Default unbound DNS-over-TLS - Potential MITM Issue By Not Verifying Certificate?
-
I was reading up on unbound on another blog and wanted to see pfSense's current implementation. I'm currently using DoT to 1.1.1.1 and 1.0.0.1 successfully.
Looking at the unbound config file:
/var/unbound/unbound.conf
Here's how pfSense configures the forward zone:
# Forwarding forward-zone: name: "." forward-tls-upstream: yes forward-addr: 1.1.1.1@853 forward-addr: 1.0.0.1@853Here's what I'd like to see:
# Forwarding forward-zone: name: "." forward-tls-upstream: yes forward-addr: 1.1.1.1@853#cloudflare-dns.com forward-addr: 1.0.0.1@853#cloudflare-dns.comAnd for those using Quad9:
forward-addr: 9.9.9.9@853#dns.quad9.netThe article states that the "#" is not actually a comment but specifies the CN for unbound to verify with the upstream DoT server. Without specifying "#cloudflare-dns.com", for example, it potentially opens up a MITM scenario that allows self-signed certificates from an attacker.
It would be nice if there was a way for us to specify in the WebUI (maybe in General Setup where we specify the DNS servers?) the FQDN/CN of the DNS-over-TLS certificate that applies for each entry, which then gets added to unbound.conf.
-
@finger79 said in Default unbound DNS-over-TLS - Potential MITM Issue By Not Verifying Certificate?:
It would be nice if there was a way for us to specify in the WebUI (maybe in General Setup where we specify the DNS servers?) the FQDN/CN of the DNS-over-TLS certificate that applies for each entry, which then gets added to unbound.conf.
Heck, it may be easier to completely separate the System DNS (in General Setup) with the unbound settings. In other words, keep the System DNS UI in General Setup as-is, but instead of unbound pulling from General Setup, have separate text fields that only unbound uses (Servces --> Resolver). This has the added benefit of easier UX since I've seen many users (myself included) confuse the DNS entries that pfSense itself uses on localhost vs. what unbound uses.
-
Yes, there is a potential for MITM, but Unbound could not validate hosts at first due to the OpenSSL version used on pfSense. They recently put out an updated version that can, though their fix was incomplete so we had to submit a patch to fix that.
Read through all the history here: https://redmine.pfsense.org/issues/8602
tl;dr: It will be possible on pfSense 2.5.0, and maybe on 2.4.x if we have to make another release there.
-
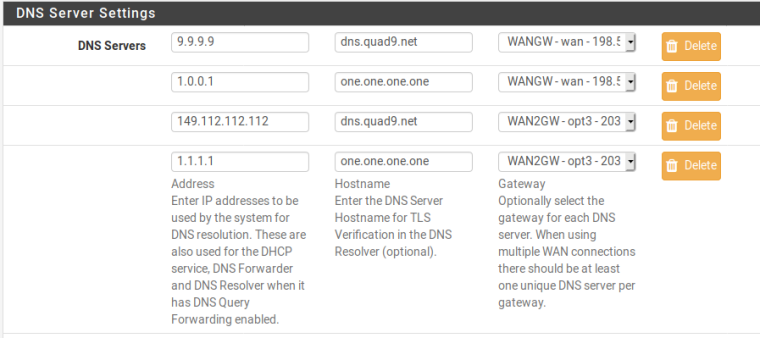
Meant to tack this onto my earlier reply. Here is a screenshot of how you set the hostname for DNS over TLS verification on 2.5.0: