OpenVPN direct connection to Static IP desktop MAC address
-
Hello,
I have completed the OpenVPN set up on our pfSense firewall and exported the OpenVPN client utility package.
My question is once the external client installs the utility package and connects into our office LAN how do I route the connection in the tunnel directly to a specific computer which I have assigned a static IP to in the DHCP server ?
In order for the user to operate on this local PC after getting into our network because of printing they must use our MFP within our network domain.
This is my first time working with VPN so I am unsure as to get from their endpoint on their desktop OpenVPN application to the specific PC after a random local port is used to pass the client traffic into our LAN in our office.
Thank you.
-
Your OpenVPN RAS Client can connect to any internal network resource by it's local IP, just the same IP you use in the LAN. But you need to setup your Firewall Rules (OpenVPN Tab).
OpenVPN does not care if the target system you want to reach is some PC, Server, MFP and so on.-Rico
-
Rico I appreciate the information but I still do not full understand.
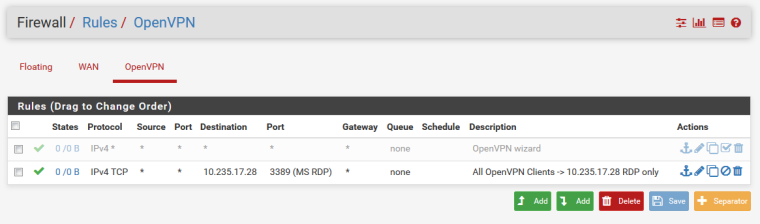
So in order for a remote IP to come through and go directly to a target resource I must set that up in the Firewall Rules such as has been done by the previous network admin before I took over as shown below...I am trying to get IP .28 and .29 off of MS RDP and onto OpenVPN for security.
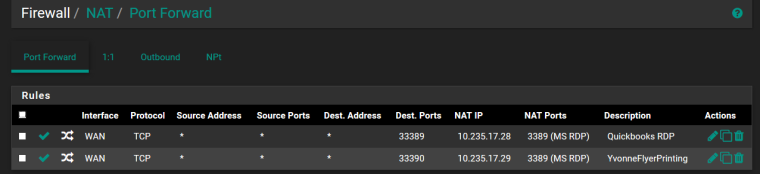
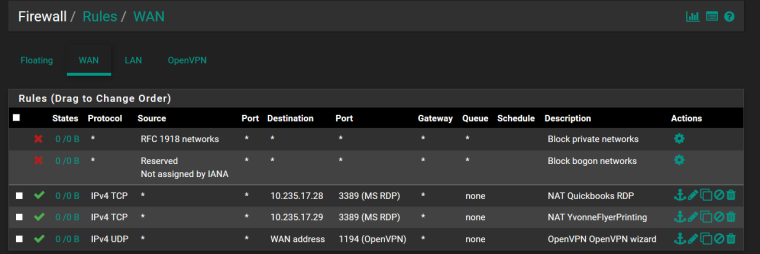
It appears that the OpenVPN rule was set by default when I completed the configuration.
Must I add the info in the Firewall NAT for the external client get to LAN IP 10.235.17.28 after entering through our WAN gateway for example?
Also I did get the TLS handshake failed after testing the exe installation openVPN desktop app so I must troubleshoot that as well.
-
To let traffic flow inside the OpenVPN network you need to add Firewall Rules in your Firewall -> OpenVPN tab
When you run the OpenVPN Wizard in the last step there is one checkbox, then the wizard will add some any-any Rule for you:
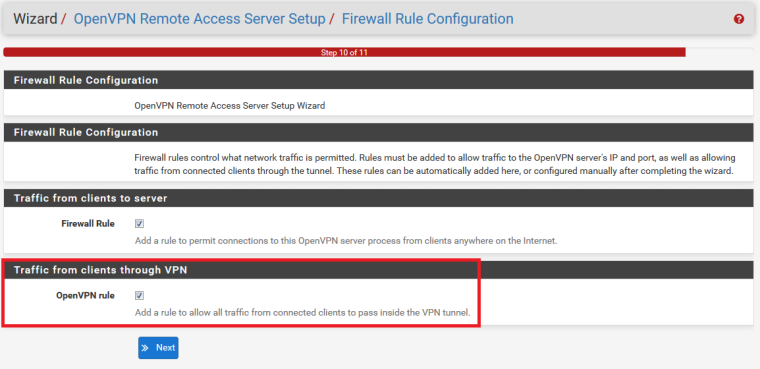
This will create:
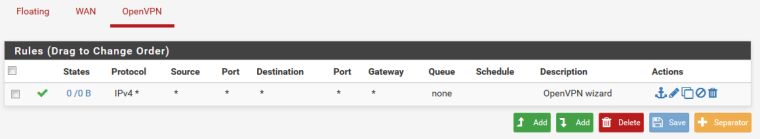
For security reasons, if you want only RDP to one server from all clients you can narrow this down:
For general problems like your TLS handshake error you can consider https://www.netgate.com/docs/pfsense/book/openvpn/troubleshooting-openvpn.html
There are also great Netgate video tutorials on OpenVPN Remote Access to give a better understanding and great tipps & tricks:
https://www.netgate.com/resources/videos/remote-access-vpns-on-pfsense.html
https://www.netgate.com/resources/videos/remote-access-vpns-on-pfsense-part-2.html-Rico
-
Rico,
I am resorting to https://www.netgate.com/resources/ videos for making another attempt at this.
The firewall NAT and rules are in place for OpenVPN and I do not think that is the problem.
I am just unsure whether to set up OpenVPN server mode as remote access, site-to-site, or WAN.
I am unsure about as well as the client export. Maybe Interface IP addresses?
The interesting thing with this is that MS RDP is also not working anymore for another remote microsoft box with the same wan static ip and destination port notation as before after we moved offices and were issued a new fiber circuit ID from att and they shifted some IP schema (WAN/IPv4 Lan block) while migrating LAN IPs within our gateway.
The external PCs for these remote employees are in other parts of the world but the problem is that we have an ATT managed router and thus it could be interfering with the VPN tunnel. I am almost sure the DGW is correct and we have a static IPv4 address on the WAN interface in our firewall but have not been able to verify as I have been trying to get into contact with the AT&T Lifecycle managed internet services engineers in India to no avail. For being a mega tech giant att data engineers resources are so frustrating. They shift some things and don't communicate to network admins unless you probe them incessantly! My sales account exec and service manager is also practically useless with this matter.