IKEv2 IPsec VPN with pfSense and Apple devices
-
I know zero about VPN setup so I am behind the eight ball here to begin with...
My goal is to setup a "road warrior" VPN. That is without any additional software installed on a vanilla macOS device and on a pure pfSense system (not running any kind of authentication server) allow someone to install an Apple Configurator Profile onto their system and VPN to the remote network for full access.
I am running the latest version on both sides: macOS Mojave 10.14.3 and pfSense 2.4.4-RELEASE-p2. I have followed these various tutorials:
IKEv2 IPsec VPN with pfSense and Apple devices
Valid configuration for IKEv2 VPN for iOS and OSX
pfSense IKEv2 for iOS/macOS
IKEv2 with EAP-TLSAll of which are extremely similar if not identical. Yet, when I try to connect from macOS it immediately fails with a dialog saying "User Authentication Failed."
I have gone through the setup several times on the pfSense side checking all settings and making some minor tweaks based on the various tutorials but have been getting no where. I have tried the profile (it installs the CA, the server cert, and the client p12, and the VPN setup fine) on two different macOS systems and even a VMWare blank macOS install. I have recreated the certificates several times and am almost to the point where I do not need to look at the tutorial information anymore to populate the setups.
Yet, the best progress I have made to date has been turning this:
default 08:00:02.859513 -0500 neagent Verifying the signature of plugin at file:///System/Library/Frameworks/NetworkExtension.framework/Versions/A/Resources/PluginIKEv2.vpnplugin/
default 08:00:02.865057 -0500 neagent UNIX error exception: 17
default 08:00:02.868914 -0500 neagent UNIX error exception: 17
default 08:00:02.872107 -0500 neagent UNIX error exception: 17
default 08:00:02.887727 -0500 neagent Plugin satisified designated requirement: identifier "com.apple.neplugin.IKEv2" and anchor apple
default 08:00:02.957000 -0500 neagent UNIX error exception: 17
default 08:00:02.962717 -0500 neagent UNIX error exception: 17
default 08:00:02.965160 -0500 neagent UNIX error exception: 17
default 08:00:02.967447 -0500 neagent UNIX error exception: 17
default 08:00:02.970169 -0500 neagent UNIX error exception: 17
error 08:00:03.043895 -0500 neagent BACKTRACE failed to retrieve remote CA cert data by CN (raymonds.com-vpnrootca )
error 08:00:03.070948 -0500 neagent Auth initiator received notify error: Error (Authentication Failed)
error 08:00:03.071017 -0500 neagent Failed to process IKE Auth packetInto this:
default 08:16:17.767721 -0500 neagent Verifying the signature of plugin at file:///System/Library/Frameworks/NetworkExtension.framework/Versions/A/Resources/PluginIKEv2.vpnplugin/
default 08:16:17.778135 -0500 neagent UNIX error exception: 17
default 08:16:17.783161 -0500 neagent UNIX error exception: 17
default 08:16:17.786802 -0500 neagent UNIX error exception: 17
default 08:16:17.804362 -0500 neagent Plugin satisified designated requirement: identifier "com.apple.neplugin.IKEv2" and anchor apple
default 08:16:17.889116 -0500 neagent UNIX error exception: 17
default 08:16:17.892719 -0500 neagent UNIX error exception: 17
default 08:16:17.898315 -0500 neagent UNIX error exception: 17
default 08:16:17.900654 -0500 neagent UNIX error exception: 17
default 08:16:17.903365 -0500 neagent UNIX error exception: 17
default 08:16:17.989758 -0500 secd neagent[6734]/1#3 LF=0 copy_matching Error Domain=NSOSStatusErrorDomain Code=-50 "query missing class name" (paramErr: error in user parameter list) UserInfo={NSDescription=query missing class name}
default 08:16:17.990384 -0500 secd neagent[6734]/1#3 LF=0 copy_matching Error Domain=NSOSStatusErrorDomain Code=-50 "query missing class name" (paramErr: error in user parameter list) UserInfo={NSDescription=query missing class name}
error 08:16:18.022168 -0500 neagent Auth initiator received notify error: Error (Authentication Failed)
error 08:16:18.022187 -0500 neagent Failed to process IKE Auth packet (connect)And I am not 100% sure which change I made with the certificates to do this. I could upload images of my cert setups but they are identical in form to ones shown in the "pfSense IKEv2 for iOS" link above.
If I block access to the remote pfSense device I get the same failure behavior so I am kind of assuming macOS is not even reaching the point to try to connect.
I am at the total loss of how to debug this further since I believe I have deleted and recreated the certs to the point where I have "tried everything." I even shared my exact setup with the author of the "IKEv2 IPsec VPN with pfSense and Apple devices" link above and he does not see anything wrong with what I am attempting to do.
-
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.html?highlight=vpn.<< I followed this.
You may have an issue with self signed certs and Apple Configurator.
I imported my CA and VPN cert, trust the root CA.
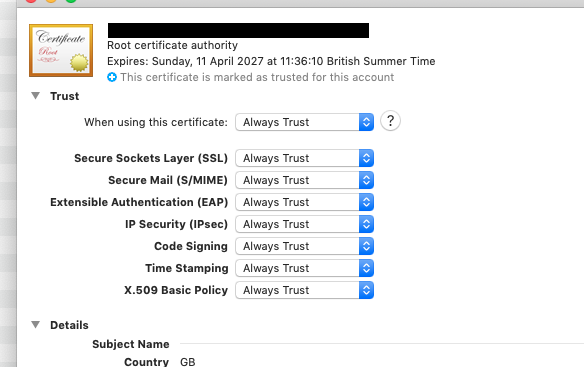
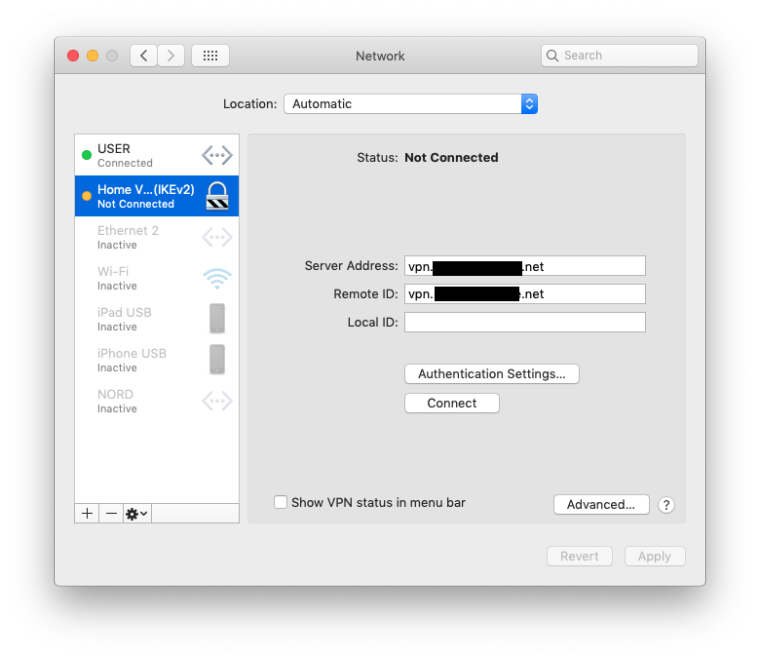
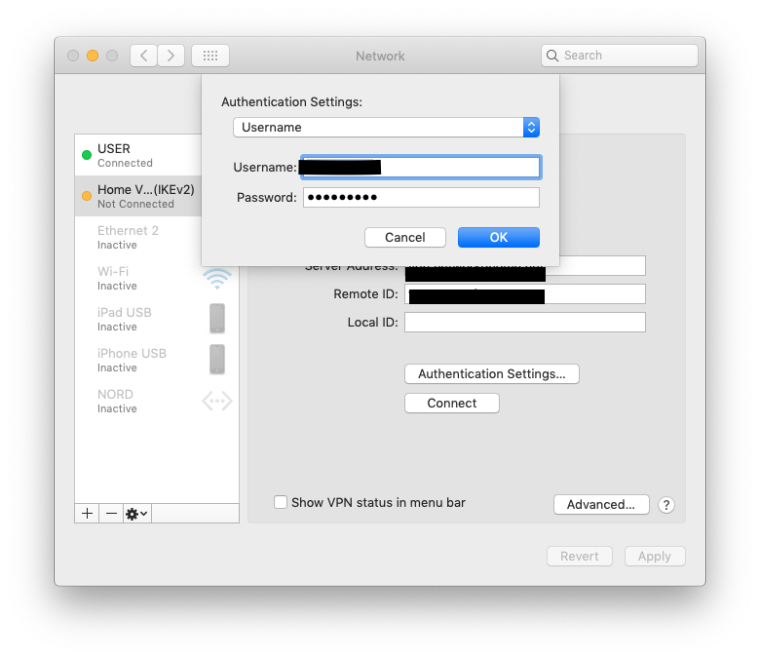
I use a mixture of Windows7, Mac OS & IOS, the following settings seem to work for all:-
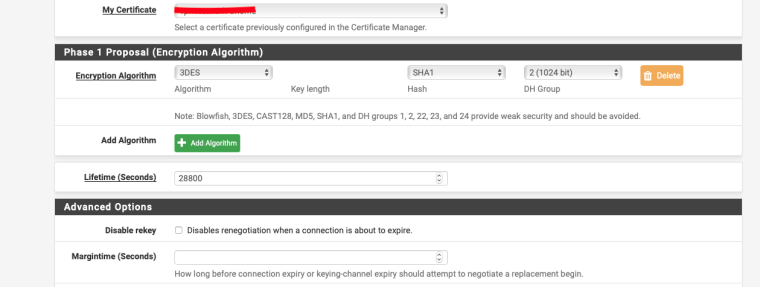
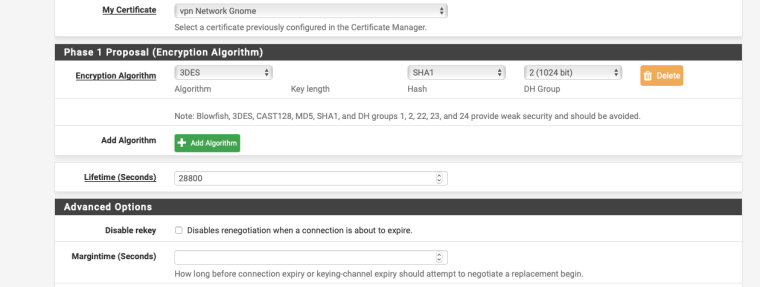
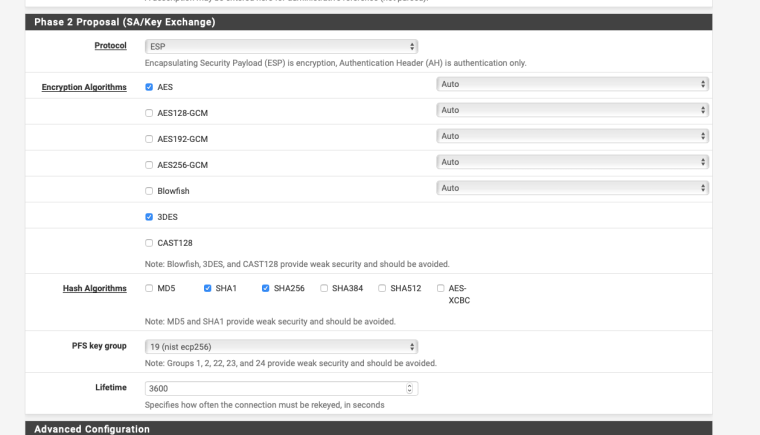
-
@nogbadthebad Thanks for your feedback. Yes, the root CA is trusted and the guide you followed is actually one of the ones I linked to. Working on this further today it seems like it is trying to connect. See my additional reply to this thread below.
-
Update -- I seem to be trying to make a connection. (Please excuse my lack of knowledge on both VPNs and pfSense!) Here is the redacted failure log from pfSense:
Feb 19 15:58:36 charon 05[NET] <38> received packet: from [WANADDRESSOF macOS][500] to 192.168.1.1[500] (272 bytes)
Feb 19 15:58:36 charon 05[ENC] <38> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ]
Feb 19 15:58:36 charon 05[CFG] <38> looking for an IKEv2 config for 192.168.1.1...[WANADDRESSOF macOS]
Feb 19 15:58:36 charon 05[CFG] <38> candidate: %any...%any, prio 24
Feb 19 15:58:36 charon 05[CFG] <38> found matching ike config: %any...%any with prio 24
Feb 19 15:58:36 charon 05[IKE] <38> [WANADDRESSOF macOS] is initiating an IKE_SA
Feb 19 15:58:36 charon 05[IKE] <38> IKE_SA (unnamed)[38] state change: CREATED => CONNECTING
Feb 19 15:58:36 charon 05[CFG] <38> selecting proposal:
Feb 19 15:58:36 charon 05[CFG] <38> no acceptable ENCRYPTION_ALGORITHM found
Feb 19 15:58:36 charon 05[CFG] <38> selecting proposal:
Feb 19 15:58:36 charon 05[CFG] <38> proposal matches
Feb 19 15:58:36 charon 05[CFG] <38> received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384
Feb 19 15:58:36 charon 05[CFG] <38> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048
Feb 19 15:58:36 charon 05[CFG] <38> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384
Feb 19 15:58:36 charon 05[IKE] <38> local host is behind NAT, sending keep alives
Feb 19 15:58:36 charon 05[IKE] <38> remote host is behind NAT
Feb 19 15:58:36 charon 05[IKE] <38> sending cert request for "CN=[NAME], C=US, ST=[STATE], L=[CITY], O=[ORG]“
Feb 19 15:58:36 charon 05[ENC] <38> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ]
Feb 19 15:58:36 charon 05[NET] <38> sending packet: from 192.168.1.1[500] to [WANADDRESSOF macOS][500] (305 bytes)
Feb 19 15:58:37 charon 05[NET] <38> received packet: from [WANADDRESSOF macOS][52092] to 192.168.1.1[4500] (368 bytes)
Feb 19 15:58:37 charon 05[ENC] <38> unknown attribute type (25)
Feb 19 15:58:37 charon 05[ENC] <38> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CERTREQ CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6 (25)) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ]
Feb 19 15:58:37 charon 05[IKE] <38> received cert request for "CN=[NAME], C=US, ST=[STATE], L=[CITY], O=[ORG]“
Feb 19 15:58:37 charon 05[CFG] <38> looking for peer configs matching 192.168.1.1[vpn.domain.com]...[WANADDRESSOF macOS][vpnclient]
Feb 19 15:58:37 charon 05[CFG] <38> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 19 15:58:37 charon 05[CFG] <bypasslan|38> selected peer config 'bypasslan'
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> peer requested EAP, config unacceptable
Feb 19 15:58:37 charon 05[CFG] <bypasslan|38> no alternative config found
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP4_ADDRESS attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP4_DHCP attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP4_DNS attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP4_NETMASK attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP6_ADDRESS attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP6_DHCP attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing INTERNAL_IP6_DNS attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> processing (25) attribute
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> peer supports MOBIKE
Feb 19 15:58:37 charon 05[ENC] <bypasslan|38> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ]
Feb 19 15:58:37 charon 05[NET] <bypasslan|38> sending packet: from 192.168.1.1[4500] to [WANADDRESSOF macOS][52092] (65 bytes)
Feb 19 15:58:37 charon 05[IKE] <bypasslan|38> IKE_SA bypasslan[38] state change: CONNECTING => DESTROYING -
Try changing the P1 & P2 settings as per my screenshots.
“Feb 19 15:58:36 charon 05[CFG] <38> no acceptable ENCRYPTION_ALGORITHM found“
-
@nogbadthebad Tried your settings, even though they are not recommended anymore for security, and did not manage to get any further.
-
@jraymonds said in IKEv2 IPsec VPN with pfSense and Apple devices:
@nogbadthebad even though they are not recommended anymore for security,
Yup that’s due to having w7, ios and mac os, otherwise i’d have made them a bit stronger.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-troubleshooting.html
-
I think Apple might have broken IKEv2 on macOS ... again.
A couple adjustments to this should be made:
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.html
Set Peer Identifier to User Distinguished name, enter an e-mail address style identifier (e.g. user@example.com) – This isn’t used, but is currently required by the GUI
Try setting Peer Identifier to Any.
Also, in the IPsec Mobile config, set a DNS server to give to the clients. I set it to an address on pfSense that DNS Resolver is listening on.
Also, set the Local ID on the macOS configuration to the CN in the user certificate.
That should get you to connect.
After that it looks like there is disagreement between the server and the client as to whether NAT-T or ESP is to be used. As far as I can tell, pfSense is doing the right thing here. This seems to correct itself after the first re-key (I think. I haven't dug into the logs to verify this). IDK. Apple keeps messing with the IKEv2 client.
I am testing EAP-TLS with Mojave 10.14.3 to pfSense 2.4.4-p2. I have not tried iOS yet.
-
@derelict thanks for trying to help on this one. The https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.html falls short of hitting all of the settings. (For example it doesn't say anything about MOBIKE, DPD, etc) if you have a working config with EAP-TLS with Mojave 10.14.3 to pfSense 2.4.4-p2 it would be great to see a screen shot. (I have been through so many versions and comments on this -- some say lower case for CA common name, some different formats for the client CN, etc) iOS would make it complete but at the moment that is a zero priority -- my focus is on macOS.
-
Generally the walk-through documentation only covers changes from the defaults and cover just enough to get it working. Other documentation, like the book, should be consulted for other options. Far too many options to make a walkthrough for every conceivable configuration.
The only discrepancies I can find are the Peer identifier: any, the DNS Server, and the Local ID needs to be set to the CN in the certificate. I do not believe this used to be required. IMHO the Mac client should just use the CN out of the cert if that's what it needs to be unless it is explicitly set.
What I am seeing, however, is the initial connection connects, but results in the Mac side sending traffic using NAT-T (UDP/4500) while the pfSense side is sending and expecting protocol ESP. There is no NAT in my test environment so it would stand to reason that NAT-T should not be used.
The Mac client always re-keys at exactly 8 minutes. (This used to work for 8 minutes then break but they fixed that.) When this happens, the Mac side starts sending its payloads encapsulated in ESP and everything starts working.
Here is one such exchange. The Mac is 192.168.223.203, the pfSense VM WAN is 172.25.228.5. The Mac is pinging 8.8.8.8:
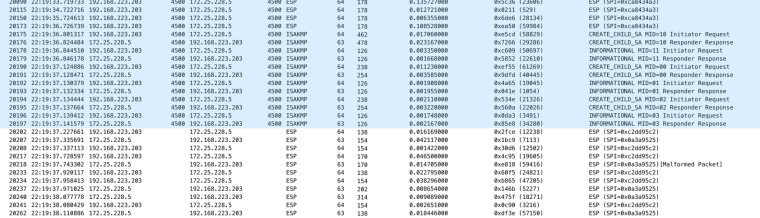
Note how the port column goes blank because NAT-T is no longer in use. After it's all working the internet works. Speed tests at about 150Mbit/sec, etc.
This is being tested NOT using the profile exporter since my test device is Community Edition. It might be that using a profile will make it work. (In the aforementioned work for 8 minutes then break, it would only break on manual configured tunnels. If you used a profile it would work.) I still have not tried iOS. Maybe later.
-
@derelict Okay, it was my dumb setup in the NAT that was causing most of the problems. I have a range of static addresses and I use 1:1 mapping for them. Well, I included the pfSense box in the 1:1 maps and that was resolving the VPN request to the LAN side instead of the WAN side. With that fixed this configuration pretty much works: (pfSense IKEv2 for iOS/macOS) I am still tracking an odd problem of not being able to access the pfSense box from the LAN when connected with the VPN but at least I can sleep better now with the rest figured out.
-
I know it's an old topic, but specifically because it's old I am asking that you actually update the official Docs with these conclusions and replace the "Set Peer Identifier to User Distinguished name, enter an e-mail address style identifier (e.g. user@example.com) – This isn’t used, but is currently required by the GUI" with "Set to Any".
I would do this myself, but you don't seem to be hosting the Docs on GitHub anymore.
I spent some 2 hours today at my wits end trying to figure this out before I set the Local ID on my mac to "user@example.com" and got it working.