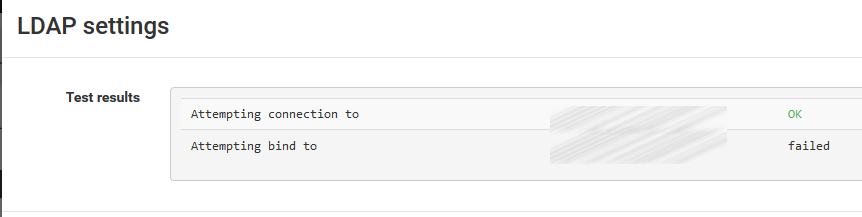
2.4.4_2 ldap with ssl failure
-
Hi @ all,
the new version 2.4.4_2 seems to have an issue with the ldap ssl connection and an active directory backend. I got the following output after the update from 2.4.4_1 to 2.4.4_2:

In the system logs i see the following message:
Jan 8 14:51:56 php-fpm 950 /index.php: ERROR! Could not bind to LDAP server dc01. Please check the bind credentials.Without using ssl there is no issue!
On my other cluster node, which has still version 2.4.4_1 everything works well.
Is there anybody who has a clue whats the problem?
If not, i might discovered a bug ... -
Nothing changed in LDAP between -p1 and -p2, so that should all work the same.
Can you check the AD logs to see what it believes the problem may be?
-
@jimp
Here is the event log entry from the domaincontroller:unknown_ca Received a valid certificate chain or partial chain, but the certificate was not accepted because the CA certificate could not be located or could not be matched with a known, trusted CA. This message is always fatal.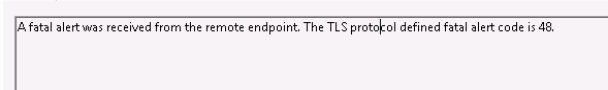
I have not changed any certificate or CA on the pfsense webgui. When i use the older version everything works very well.
-
Any ideas?
-
Nothing changed in the SSL or CA setup on -p2 either. My TLS LDAP setup is still functioning, even on 2.4.5 snapshots.
Do you have the correct CA chosen for the LDAP certificate in the LDAP server settings? I am using an LE cert on my LDAP server, so I use the Global Root CA List choice.
If you make a change to the LDAP SSL settings, it's a good idea to use options 16 then 11 in the console (ssh or video/serial) to ensure PHP gets the environment setup properly.
-
@jimp
I will reimport the Root CA Chain. What about the ldap log patch which you have created:
Is it still working with 2.4.4 ?
I got the following error: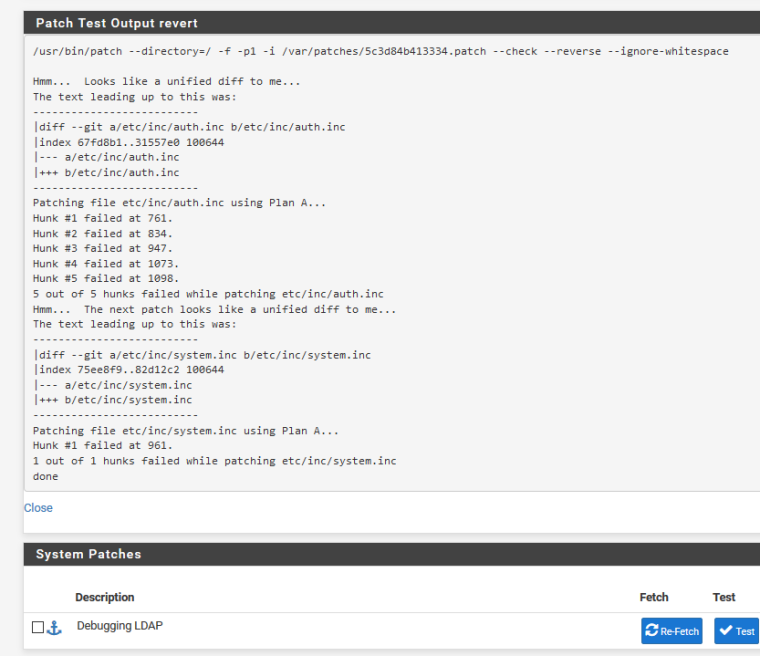
-
No, that patch doesn't work. I haven't looked into turning that on in recent versions, that patch is super old.
A packet capture of the exchange should show you the certificates being sent between client and server.