SNAT From OpenVPN user to a IPSec tunnel possible?
-
Hello,
First topic here, hope I am following the rules.I have a 2.4.4-p2 PFSense Box with a OpenVPN server and some IPSec tunnels configured.
My LAN subnet is 10.25.16.0/21 and my OpenVPN client subnet is 10.25.26.0/23 (large subnets, I know :S )I have an IPSec tunnel that has my LAN subnet (10.25.16.0/21) on a single Phase2 and now I need that my OpenVPN clients (10.25.26.0/23) access the remote subnet of this tunnel (10.80.242.0/24)
I have to access the remote subnet but the remote subnet doesn't need to access my sides. So the VPN tunnel just need to be one way.The question is, can I do this without adding a new Phase 2 to the VPN?
I would think that a SNAT from my OpenVPN LAN to route that subnet trough the tunnel would be somewhat possible. Am I thinking this wrong?Thank you for your time!
Best regards,
John -
Try so
https://forum.netgate.com/topic/140435/can-a-remote-vpn-user-client-access-other-vpn-ipsec-site-to-site/3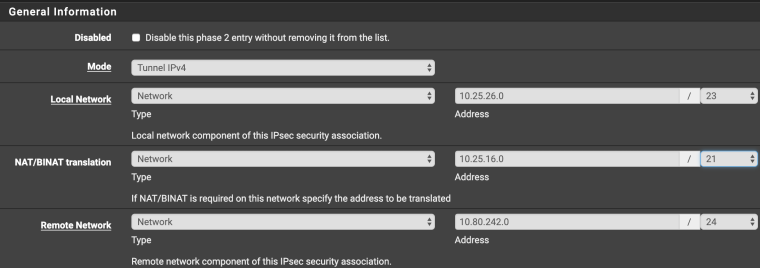
-
Thank you so much for your quick answer.
However on your example config I'm able to reach the remote subnet but only if I am on the OpenVPN subnet. LAN clients can't reach it.
I tried swapping the subnets between "Local Network" and "NAT/BINAT translation" and it seems that the clients connected under the "NAT/BINAT translation" can't reach the other end.For confirmation, the Firewall Rules created to allow this traffic are accusing hits, so I guess it's a routing issue.
-
@johnpulse
Try adding this as a second phase 2 on the pfsense side.
See link ( post 3) -
@johnpulse
Here are my test settings
Lan 10.10.25.0 - lan with binat
binat on enc0 from 10.10.25.0/24 to 192.168.15.0/24 -> 10.0.3.0/24
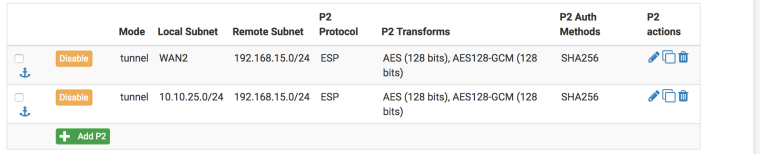
Second side
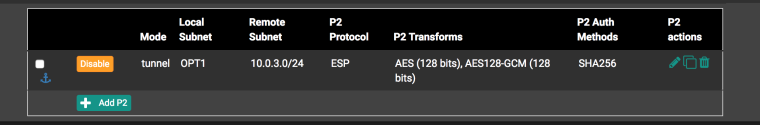
Connection status
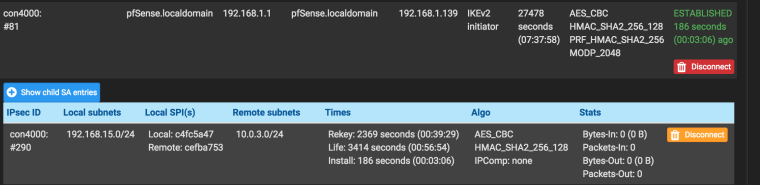
-
I have to admit, when I saw your post I thought that having a different number of Phase 2's on both sides would never work!
However, it worked perfectly! I can now reach the other side from both my LAN subnet and my OpenVPN subnet.
I cannot thank you enough, it was stupid of me trying to crack this one up for so long (weeks literally) when it was so fast to get awesome help here.Hope you have a perfect weekend. Thank you so much for giving me your time and even by trying the setup on your LAB.
Regards,
John