on the actual interface rather than floating rules.
-
That will inevitably cause asymmetric rules. This firewall has upwards of 500 rules and 3 people making changes.
-
Sounds like you have a MESS to be honest, and don't actually understand how rules are processed either.. Sending traffic out a specific gateway is not proper firewalling..
-
@johnpoz Ok, how would you do this? 6 networks. 2 are WANs, 2 are unpriv LANs, 2 and priv LANs. The First unpriv LAN has whitelist Internet access via the first WAN. The Second unpriv LAN is a guest network that has full Internet access via the first WAN. Both unriv LANs should only have access internally if they follow the firewall rules that any other Internet user can. The priv LANs should have access wherever they need. One is a network of private IPs and the other is public IPs route to the firewall. We only have one firewall cluster handling this task. It used to be Fortinet firewalls, now we are trying to transition to pfSense. How would you do it?
-
It’s hard to read your posts, any chance you could use the return key ;)
Maybe draw us a diagram.
-
@mecjay12 said in Best Practice for Guest Network:
How would you do it?
You have not stated anything of complexity there at all.. You have a couple of routed netblocks.. Great - those firewall just like anything just not natting.
While you might want to push traffic out a specific wan.. You would not use that as firewalling, you would actually create the specific rules blocking want you block before you allow the traffic out the specific wan network, etc.
Its all fine and good to policy route, but that is not a firewall rule in itself, its just a way to route traffic based on policy..
6 networks... I have more than on my home network... heheeh
That you have 500 some rules on your firewalls, with only 6 networks... Seems like someone doesn't understand something here that is for damn sure, especially if your firewalling via a policy route..
-
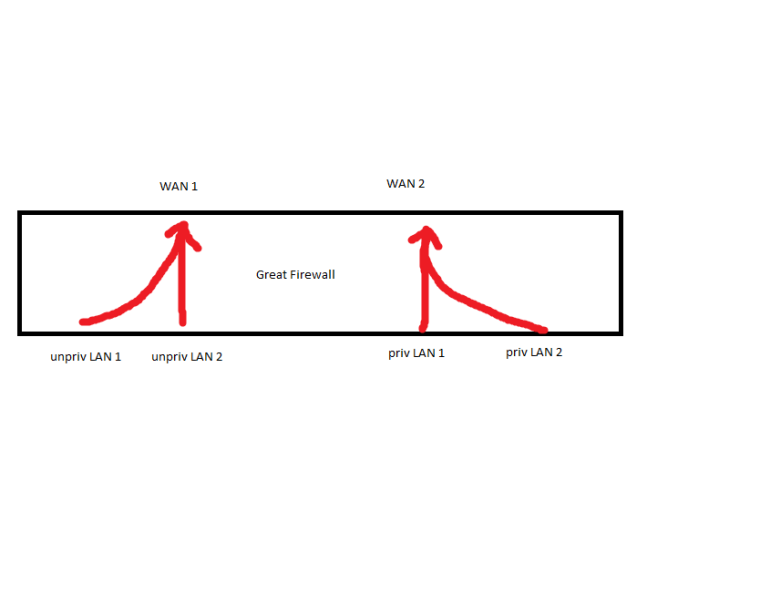
Requirements:
Both unpriv LANs go out WAN 1.
WAN 1 has no inbound traffic, only established traffic.
Both priv LANs use WAN 2 for outbound traffic.
There is inbound traffic to the priv LANs. The access rules are the same for unpriv LANs and Internet users the same.
Must be easy to add new interfaces/vlans later and no duplicate rules (to prevent one rule getting updated or created without another).
Current setup:
Both unpriv LANs are policy routed out WAN 1.
WAN 2 is the default gateway (I don't like this).
All inbound firewall rules for priv LANs are on WAN 2 (not floating).
Both priv LANs have allow all rules.
Both unpriv LANs were EXPECTED to egress WAN 1 then immediately ingress WAN 2 and filter through WAN 2's rules. (not functioning).
Potential solutions:
Replace WAN 2 inbound rules with floating rules for 'in' on each unpriv interface. Should fix immediate problem but be a pain if/when a new interface/vlan is added (would have to modify every rule).
Replace WAN 2 inbound rules with floating rules for 'out' on priv interfaces. Unsure if this would work because traffic getting blocked on ingress? Need to test.
-
You maybe could look at Interfaces -> Interface Groups
"Interface Groups allow setting up rules for multiple interfaces without duplicating the rules.
If members are removed from an interface group, the group rules are no longer applicable to that interface."https://www.netgate.com/docs/pfsense/interfaces/interface-groups.html
You'd just need to add any new interface / vlan to the group or floating rule.