pfSense route some VLANs use L3 switching for the others
-
After some monkeying around I think I finally have my network setup to accommodate routing at the switch level. I'm doing this because my homelab has gotten busy enough that traffic between my esxi box on VLAN 70 and my NAS on VLAN 20 is bringing pfSense to it's knees because snort can't keep up with the traffic on my c2758.
I was wondering if it can be done or is advisable to let pfSense handle routing VLAN 10, 30, 40, 50 and 60 and having VLAN 20 and VLAN 70 routed on my switch?
I currently have VLAN 10, 20, 30, 40, 50, 60, and 172 interfaces configured.
My core switch is hooked up to pfSense with 172up, 10T, 20T, 30T, 40T, 50T, 60T, 70T. It's default route is 172.36.1.1 and has an interface for VLAN 10 (management)
My second switch is LACP'd to the first passing tagged traffic and no other interfaces other than VLAN 1.
In googling I don't see any examples where pfSense routes some VLANs and others are handled at the switch. I'm starting to get a sense there is a reason for that lol.
So my question is, can this be done? Also, I read that if you let the switch handle routing, you have to have a separate DHCP server because pfSense needs to route the traffic to provide DHCP?
At this point I'm wondering if tearing up my network just for these two boxes is stupid, and I should just have my esxi host have one link on the DMZ 70 VLAN and use it's other 3 NICs to have access on VLAN 20. It would allow for fast traffic over layer 2 for IO and only serve up content on the DMZ VLAN. I know it's not the most secure, but I don't know which way to go for a lab that has shared storage that provides for the LAN and DMZ.
-
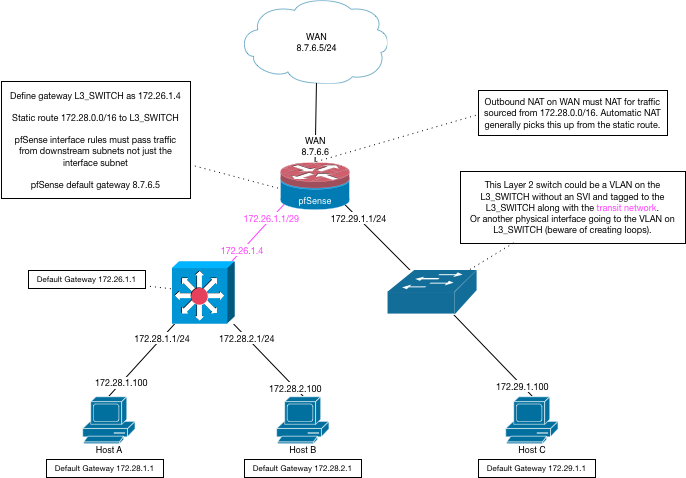
Yes. You can do that no problem. A Layer 3 switch VLAN without a layer 3 interface defined on it is just like any other Layer 2 switch. Just tag the VLAN to it and make a pfSense interface for that VLAN.
Yes, you can make a transit network and route other VLANs to the switch for routing across its Layer 3 interfaces (will not include the Layer 2 VLANs above).
Yes, pfSense can only serve one DHCP scope on an interface so you will have to make other arrangements.
My inside network and lab is backed by a Brocade ICX-6450 with premium L3 software.
I have 2x1G LACP to it. Over that is tagged a bunch of VLANs to L2 VLANs on the switch. These work fine. pfSense DMZ interface assigned to VLAN 224 on lagg0 for instance.
One of these tagged networks is a transit /29 interface to a Layer 3 VLAN on the switch. I run OSPF over this between pfSense (FRR) and the switch so if I add a L3 network or a route on the switch, pfSense knows about it immediately - and vice versa. The switch routes between its Layer 3 VLANs.
I would not put any shared storage through a firewall at all. At least not VM disks. I have dedicated 10Gx2 LACP between the Proxmox host and FreeNAS for that. And it's still not "fast enough".
-
@Derelict Again, thanks for your patience, I think I'm slowly getting there.
I actually just bought a new piece of kit for storage so I can completely isolate personal storage vs dmz storage.
I tried making the setup above work with mixed results. I tried to setup a transit VLAN, but I'm not sure that it's how it's supposed to be configured.
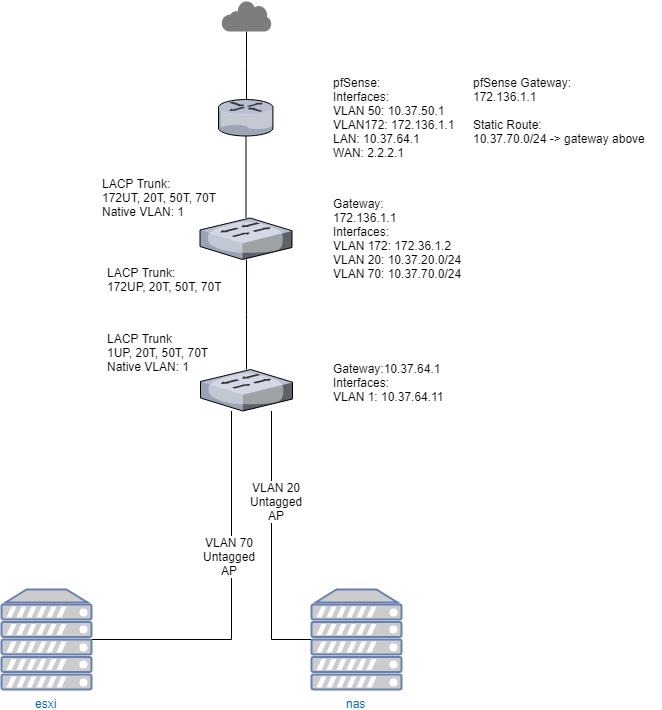
The inter-vlan part of that diagram makes sense to me. What I'm trying to comprehend is something that comes from VLAN 20 or 70 at the bottom and then routes back up.
Using VLAN 20 as an example, It'll hit the first switch, and it'll just pass it up (tagged) to the core switch. At that point there is a VLAN 20 interface there. That will in result, strip it's tag. Seeing nothing in the routing table for where it wants to go, it will then pass it up to the default route of that switch. I'm assuming this will come out as the native VLAN (in my case 1), since it is a tagless packet at this point. That would mean it would end up in pfSense as the "LAN" interface, correct?
Should I set the native VLAN on my core switch to be 172, the same as the transit VLAN? Right now the only thing that is being sent over the transit VLAN is the admin interface for that VLAN, right?
-