Block layer 7 on websites
-
Snort and the openappid streaming media rule.
-
Thanks @NogBadTheBad
Do you know if there is any documentation available on how to create this rule?
-
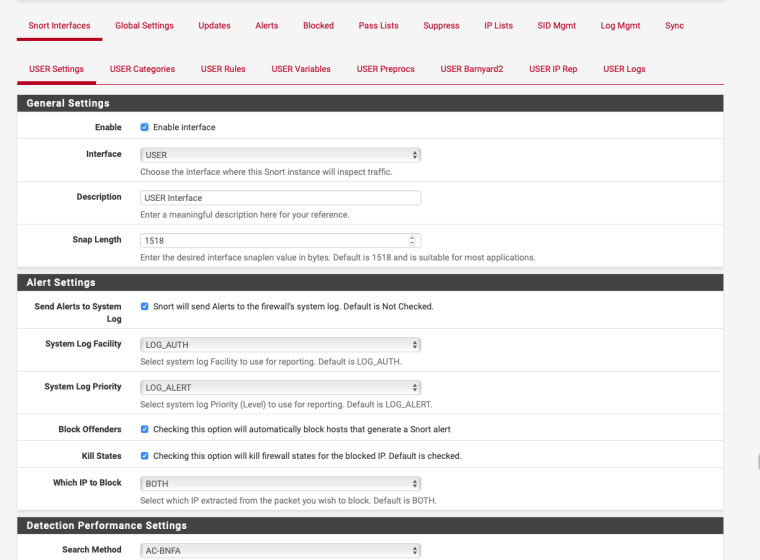
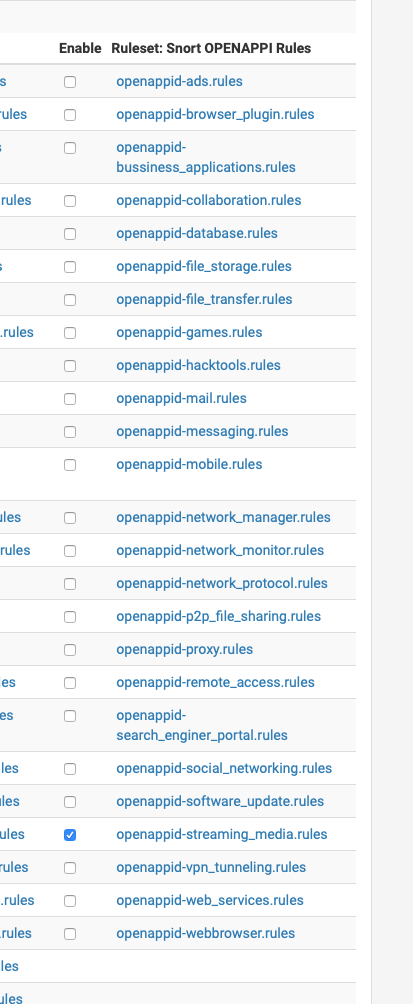
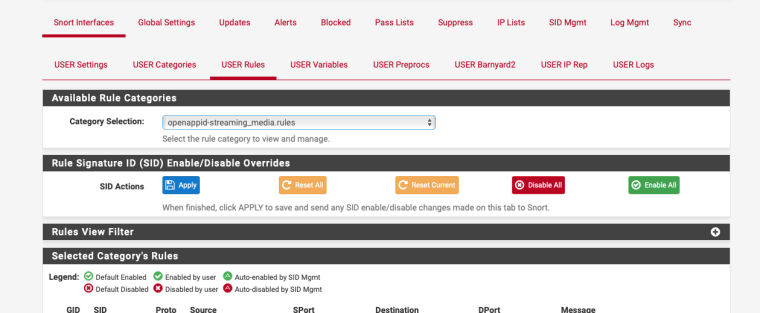
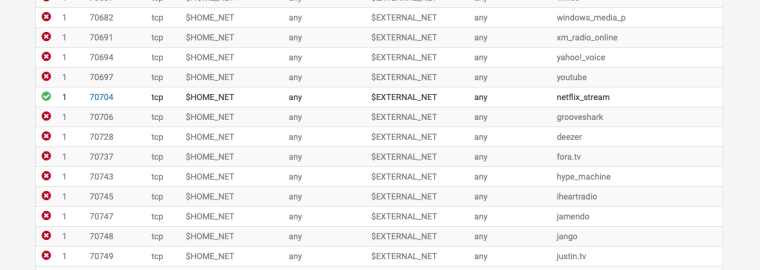
The rules are there, i think you need to select it then unselect everything you want to pass in the actual rule.
Then enable blocking in the interface.
-
-
Brilliant m8. Thanks for the input. Much appreciated. It works perfectly :)
Now I'm trying to see whether you can manually add rules to the list because there were some embedded video players that weren't blocked since there were no signatures combined to them.
-
@dma11 said in Block layer 7 on websites:
Brilliant m8. Thanks for the input. Much appreciated. It works perfectly :)
Now I'm trying to see whether you can manually add rules to the list because there were some embedded video players that weren't blocked since there were no signatures combined to them.
Provided you know and follow the required syntax, you can create your own custom rules and add them to the list of enforced rules in Snort. Go to the RULES tab (first EDIT an interface and then choose the RULES tab) and choose Custom in the Category selection drop-down. Type your rules into the text area box. Save them and restart Snort on the interface.
-
@bmeeks said in Block layer 7 on websites:
@dma11 said in Block layer 7 on websites:
Brilliant m8. Thanks for the input. Much appreciated. It works perfectly :)
Now I'm trying to see whether you can manually add rules to the list because there were some embedded video players that weren't blocked since there were no signatures combined to them.
Provided you know and follow the required syntax, you can create your own custom rules and add them to the list of enforced rules in Snort. Go to the RULES tab (first EDIT an interface and then choose the RULES tab) and choose Custom in the Category selection drop-down. Type your rules into the text area box. Save them and restart Snort on the interface.
hi bmeeks;
Can you share a sample packet listening and blocking path detail. chrome, opera, firewfox vpn apps etc. (not the rule listed, the new custom rule)
thanks. -
@susamlicubuk said in Block layer 7 on websites:
@bmeeks said in Block layer 7 on websites:
@dma11 said in Block layer 7 on websites:
Brilliant m8. Thanks for the input. Much appreciated. It works perfectly :)
Now I'm trying to see whether you can manually add rules to the list because there were some embedded video players that weren't blocked since there were no signatures combined to them.
Provided you know and follow the required syntax, you can create your own custom rules and add them to the list of enforced rules in Snort. Go to the RULES tab (first EDIT an interface and then choose the RULES tab) and choose Custom in the Category selection drop-down. Type your rules into the text area box. Save them and restart Snort on the interface.
hi bmeeks;
Can you share a sample packet listening and blocking path detail. chrome, opera, firewfox vpn apps etc. (not the rule listed, the new custom rule)
thanks.Sorry, I am not a rule writer. Never bothered to learn the syntax in detail. You should be able to find some examples with a Google search, and then maybe build off the rules included in the OpenAppID package with pfSense.
-
@NogBadTheBad Does this also block all the video streaming apps installed on smart phones (etc. tiktok, likee, snackvideo and other like these)?
-
You're waking up forum threads more then 4 years old ...
Much has changed since then. -
@Gertjan you are right. please guide how can I block streaming apps installed on smart phones using pgblockerNG or snort.
-
@ammar177 Using pfBlockerNG. Create an alias of ASNs you want to block (netflix,hulu,peacock,etc..). Apply that alias to the IPs that should be blocked.
There isnt a clean way to block streaming sites on pfsense. Snort openapp.id rules have not been updated in some time (over 5 years) so they will not account for the latest streaming sites. You will need to write your own rules for that.If you are looking to block streaming media sites on a phone its probably best to point that client to openDNS or NextDNS where you can do category-based blocking and not use pfSense for DNS. That's the best recommendation i can give.