VPN clients can't access Internet
-
Hey everyone! So I set up CARP VIPs yesterday (with an existing IPsec VPN setup) and it's working great with one exception... Before I set up HA, VPN clients would route all of their network traffic over the VPN tunnel. Now they can still connect to the VPN server, and they can access the internal network, but they can't get out to the Internet (my Windows 10 computer falls-back to its locally-connected network for Internet access).
I've reviewed NAT, firewall rules, VPN config and I'm completely stumped. I've Googled for hours and I've found numerous posts on not being able to ping the secondary node (which is working since I created the Outbound NAT rule) but have found nothing on VPN clients having no Internet access through the VPN connection. I'm hoping someone could help point me in the right direction.
Thanks in advance!
-- Chris -
Be sure the VPN tunnel network is properly covered in your outbound NAT rules.
You'll probably want to post them for us to look at.
There is not really anything in HA other than that that could affect this.
Either way we're going to need a much more detailed picture of what you have there.
-
Ah yes, sorry. Makes sense in hindsight lol... Here are my outbound NAT rules for the VPN.
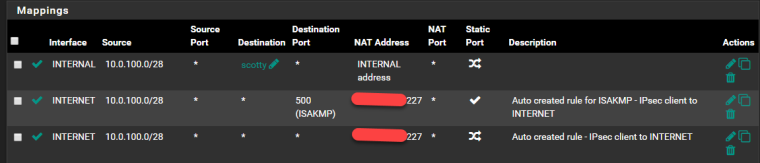
The top rule is so VPN clients can access the secondary node. The bottom two are for the VPN network to access the internet. The NAT address (ending in 227) is one of 3 CARP addresses on the WAN interface. Not sure if it matters but VPN connections also come in on that address.
-
@cemyl95 said in VPN clients can't access Internet:
Now they can still connect to the VPN server, and they can access the internal network, but they can't get out to the Internet (my Windows 10 computer falls-back to its locally-connected network for Internet access).
Sounds like an issue on the windows computer. pfSense can only route traffic it receives.
-
I'm not sure that's the case, my Android phone is experiencing the same thing. Those NAT rules look good though right?
-
NAT rule looks fine as long as the traffic being processed is sourced from 10.0.100.0/28 and outbound connections work sourced from the .227 address.
-
I reviewed the settings on my Android phone (using the StrongSwan VPN client to connect). There's nothing under the "split tunnel" settings that would modify the default of all traffic going through the VPN tunnel, yet it's still not sending Internet traffic over the VPN tunnel. Here are my VPN server settings.
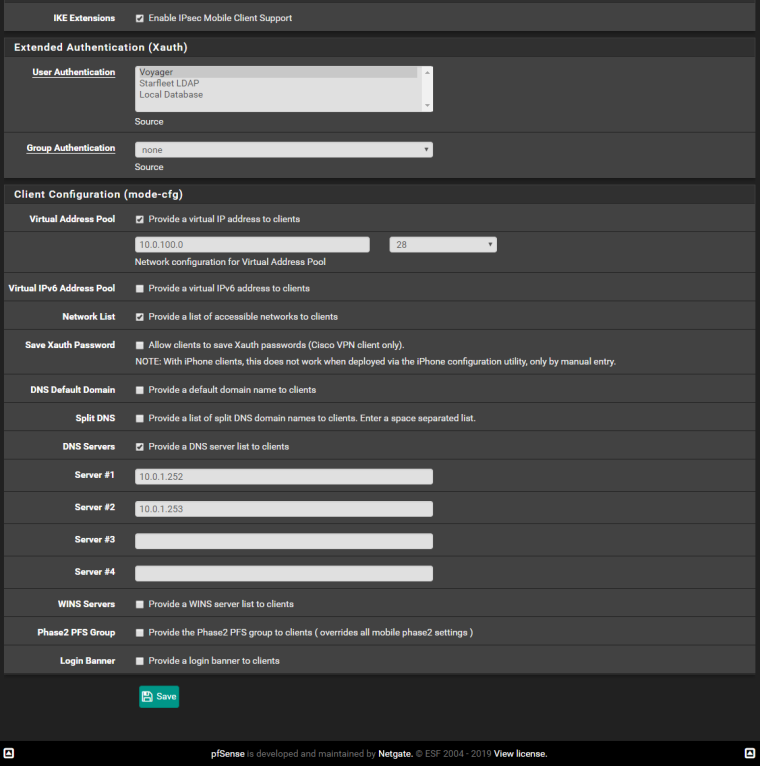
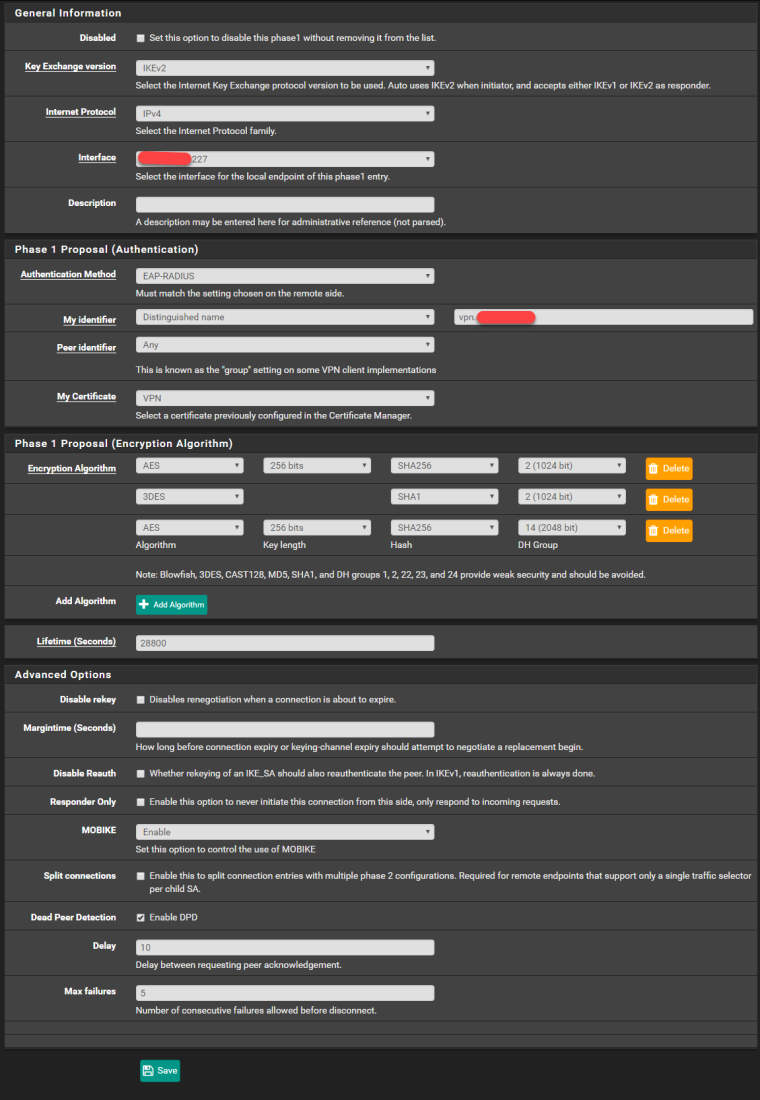
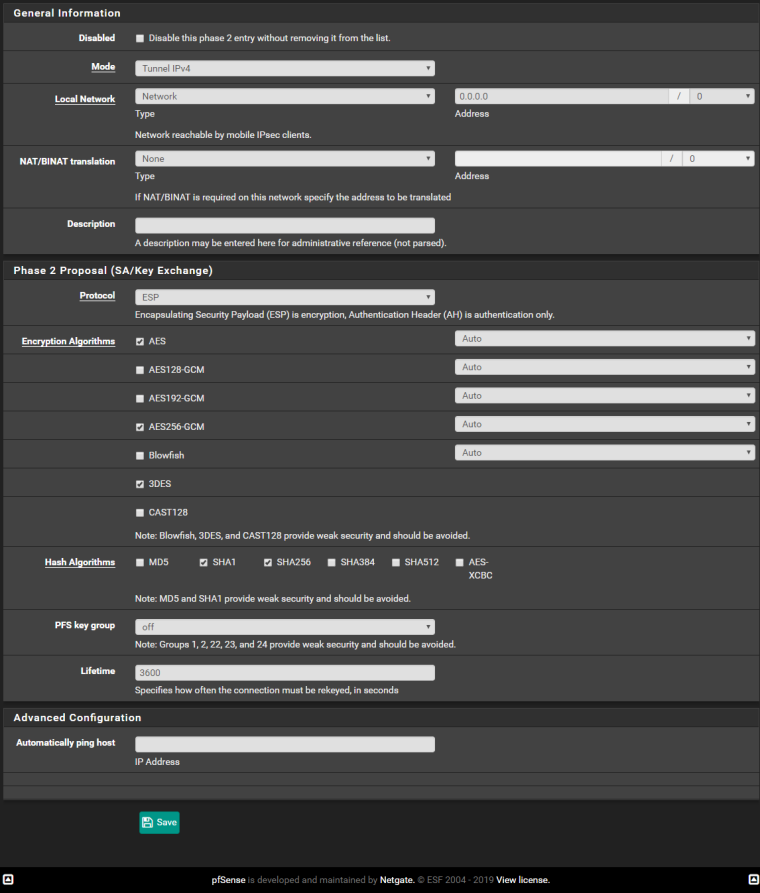
-
If it is still not sending traffic over the VPN then what should the server do about that? It is already being instructed to provide a network list and that list is 0.0.0.0/0.
pfSense cannot route and NAT traffic the client does not send to it.
You might packet capture on the IPsec interface for host address 10.0.100.0/28 and see what, if anything, the client is trying to send over the tunnel and what the disposition of that traffic flow is.
-
I did the packet capture like you suggested, and I saw DNS requests coming over the VPN tunnel but nothing that was destined for the Internet. That got me thinking, so I checked my default route while connected to the VPN. Sure enough, the default route was to the local network gateway (instead of the VPN connection). I dug through my VPN settings a little and found that the "Use default gateway on remote network" wasn't checked. Checked that box, reconnected, and now it works!
@Derelict thank you for your help! ^_^ I was banging my head against a wall trying to figure this out lol
Documenting my solution:
- Go to the interface settings for the VPN interface
- Go to the Networking tab and open IPv4 properties
- Open the Advanced window and check the "Use default gateway on remote network"