how to config NAT/interface for external ips
-
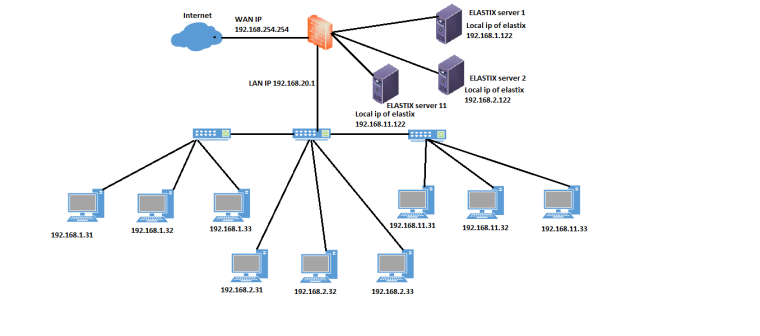
Here's my network plan.
INterface.
WAN 192.168.254.X
Lan 192.168.20.1
OPT1 for elastix server dot 11, local ip server 192.168.11.122
OPT2 for elastix server dot 2, local ip server 192.168.2.122
what i would like:
i plan to opt1 is same network address of server elastix, for not reconfig the 3cx or phones
Opt1 same plan to opt 2
rules for each interface
opt1
no internet access, block connection to option 2
Option 2
with internet access, block connection to option 1
would help me with my plan. or give me a step by step, how to do it.
-
pls help me :(
-
It looks like you have the client machines in subnets routed via LAN but those also look like the subnets the server are in. Unless those subnets are not /24. That would be a conflict if they are /24, you can't have the same subnet locally and routed.
What exactly are you trying to achieve here? What do you have currently?
Steve
-
yeah if your routing those 192.168.1, .2, .11 etc. to some downstream router via the transit 192.168.20 then those servers should connect into the L2 network off the downstream router.
Are you trying to use some bigger than /24 masking on all of these networks? like maybe a /20 for example?
-
The question for me is... is your diagram just a quick mockup to give us an idea of what you want to do or is everything already physically connected that way?
A high-level, straight forward approach for accomplishing your goals would be:
- Create VLANs on the PFsense LAN interface
- Consolidate down to 1 managed switch and connect it to PFsense via a trunked interface
- Connect everything to the managed switch
- Configure firewall rules to control access as necessary
There's no way to accomplish everything you're looking for as currently shown in your diagram. If you keep the transit network, you can establish connectivity by moving your servers to one of the other switches, but that would mean your VLANs would be terminated on the middle L3 switch and you'd lose inter-vlan firewalling capability. This would be the favorable design from a performance standpoint, but you lose granularity in your access control.
If you want to keep the 3 switches and require inter-vlan firewalling, you can still accomplish your goals, but it would require a re-design and managed switches. You'd need to:
- Create VLANs on the PFsense LAN interface
- Re-configure the link between PFsense and the middle switch as a trunk
- Trunk the two outside switches to the middle switch
- Move your servers to any of the three switches
If everything is in close proximity, personally I would consolidate down to one managed switch to keep it simple.
Regardless of your design choice, in order to fulfill all of your requirements, all roads lead to managed switches and a re-design.
