AWS Pfsense OpenVPN no access to private subnet
-
Netgate forum users,
I have set up a pfsense instance that also acts as the OpenVPN server.
Then I installed pfsense on AWS with the official pfsense AMI and everything is working as expected so far.I have 1 public subnet and 1 private subnet containing a linux instance that I want to reach via the VPN.
When connecting to the VPN I can't ping the linux instance in the private subnet.
The pfsense firewall (2.4.4) has the following interfaces:
WAN 10.3.0.245
LAN 10.3.1.5The OpenVPN tunnel network is 10.3.2.0/24 going to 10.3.1.0/24 channeling all trafic trough the VPN.
The linux instance has the following private IP: 10.3.1.58
The firewall itself can ping the instance and when I connect to the VPN (windows host) I can ping the firewall on 10.3.1.5 .However, I can't ping 10.3.1.58 (request timed out). I cant SSH either into the instance.
OpenVPN client config:
dev tun persist-tun persist-key cipher AES-128-CBC ncp-ciphers AES-128-GCM auth SHA256 tls-client client resolv-retry infinite remote 18.197.36.21 1194 udp verify-x509-name "VPN Server Cert" name auth-user-pass pkcs12 pfSenseMentech-UDP4-1194-Hicham.p12 tls-auth pfSenseMentech-UDP4-1194-Hicham-tls.key 1 remote-cert-tls server compressThe security group in amazon allows all trafic for now. Disabled the firewall on the linux system. Disabled source / destination checking on the instance and the secondary network interface.
I have allowed traffic from the vpn to the lan (for now I allowed all traffic to see where the problem lies).
What I tried:
- disable firewall on windows / linux instance
- Running OpenVPN GUI as admin
- Force all client-generated IPv4 traffic through the tunnel. on / off
- Making new vpn server and user
- enable opvns interface, bridge LAN with opvn interface
- pushing "redirect-gateway def1"
- pushing "10.3.1.0 255.255.255.0"
- allow all in firewall rules
Route print on windows client:
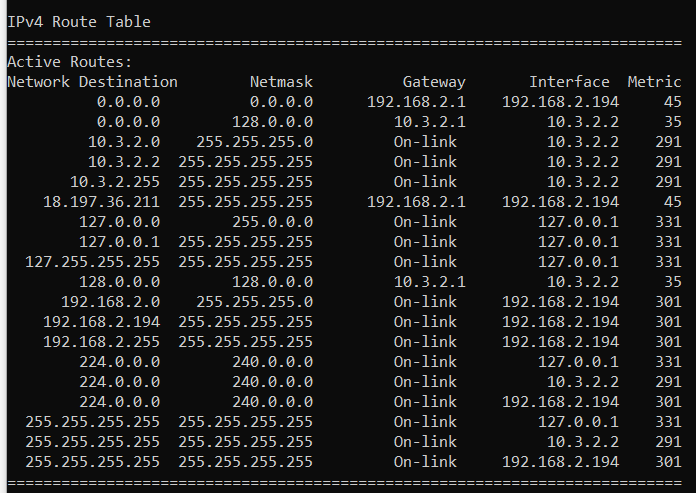
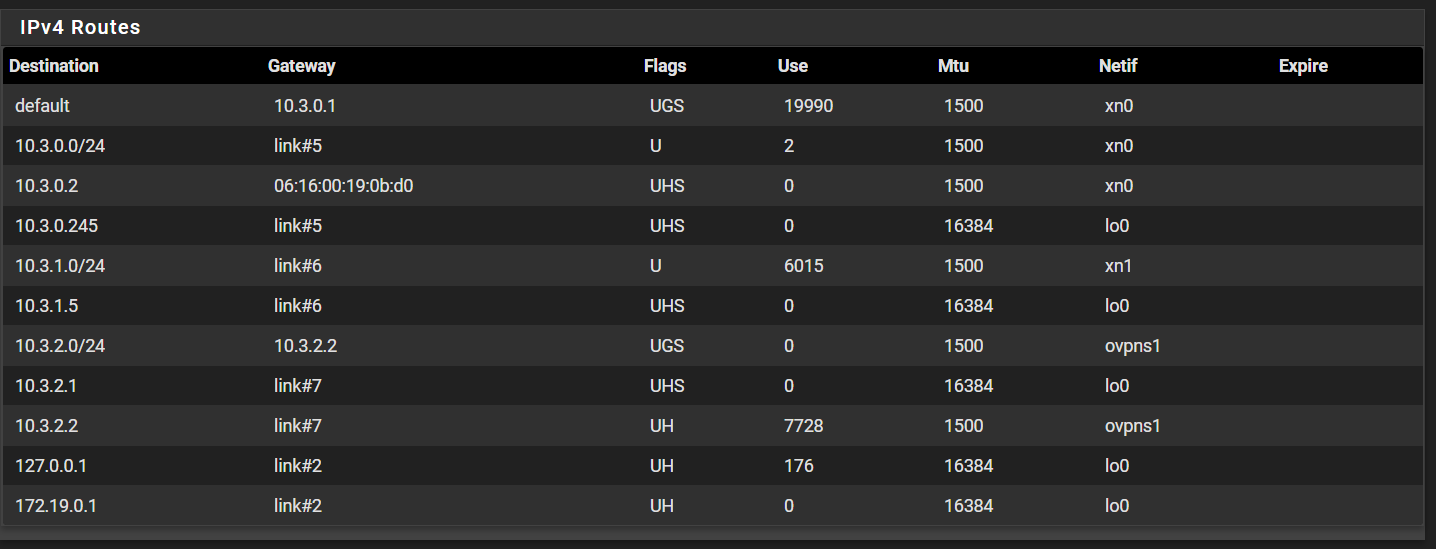
Routes on pfsense:
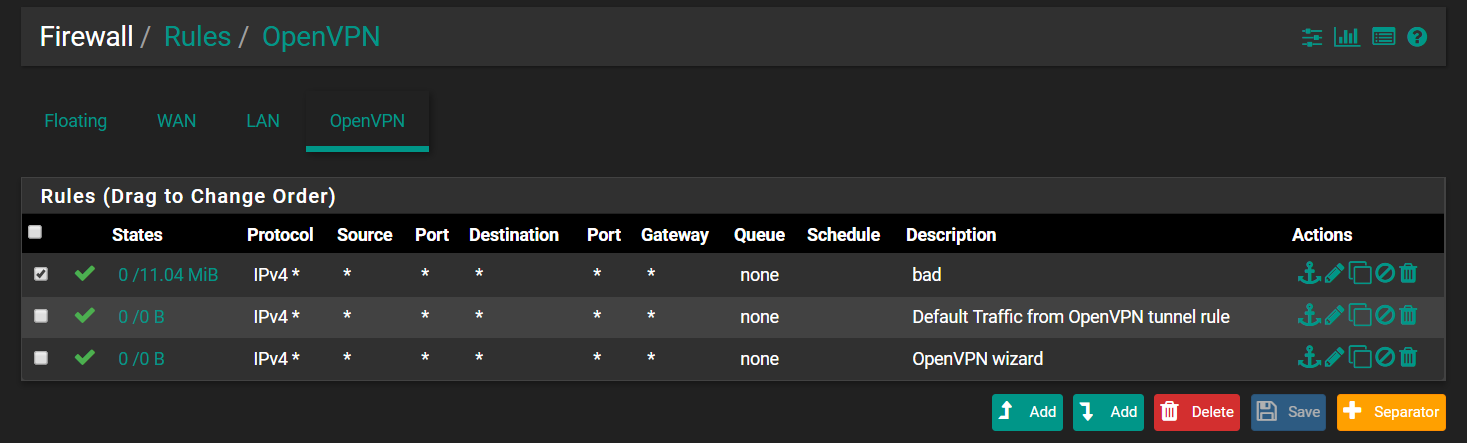
Openvpn firewall rules:
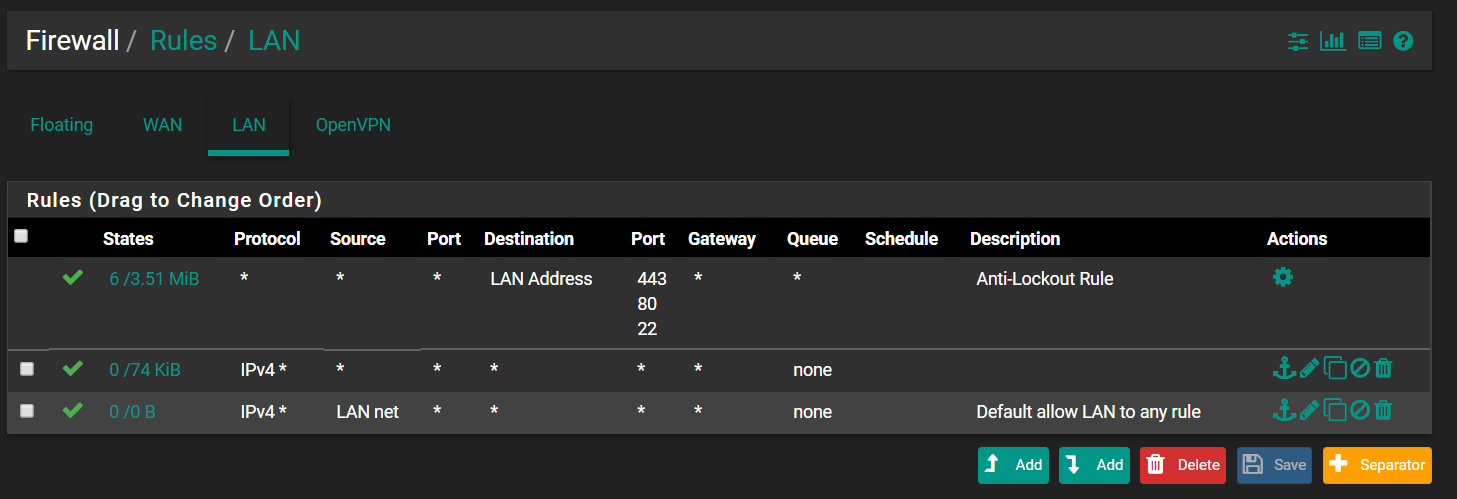
lan firewall rules:
-
please post the firewall rules on the openvpn interface.
-
Will update the topic:

-
sorry, should have also requested LAN rules as well. please post those too.
-
@isolatedvirus no worries, thank you for your time. Updated the topic with the requested information!
-
can you confirm pfsense can ping the instance (.58)
Also confirm the following:
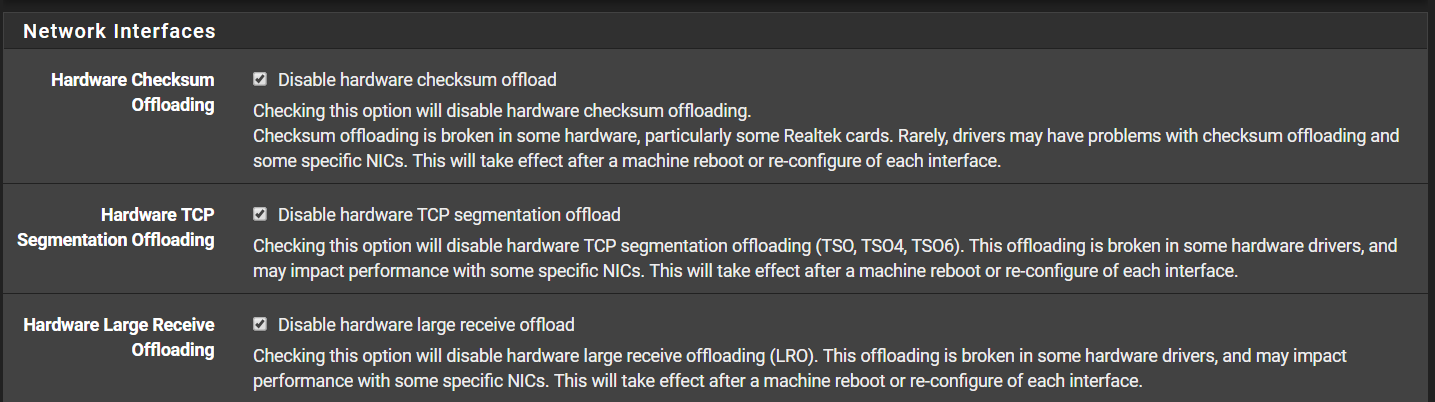
System->Advanced->Networking
-All offloading is disabled (Checksum/TCP Seg/Large Receive -
Yes pfsense can ping all instances in the private subnet.
Confirmed:
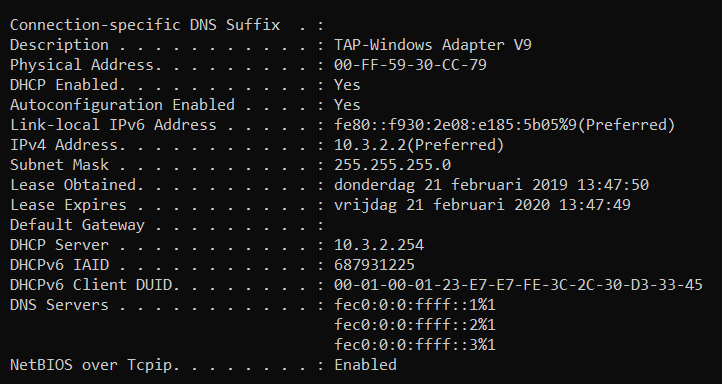
I don't get a default gateway when connecting to the vpn, could that have something to do with it?
-
ok i think it might be a route or firewall entry on the linux host itself.
You can post your screenshots of your OpenVPN server config, but i doubt theres an issue there primarily because: Windows can ping the firewall tunnel IP and the firewall interface on the subnet in question. This leads me to believe youre forwarding the correct routes for the vpn.
Post the route table and firewall config for the linux host.
-
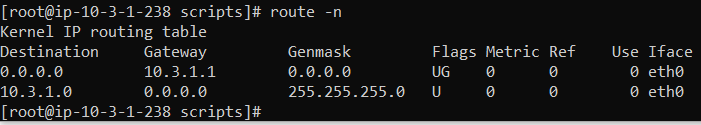
@isolatedvirus ok, thank you for your reply. I currently have 2 linux hosts in the private subnet (which has access to the internet for now otherwise I could not SSH into the hosts):
Nagios XI on centos:
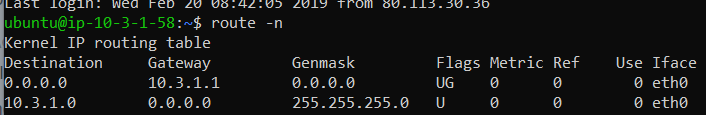
Ubuntu server:
firewall is off:
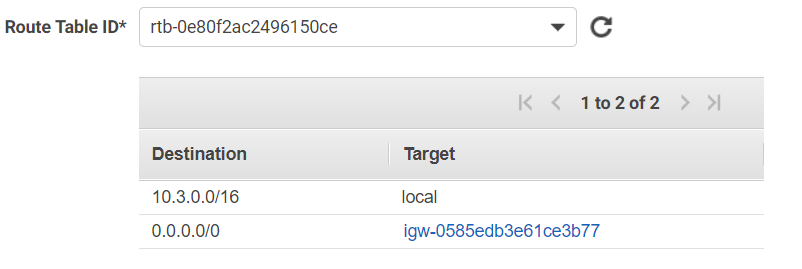
Amazon private subnet (should be without internet access):
-
your hosts have their gateway set as 10.3.1.1, it should be 10.3.1.5 (PFSense Lan) unless you have another gateway in the environment.
Otherwise, set a route for your VPN subnet to point to 10.3.1.5 on the linux hosts
-
@isolatedvirus said in AWS Pfsense OpenVPN no access to private subnet:
10.3.1.5
Yes this worked!
I can now ping my private subnet instances from the vpn client.
Do you happen to know why the default gateway gets set to 10.3.1.1?
Everytime I make a new instance it sounds like I need to change the default gateway manually.Thank you for your time and help.
-
I'm not sure why. If youre handing out IP's behind pfsense via DHCP i'd check the dhcp config to verify youre not handing out the wrong gateway config.
Its also possible that this is just a AWS thing, since im not familiar with AWS i cant really say.
-
What have you done in the VPC routing table so it knows to send traffic for the 10.3.2.0/24 subnet back to the pfSense interface?
-
Is this regarding the default gateway of the instances?
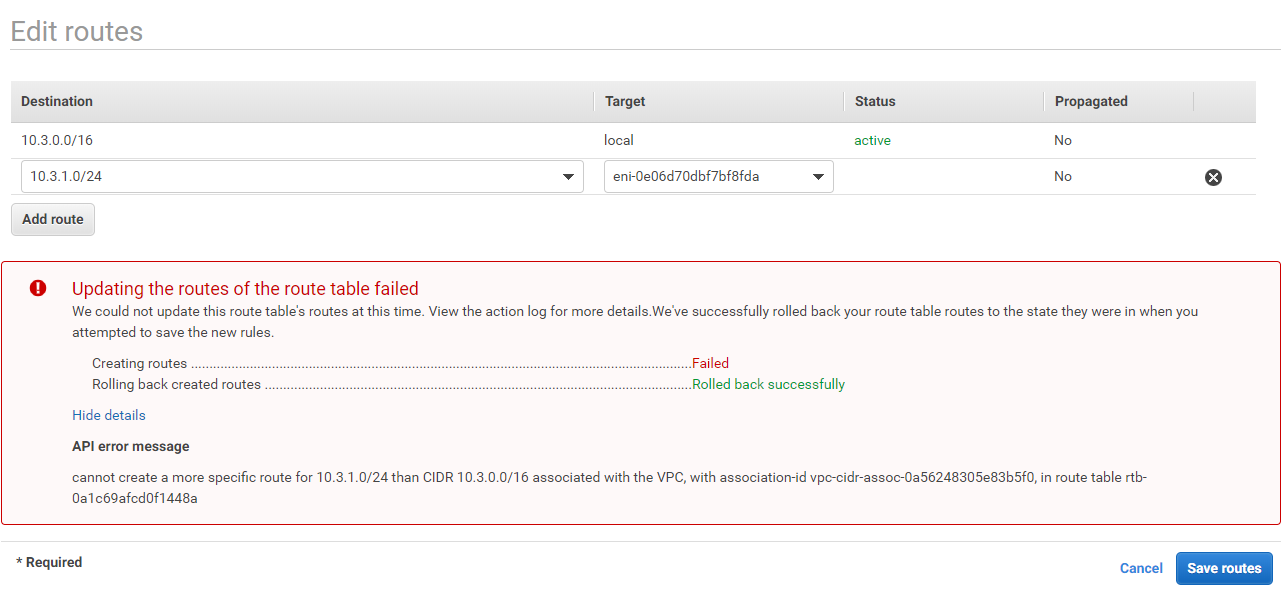
I thought I should edit the route table of the private subnet to point to 10.3.1.5 which is the LAN side of the pfsense firewall but it won't let me do just that:private subnet
-
You can't use subnets contained inside your VPC subnet anywhere but the VPC itself.
Use something outside of that for the other side of the VPN. Sorry. That's just the way AWS works, as you can see from that error message.
-
@Heikum in my case hardware checksum offloading chacked solved the problem. Thanks!
-
@Leonardo-Fernandes That is only when using ena adapters and is fixed by a later version of the ena driver in pfSense 2.5.0.
-
@leonardo-fernandes You are my hero. Thank you very much. My OpenVPN with AWS works perfectly now