Why use pfsense as an NTP server?
-
I'm wondering, is there any benefit to using the pfsense box itself as the NTP server for your internal networks? I mean, is it keeping better time than external time servers that most computers/workstations are already programmed to check automatically?
I know the NTP traffic is really small, so if I setup the proper rules, is it worth keeping that traffic "in network", or is it so trivial that the pass any-to-any rules on the various interfaces we've got setup is enough.
I'm not asking how to set all this up, that's pretty easy. I was just wondering why somebody would want to do it. I have searched for any helpful posts or articles on this, but it's mostly the instructions for how to make it all work.
I guess if I'm asking "why do it", I don't really need to do it...
Anybody got any insight? Thanks!
Jeff
-
NTP sources can have jitter, lag and other artifacts from being on the public Internet. These problems don't exist to anywhere near the same degree on LAN. What that means is that your LAN clients will all have the same time if they fetch it from the router. If each LAN client has to fetch his own time from the Internet, they can be slightly off as compared to each other as measured in milliseconds. Usually this isn't that important for most people. Kerberos auth like MS AD requires timestamps that are within 5 minutes of domain time, but even with a jittery NTP server, you wouldn't be 5 minutes out of sync.
-
Also helps keep the traffic down on the external servers.
-
And you can use a GPS module for even more accuracy: https://docs.netgate.com/pfsense/en/latest/book/services/ntpd-gps.html
-
All of the above and if I think about my 50+ hosts at home alone all querying ntp.org instead of only my router the motivation should be clear.
The new paradigm seems to be data-abstention (at least in Europe/Germany). -
Added to all that : my pfSense doesn't do much anyway (35 hosts), and upstream bandwith is always not enough ....
-
@akuma1x said in Why use pfsense as an NTP server?:
I know the NTP traffic is really small,
Already touched on but don't forget very small time X number of clients can equal not so small ;)
Also touched on with your time source being common and local your machines time will all be better in sync then all your different clients talking to different servers with different jitter and response times depending.
The question should be more to you have a box that can be ntp server that is local - why would you not just have your local clients point to it?
-
@johnpoz said in Why use pfsense as an NTP server?:
The question should be more do you have a box that can be ntp server that is local - why would you not just have your local clients point to it?
I agree with that, and it makes sense. So, would it better network etiquette (netiquette? :)) to program the settings into each client/host to use the pfsense box as the NTP server, or setup pfsense to do the redirect work itself?
Jeff
-
You do not need to redirect anything... Just hand out ntp via dhcp and you would hope most clients would use that.. If clients do not, then you might have to set them on the client to point to your local ntp..
Where you might want to redirect or setup some host overrides is iot devices that might be harded coded query a specific ntp name or IP.
Found some bad programmed iot devices that for example use wrong freaking country ntp pool.. Some lights I have hit uk.pool.ntp.org for example.. Morons!! ;)
For starters if they want their device to use ntp that is great, they should prob use the custom listing you can setup with ntp.org like pfsense did.. Or atleast let the user change it - because not even in the UK.. Im in the US.. So some lazy coding there for sure ;) Not like I bought UK version of the lights, bought them off amazon and they are US lightbulbs.. So why they freaking point to uk ntp pool? ;)
How deep you want to get into it is up to you - I love ntp so much I run a local ntp stratum 1 on a pi ;) that serves up to the pool ;)
-
@johnpoz said in Why use pfsense as an NTP server?:
Some lights I have hit uk.pool.ntp.org for example.. Morons!! ;)
They wanted to use NTP servers closest to the Greenwich Meridian for the sake of precision...



-
heheeheh - yeah maybe ;)
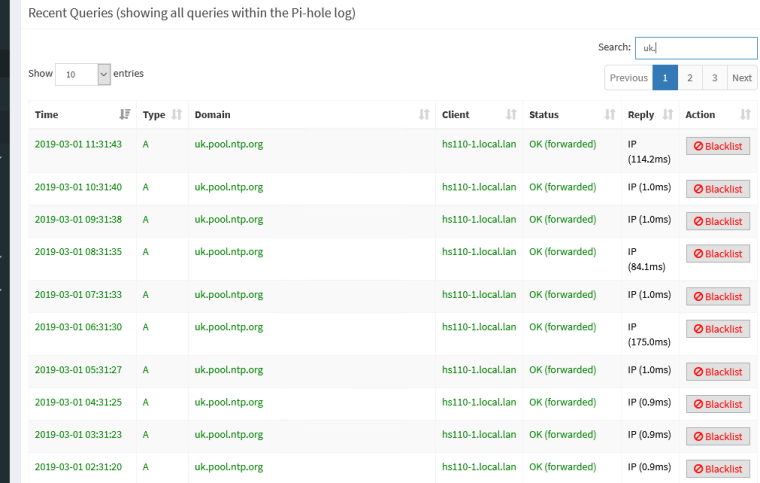
My bad it wasn't the actual "light" is was the HS110 smart switches...
I will have to put that override back in for uk.pool.ntp.org ;)
-
@johnpoz said in Why use pfsense as an NTP server?:
You do not need to redirect anything... Just hand out ntp via dhcp and you would hope most clients would use that.. If clients do not, then you might have to set them on the client to point to your local ntp..
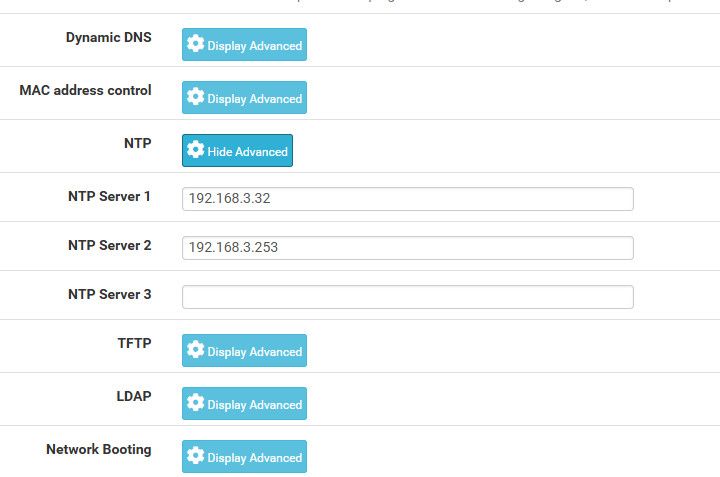
Am I correct in saying you would do this under Services > DHCP Server > Other Options > NTP and then just enter 192.168.0.1 in the field "NTP Server 1"? (if 192.168.0.1 is the LAN address of the pfSense router)
-
@occamsrazor yes in your dhcp server area you can set up to 3 ntp servers to hand out via dhcp. But there is nothing saying that the client will actually use this..
Linux more likely to use these than say windows client - guess to if iot will use it, prob not. Especially when they are hard coded to use some specific pool address like in my above example with uk pool... Stupid devices ;)
Best plan is set your dhcp to use the ntp you want, then watch your dns and network traffic - are they actually using that, if not then look to see what dns they are using and you could override that dns to point to the ntp server you want them to use.
If they are really horribly at it, and have some hard coded IP they point too - then yeah you could do a redirect for ntp on that IP, or just all traffic on udp 123 to what you want them to use locally. Its not like they are doing any sort of authentication that who they are asking for ntp is that specific ntp..
-
@johnpoz said in Why use pfsense as an NTP server?:
If they are really horribly at it, and have some hard coded IP they point too - then yeah you could do a redirect for ntp on that IP, or just all traffic on udp 123 to what you want them to use locally. Its not like they are doing any sort of authentication that who they are asking for ntp is that specific ntp..
That would seem the simplest solution... I could just redirect all NTP requests coming from my LAN to the pfSense NTP server. Do you see any disadvantage to that? I'm mostly Apple and IOS plus some IoT devices and have been reading some reports that Apple devices aren't great at keeping synchronized in latest OS versions so was keen to try. I should add that I've encountered no problems, just keen to play with the capabilities of pfSense....
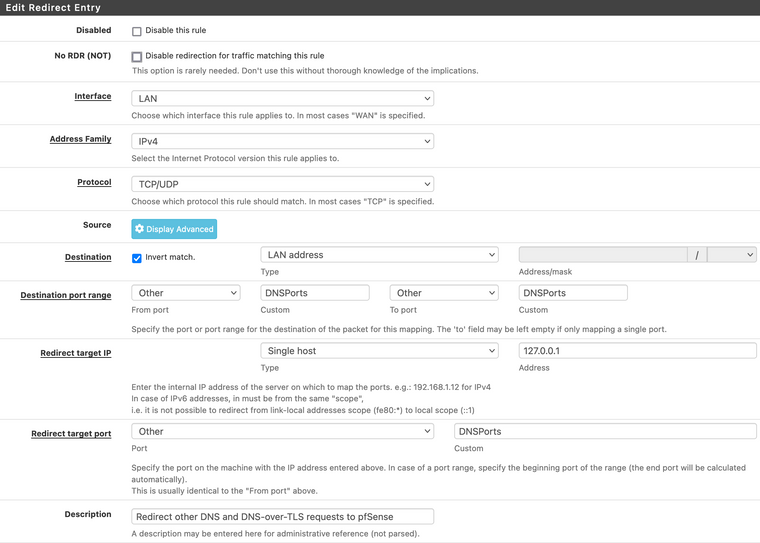
Could you please remind me where and how to create such a redirect rule? I have this existing port forward rule that intercepts DNS requests and redirects them to my pfSense server - would it be exactly the same but with the NTP port 123 instead?
Thanks...
-
@occamsrazor Yeah it would be the same as dns, just use port 123..
I'm just not a fan of redirection in general.. If you can accomplish what you want without redirecting traffic would be the better option imho.
BTW why are you using alias dnsports? This really would only be 53..
reports that Apple devices aren't great at keeping synchronized in latest OS versions
I have not seen such reports - do you have a link that your seeing this being reported? I only have phones - which would use the cell connection to keep accurate time.. I was just using ipad to show time for a video test of latency, and it was spot on..
-
It just seems like it would be advantageous to have all devices on LAN sync from the same time server, and as pfSense is using multiple NTP servers and then making a single decision as to the time, having them sync to pfSense would keep all devices in fairly perfect sync.
I'm using that alias to redirect both DNS port 53 and DNS-over-TLS port 853 to pfSense Unbound
Re: links on Mac devices (note Mac and specifically Big Sur version, not IOS):
https://apple.stackexchange.com/questions/414088/macos-timed-wont-keep-accurate-time
https://forums.macrumors.com/threads/time-synchronization-command-line-in-macos-big-sur.2279396/I'll admit it's a bit beyond me....
-
@occamsrazor said in Why use pfsense as an NTP server?:
DNS-over-TLS port 853 to pfSense Unbound
That isn't going to work.. Atleast not with any sane client, because the client should be validating the cert.. even if you have pfsense listening on 853, the certs not going to be valid for the cn the client should be checking.
I am not saying its not a good idea to sync all your clients to your local source, I am just against redirection. The correct solution is to point the clients at your ntp server - be it via dns, via dhcp handing it out, be it via configuration on the client directly..
If you can not get your client to use local ntp by normal means - then sure redirect them to accomplish your goal. It would just be my last choice is all.
-
@johnpoz said in Why use pfsense as an NTP server?:
That isn't going to work.. At least not with any sane client, because the client should be validating the cert.. even if you have pfsense listening on 853, the certs not going to be valid for the cn the client should be checking.
It was a long time ago I set this up. I seem to remember the objective may have been to prevent guest devices on my network that might have hard-coded DNS-over-TLS servers from being able to bypass Unbound. I think the objective may have been intentionally for such requests to fail.. umm, maybe?
Edit: It came from this discussion (though I'm no longer using forwarding, am using as resolver): https://forum.netgate.com/topic/135832/quad9-dns-over-tls-setup-with-unbound-forwarding-in-2-4-4-rc
I am not saying its not a good idea to sync all your clients to your local source, I am just against redirection. The correct solution is to point the clients at your ntp server - be it via dns, via dhcp handing it out, be it via configuration on the client directly..
That does seem better, but with a number of different devices such as IOT etc it seems like it would be a lot of work manually configuring and some devices may be hard-coded or or without the option to set manually as you point out. Then, for mobile devices such as laptops and iPhones, I wouldn't want to hard-code to pfSense as they'd then have the wrong NTP server when outside the home, no? I'm in favor of solutions that can be implemented, changed, disabled easily at the router level to avoid this.
I'm sensing I may be overcomplicating solutions to a problem that doesn't exist, but it's fun to experiment :-)
-
@occamsrazor said in Why use pfsense as an NTP server?:
I could just redirect all NTP requests coming from my LAN to the pfSense NTP server.
When I tried that, the traffic was routed but the clients were not able to update their time, indicating some form of validation is used.
-
@patch said in Why use pfsense as an NTP server?:
When I tried that, the traffic was routed but the clients were not able to update their time, indicating some form of validation is used.
I've added the redirect rule but struggling how exactly to test if (a) requests to external NTP servers are indeed getting redirected to pfSense and (b) if they are being successful.
Not sure if this is correct usage on OSX but I'm not sure if the pfSense NTP server is working properly:
Trying to sync with pfSense:
~ % sntp 192.168.0.1 sntp: Exchange failed: Server not synchronized sntp: Exchange failed: Timeout sntp: Exchange failed: Timeout sntp: Exchange failed: Timeout -0.022114 +/- 0.017639 192.168.0.1 192.168.0.1With redirect rule ENABLED:
~ % sntp time.nist.gov sntp: Exchange failed: Server not synchronized sntp: Exchange failed: Timeout sntp: Exchange failed: Timeout sntp: Exchange failed: Timeout -0.023434 +/- 0.016968 time.nist.gov 132.163.97.4With redirect rule DISABLED:
~ % sntp time.nist.gov +0.006460 +/- 0.000610 time.nist.gov 132.163.97.4