Mobile IPSec VPN works but does not follow 302 redirects
-
I have a very odd problem, I have a pfsense firewall that is serving IPSec VPN to my mobile phone (Pixel XL, Strongswan VPN). The VPN works fine in that I can connect, reach the internet and the internal LAN webservices.
The one thing that doesn't work is to login on some of my hosted webservices, and I think it is because 302 redirects are not sent back / followed to the mobile device.
When I try to login to a service I expect to see this in the apache2 access logs:
The POST 302 redirect for the LOGIN when submitting user+password:
11.0.0.0 - - [01/Feb/2019:07:36:08 +0100] "POST /login HTTP/1.1" 302 2137 "https://web1.example.com/" "Mozilla/5.0 (Android 6.0; Mobile; rv:60.0) Gecko/20100101 Firefox/60.0"
The client follows the redirect and requests the dashboard post successful login:
11.0.0.0 - - [01/Feb/2019:07:36:09 +0100] "GET /dashboard HTTP/1.1" 200 2159 "https://web1.example.com/" "Mozilla/5.0 (Android
6.0; Mobile; rv:60.0) Gecko/20100101 Firefox/60.0"What I actually see is only the first piece:
The initial 302 is sent back but the client doesn't respond, and I get a timeout after a long time:
11.0.0.0 - - [01/Feb/2019:07:49:17 +0100] "POST /login HTTP/1.1" 302 1976 "https://web1.example.com/" "Mozilla/5.0 (Android 6.0; Mobile; rv:60.0) Gecko/20100101 Firefox/60.0"
I have set up very permissive firewall rules so far in pfsense for the IPSec VPN (i.e. allow all). That is why it works to surf to the internet and any internal webservice.
I wonder if I need to do some NAT setting? I had to manually open the 4500 and 500 firewall ports so might be that NAT is not correctly setup?
-
Hey
Need to see what show
/diagnostics/ packet capture
Interface Lan
Host Your problem host
Protocol any
Port your problem portand we still need a file (download capture)
or
Try the same
https://forum.netgate.com/topic/140209/tcp-issue-inside-the-tunnel/10 -
@Konstanti thanks so much for responding!
I tried the MSS Clamping but it did not help, I did the packet capture and attach the packet capture file. Can't read much what it means but hope it tells you something. Let me know if there is anything else I can provide to help with the debugging. Really appreciating your help!
PS. Had to .zip the file as the forum refused to upload the .cap file...
-
That shows 11.0.0.0 successfully connecting to 192.168.0.98 twice.
We can't see the actual redirect or URLs being connected to there because it's all wrapped in TLS.
(What is 11.0.0.0? Are you asking about help with a US Department of Defense VPN?)
-
Very strange address 11.0.0.0
What's it?
so is nat configured ?
And I see that the connection attempt is repeated twice
And used tls, it is difficult to understand what the problem is ((((( -
This post is deleted! -
Looks like TCP is working fine to me. Not sure why that would help.
-
It's just a hypothesis.
I am very confused by the address 11.0.0.0 -
Clicking checkboxes without knowing why is how people get something checked that comes back to bite them later and is almost impossible to find.
-
This checkbox has already helped a lot of people. It is necessary to see the configuration of the topikstarter to understand whether it can help him or not (often the problem of checksum tcp is faced by the owners of realtek network cards)
But I also don't see any problems with tcp in packetcapture file -
@Konstanti @Derelict thanks a lot for looking through this.
11.0.0.0 is weird I agree, I just put this as the virtual IP address for client and when I generated an certificate (I followed this guide: https://www.netgate.com/docs/pfsense/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html) and connected with my Andriod phone this is the IP that it connects through.
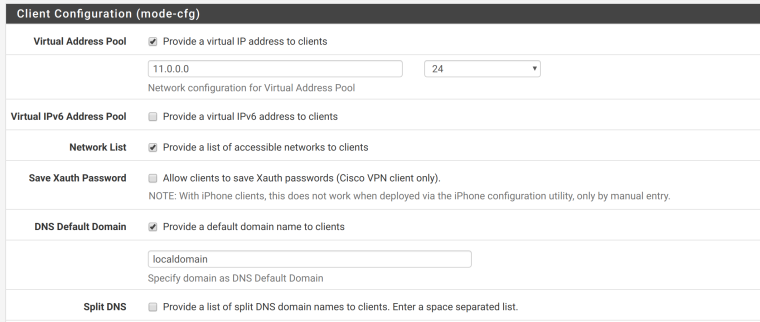
Perhaps I did a mistake there? To my knowledge, I have not configured any NAT rules for the IPSec VPN server, see below. (Please note, I have my pfsense set up as a OpenVPN client, so there are some NAT rules but that is for a different VPN).
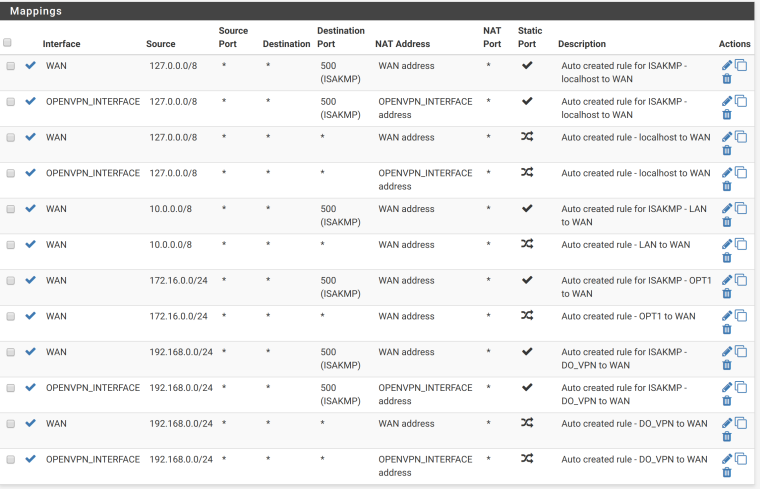
-
This is not entirely correct
It is better to assign addresses from the allowed list (private ip address)
10.0.0.0/8
172.16.0.0/12
192.168.0.0/16for example, 192.168.30.0/24
and then for this network, you can create a NAT outbound rule
for example ,
ipsec mobile client settings
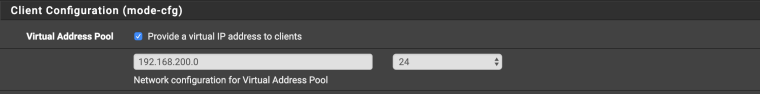
and
nat outbound
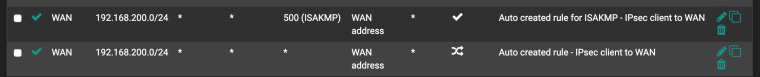
-
This post is deleted! -
- You can open the strongswan app log and see which ip is assigned
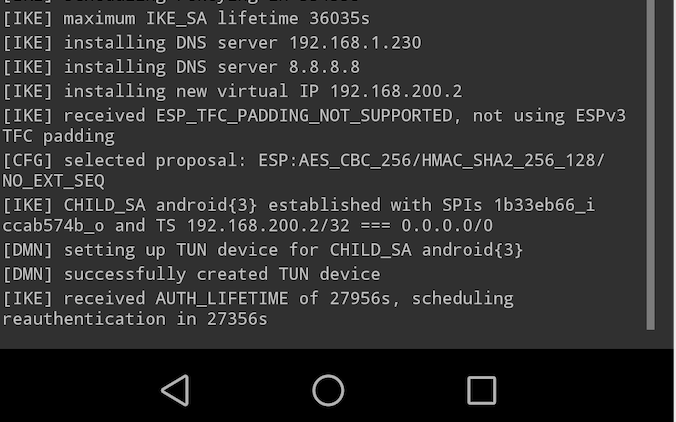
or
2. /status/ipsec/leasesor
3. Status/System Logs/IPsec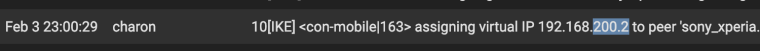
- You can open the strongswan app log and see which ip is assigned
-
@Konstanti Thanks man, I managed to reassign the virtual IP and set up the NAT as you mentioned, however it is still not working.
0_1549227415987_packetcapture_2.zip
I attach a new packet capture. Could it be something with the Unbound DNS Resolver? I am resolving the app1.example.com to IP 192.168.0.98 through pfsense Unbound DNS resolves. It works on all my other devices but is
there something special with IPSec VPN Mobile Clients? I read somewhere that I had to set the Outgoing Network Interfaces to LAN and Localhost for it to work over VPN, so did that already.DNS Resolver:
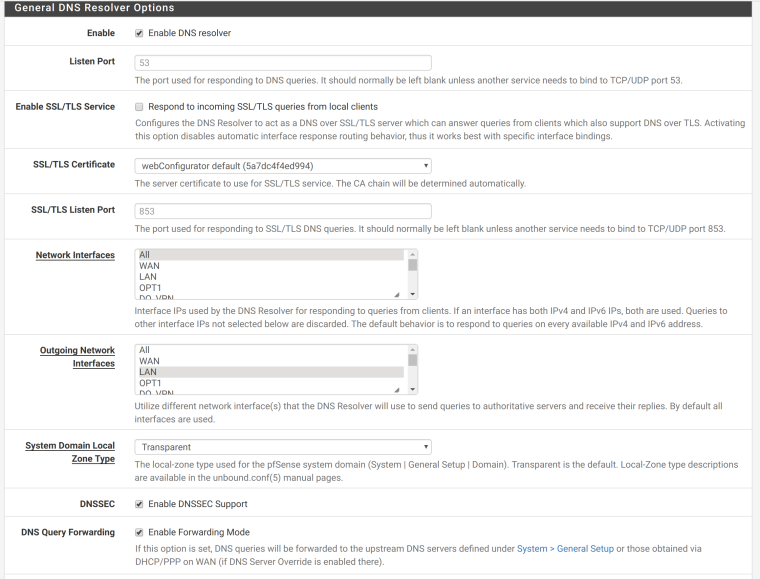
-
@svarto
Packetcapture file empty -
And don't filter on anything but the host address so we can see the DNS queries.
-
0_1549228302261_PacketCaptureontwointerfaces.zip
@Konstanti @Derelict I created two packetcaptures on the two separate interfaces, filtering for the android IPSec VPN client as Host (i.e. 192.168.200.1)
Should be something in the files now...
-
@Konstanti @Derelict What is very peculiar is that when I am connected to the Wifi on my phone, and then connect through the IPSec VPN. Everything works. When I am not on the internal network but on 4G on my phone, and connect through the IPSec VPN - it doesn't work.
See packetcapture from being on the Wifi and connected through VPN and everything works:
0_1549229309189_IPSecInterfaceonWifiallworks.zip -
Doesn't do any good to look at pcaps of it working without one of it not working to compare it to.