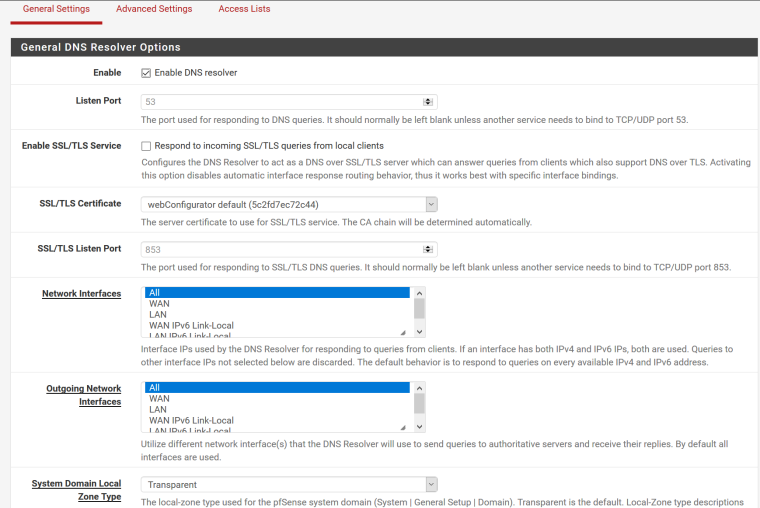
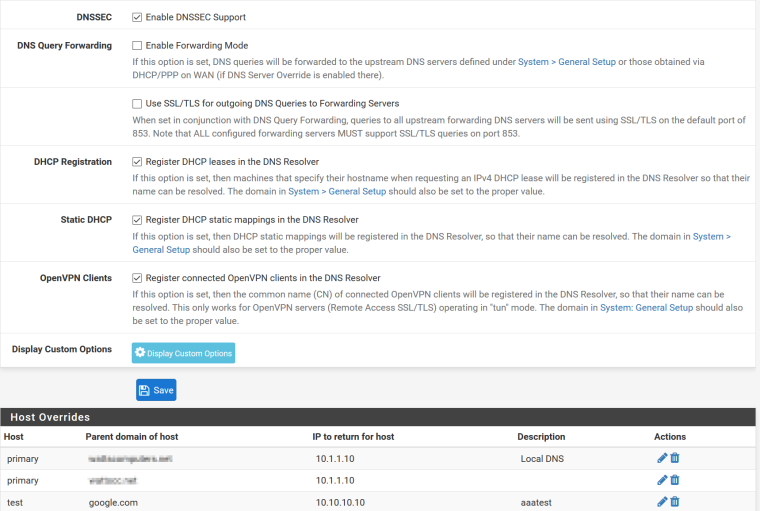
DNS Resolver/Forwarder host overrides not working
-
Hello folks
So I have been struggling for weeks now to figure out the pfsense DNS resolver/forwarder host overrides. It looks simple enough. Yes I've entered my overrides in the correct area. Yes I have made sure the host I am testing from is using my pfsense LAN IP as its ONLY DNS source. It looks like it should be a simple point and click operation. No matter which service I use, forwarder or resolver, both continue to ignore my host overrides and resolve FQDN's to their public IP's. All I am trying to do is have it so my mobile devices will resolve to the proper public IP when I'm connecting from outside my network and then resolve to the proper private IP when I'm connected internally on my LAN. I am running the latest pfsense version (2.4.4-RELEASE-p2 (arm) on a netgate 3100.
Maybe it's a simple setting that needs to be changed, or, this version of pfsense is confirmed broken. I'm hoping you folks can help me figure out which.
-
@reddelpapa said in DNS Resolver/Forwarder host overrides not working:
All I am trying to do is have it so my mobile devices will resolve to the proper public IP
And what mobile device is this? Phones love to use hard coded dns, browsers in phones also love to use proxies, etc.
Its simple enough to validate your host override is working... Do a actual query to pfsense dns from say windows or linux machine... Be it nslookup, dig, host, etc.
There is nothing really to do other than create your host override..
Create the override, apply it - do a validation test
If your phone is not then resolving the same IP as pfsense hands out - then you need to validate your phone is actually using pfsense for dns. Maybe you want/need to use dns redirection to force your mobile device to query pfsense no matter what dns it points too... Keep in mind if using a browser proxy that proxies don't query local dns, the proxy they use are what is doing the dns queries.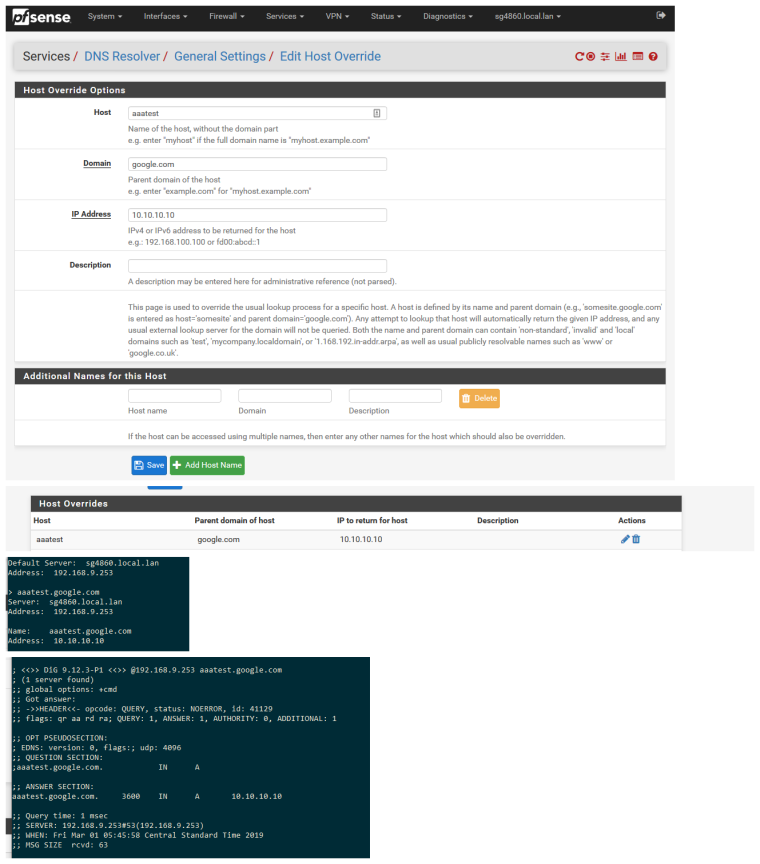
-
Thank for your response. My settings look identical to what you show.
My phone is one. It can't check my email when it's on the lan because my server host names are set to what works from outside my network. But also the problem exists on my laptop. From there it's easy to test. I do an nslookup, specify my pfsense router as the server, and then do a lookup on my hostname.domain.net and it always returns my public IP instead of 10.1.1.10 which is what I set for the host override for my mail server.
Any other ideas?
-
@johnpoz Ok, new problem. When I test from the DNS lookup app within pfsense, here is what I get. It returns the correct address along with and below the LAN adapter address of my pfsense box. Why?
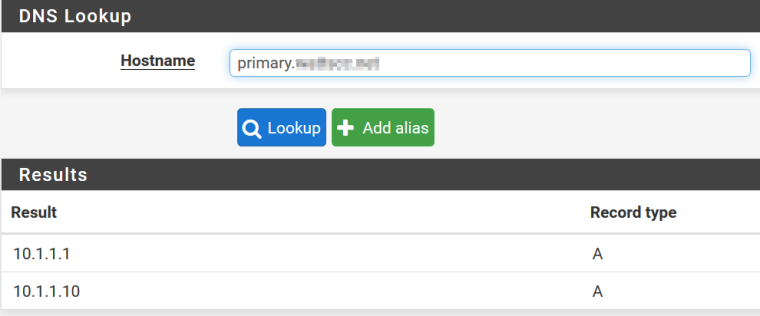
When I setup a host override for test.google.com, it works correctly from the DNS lookup app in pfsense.
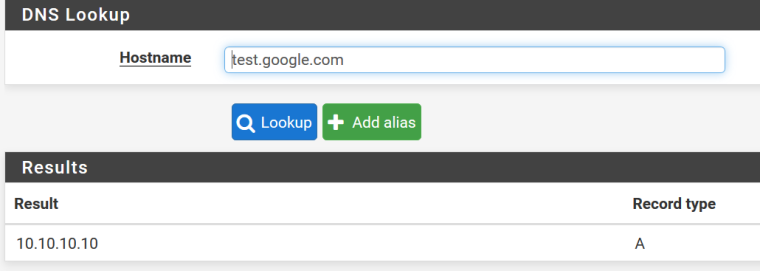
-
@johnpoz
From a different computer, using an nslookup app, it now cannot resolve test.google.com. Which should resolve to 10.10.10.10. The server returns a domain not found error.
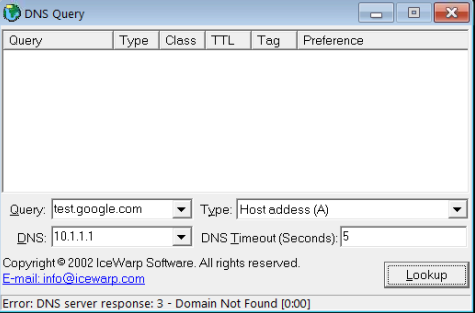
-
Tested twice :
Microsoft Windows [version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. Tous droits réservés. C:\Users\Réception-Gauche>nslookup Serveur par dÚfaut : pfsense.brit-hotel-fumel.net Address: 2001:470:1f13:5c0:2::1 > test.google.com Serveur : pfsense.brit-hotel-fumel.net Address: 2001:470:1f13:5c0:2::1 *** pfsense.brit-hotel-fumel.net ne parvient pas à trouver test.google.com : Non-existent domain > test.google.com Serveur : pfsense.brit-hotel-fumel.net Address: 2001:470:1f13:5c0:2::1 Nom : test.google.com Address: 10.10.10.10 >The first time : domaine not found - which is a correct answer.
Before launching the seconde, same test I put in place a host override for test.google.com
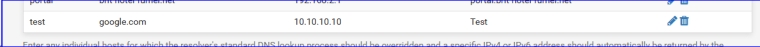
This time, the answer was 10.10.10.10
That is the good news.
The bad news : I'm using the Resolver in Resolver mode. But I'm pretty sure it should behave the same way when using Forwarder mode.Also :
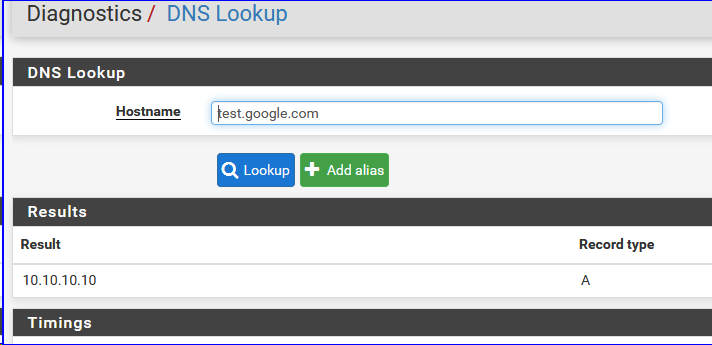
which is ok. -
is 10.1.1.1 your pfsense IP on this network. Your firewall rules allow it to be queried. Unbound is is using this interface to answer queries?
This is really drop dead click works.. Looks to me like your clients can not even query pfsense for anything. Post up your unbound config and your firewall rules.
It would respond with both if you use the same name as pfsense actual name you setup.
-
@johnpoz
Yes, yes, and yes. It will resolve external IP's for me just fine. What it won't do is pass on an overidden host to any PC on my LAN.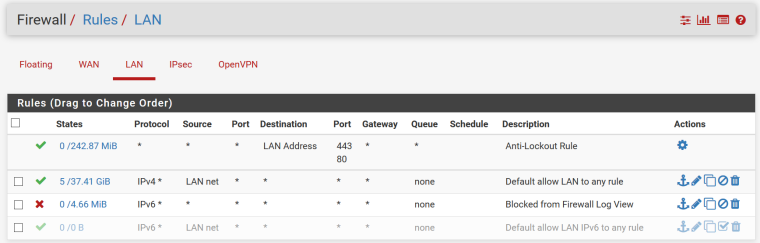
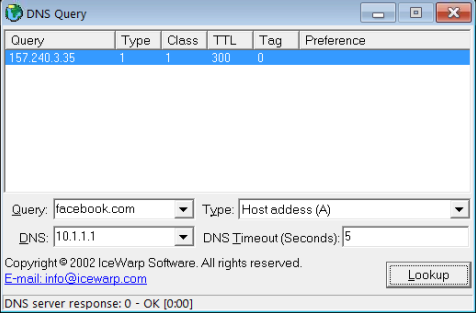
Where do I find this config file? -
-
And are you actually hitting apply to restart unbound when you put in your override?
Do you have anything odd in your custom options?
Look in your unbound conf file.. It would show you your overrides you have set. Restart Unbound.
Look in your host conf file
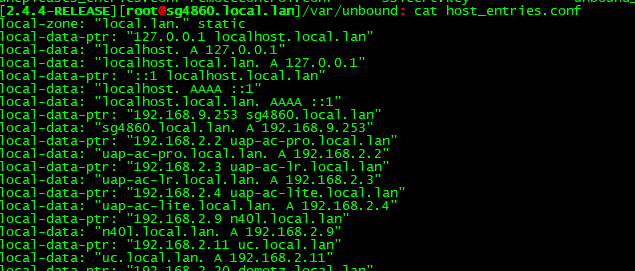
Do you actually see your host override in there - did unbound actually restart after you put in your override..
Are you running something like pfblocker?
Can you not just use a real tool like nslookup or dig so you can actually see if there what you get back like maybe NX or something or if your getting a servfail, etc. Increase the logging of unbound - do you actually see the query in the log?
Looks like tool reports nx, domain not found... My guess would be your not actually restarting unbound after you put in your override? Or maybe you have some sort of dns redirect going on? You need to validate your actually asking unbound, and unbound has the record there to serve up.
-
@johnpoz
"And are you actually hitting apply to restart unbound when you put in your override?" Yes.
"Do you have anything odd in your custom options?" Not that I'm aware of.
"Look in your unbound conf file.. It would show you your overrides you have set. Restart Unbound."
Unbound has been restarted. I don't see anything in unbound.conf pertaining to my domains.Here is my unbound.conf:
##########################Unbound Configuration
##########################
Server configuration
server:
chroot: /var/unbound
username: "unbound"
directory: "/var/unbound"
pidfile: "/var/run/unbound.pid"
use-syslog: yes
port: 53
verbosity: 1
hide-identity: yes
hide-version: yes
harden-glue: yes
do-ip4: yes
do-ip6: yes
do-udp: yes
do-tcp: yes
do-daemonize: yes
module-config: "validator iterator"
unwanted-reply-threshold: 0
num-queries-per-thread: 512
jostle-timeout: 200
infra-host-ttl: 900
infra-cache-numhosts: 10000
outgoing-num-tcp: 10
incoming-num-tcp: 10
edns-buffer-size: 4096
cache-max-ttl: 86400
cache-min-ttl: 0
harden-dnssec-stripped: yes
msg-cache-size: 4m
rrset-cache-size: 8mnum-threads: 2
msg-cache-slabs: 2
rrset-cache-slabs: 2
infra-cache-slabs: 2
key-cache-slabs: 2
outgoing-range: 4096
#so-rcvbuf: 4m
auto-trust-anchor-file: /var/unbound/root.key
prefetch: no
prefetch-key: no
use-caps-for-id: no
serve-expired: noStatistics
Unbound Statistics
statistics-interval: 0
extended-statistics: yes
statistics-cumulative: yesSSL Configuration
Interface IP(s) to bind to
interface-automatic: yes
interface: 0.0.0.0
interface: ::0Outgoing interfaces to be used
DNS Rebinding
For DNS Rebinding prevention
private-address: 10.0.0.0/8
private-address: ::ffff:a00:0/104
private-address: 172.16.0.0/12
private-address: ::ffff:ac10:0/108
private-address: 169.254.0.0/16
private-address: ::ffff:a9fe:0/112
private-address: 192.168.0.0/16
private-address: ::ffff:c0a8:0/112
private-address: fd00::/8
private-address: fe80::/10Set private domains in case authoritative name server returns a Private IP address
private-domain: "google.com"
domain-insecure: "google.com"Access lists
include: /var/unbound/access_lists.conf
Static host entries
include: /var/unbound/host_entries.conf
dhcp lease entries
include: /var/unbound/dhcpleases_entries.conf
OpenVPN client entries
include: /var/unbound/openvpn.*.conf
Domain overrides
include: /var/unbound/domainoverrides.conf
Remote Control Config
include: /var/unbound/remotecontrol.conf
"Look in your host conf file"
Here is my hosts file:
127.0.0.1 localhost localhost.mydomain.net
::1 localhost localhost.mydomain.net
10.1.1.1 primary.mydomain.net primary
10.1.1.10 S1.mydomain.net S1
10.1.1.10 primary.myseconddomain.net primary
10.1.1.10 primary.mydomain.net primary
10.10.10.10 test.google.com testdhcpleases automatically entered
dhcpleases automatically entered
"Are you running something like pfblocker?" I am running pfBlockerNG. Is that a problem?
"Can you not just use a real tool like nslookup or dig so you can actually see if there what you get back like maybe NX or something or if your getting a servfail, etc. Increase the logging of unbound - do you actually see the query in the log?
Looks like tool reports nx, domain not found... My guess would be your not actually restarting unbound after you put in your override? Or maybe you have some sort of dns redirect going on? You need to validate your actually asking unbound, and unbound has the record there to serve up."
I use nslookup from a windows machine. Are you speaking of something else? Can you tell me how to do as you suggest? I'd be more than happy to. I just upped the logging level to level 3. Where do I find the proper unbound log? And where might I find the redirect setting(s) you speak of that could cause this problem?
-
@reddelpapa said in DNS Resolver/Forwarder host overrides not working:
private-domain: "google.com"
domain-insecure: "google.com"Why do you have that set?
And yes pfblocker could for sure becausing you problems.
-
@johnpoz
I have no idea how that got set, or how. I was fooling with google.com and test.google.com overrides to see if they were broke too and the answer is yes.So then, what do you suggest? I have a test version of pfsense running in a VM. Maybe I can restore it to defaults, configure host overrides and see if it works there. If so, then I'll one by one load the same packages I have on my production box and see if pfblocker breaks it.
-
I can tell you for fact out of the box host overrides just work.. So yeah you got something odd going on..
Click on your custom options box in your unbound config - what do you have in there?
Do you have anything set in your port forwards on your lan interface?
I would set unbound to log queries, you can do that with
server:
log-queries: yesIn your custom option box and then sure up the logging level in the setting.
Now when you do a query for your host override you will see it in the log
Mar 1 10:45:03 unbound 7669:0 info: 192.168.9.100 aaatest.google.com. A IN
$ dig @192.168.9.253 aaatest.google.com ; <<>> DiG 9.12.3-P1 <<>> @192.168.9.253 aaatest.google.com ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 21606 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;aaatest.google.com. IN A ;; ANSWER SECTION: aaatest.google.com. 3600 IN A 11.11.11.11 ;; Query time: 0 msec ;; SERVER: 192.168.9.253#53(192.168.9.253) ;; WHEN: Fri Mar 01 10:45:03 Central Standard Time 2019 ;; MSG SIZE rcvd: 63 -
I have nothing in the custom options box. No lan port forwards.
Nothing extra is showing in the dns resolver log. Where exactly is this log?
-
Its in where all the other logs are ;)
There where did the customs stuff for google come from?
Seems to me you got something tweaked up!!
Did you put in the setting for query logs?
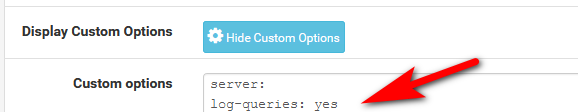
If you want to see the queries for logs.. Is anything happening there - all your other clients asking for stuff that you say is being done by unbound?
-
@johnpoz
Yes sir. I did that exactly as you show. Yes clearly this system isn't working. I'm gonna do as I explained with my VM install of pfsense. Take it to defaults with no addon packages and see if the host overrides work there. -
@johnpoz
So some progress has been made. pfblocker and suricata are not effecting my problem. I also had BIND installed but not running. I uninstalled the package and now my DNS resolver host overrides return this:
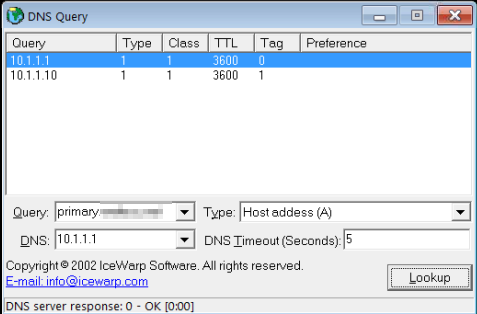
The second IP is the correct one. Now how do I get rid of the 10.1.1.1? -
So you had bind running would be my guess.. And unbound wasn't running.. That completely explains the problem!!!
And your not going to get rid of the 2nd one.. if pfsense is called primary.domain.tld that it will return the IP of its lan IP..
You can not just create another primary.domain.tld and not return that address.
Call pfsense something else!!! like pfsense.domain.tld vs primary.domain.tld - then you can create your host override pointing to what you want.
-
@johnpoz
No, I verified that unbound was indeed running. BIND was installed, but disabled.
Ok I can do that. I will give pfsense a different host name and that problem should be solved.On another topic, I have another problem. Do you know how I can make the windows OpenVPN clients actually run in service mode so that they will connect without any user needing to be logged on? I've tried everything I've searched for online but nothing works.