DNS over TLS
-
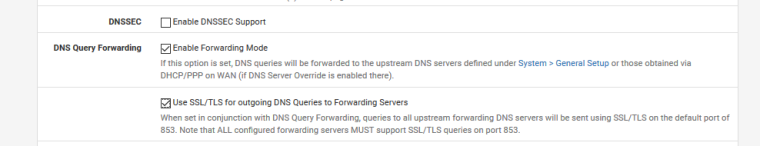
I am currently running pfsense version 2.4.4 (p2) and have tried to enable DNS over TLS by ticking Enable DNSSEC support, Enable Forwarding Mode and Use SSL/TLS for ourgoing DNS Queries to forwarding servers (under DNS Resolver - General Settings). I have also configured the DNS Forwarders as Quad 9 (9.9.9.9 and 149.112.112.112 - under System - General)
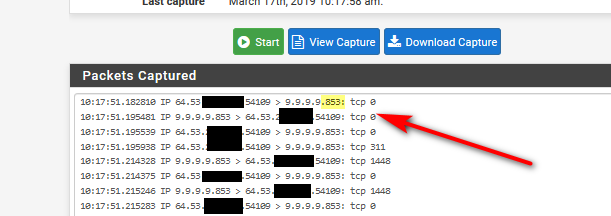
However, when I then do a packet capture on the WAN interface, I notice traffic still goes to 9.9.9.9:53, rather than 9.9.9.9:853, with the domain lookup clearly in plain text.
Any idea what I am doing wrong?
-
why don' you post up what you did on the unbound config (picture!!).. For starters dnssec has ZERO to do with dns over tls.. And if your going to forward, clicking to use dnssec is completely utterly POINTLESS.. Since your forwarding.. If your forwarding to a resolver and it is doing dnssec, you have nothing to do on the client side, ie pfsense.
Sniff
-
Pictures as requested:
-
So pfsense wan is 192.168.2.2?
So unbound actually restarted after you made the change?
-
Yes, 192.168.2.2 is the WAN interface (it goes through an Edge Router before hitting the internet).
I have restarted the unbound service several times but still get port 53.
-
So what DNS are your clients using? Also pfSense itself is probably using the Quad 9 servers directly. Any (proxy) packages running?
-
^ yup that could just be a client behind pfsense asking? You need to block them from using anything other than pfsense, or you need to redirect all dns to loopback on pfsense, etc.
Do you see any traffic at all to 853, when you specifically ask for something that your sure is not cached, etc.
-
@johnpoz The clients use pfsense for DNS and there are redirect rules, to force them to use pfsense. The packet capture was done using pfsense DNS lookup (under diagnostics).
The only thing relevant could be DNS filtering using DNSThingy, the are no proxys being used.
-
@ianjanus said in DNS over TLS:
The packet capture was done using pfsense DNS lookup (under diagnostics).
And this will also use the DNS servers configured in the general settings directly. Test from a client.
-
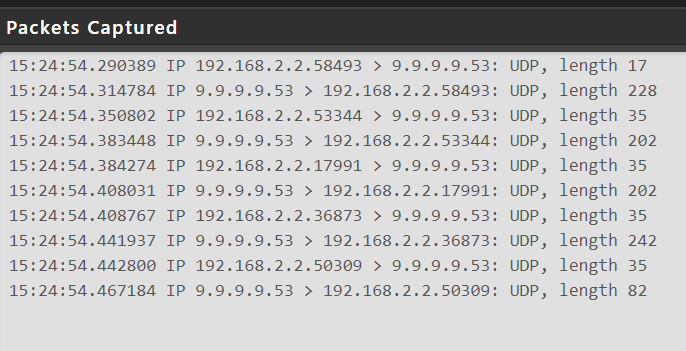
And again going to ask are you seeing any traffic to 853?
You do understand that pfsense, or the diagnostic lookup could be asking all your listed dns, be it loopback which would use tls or directly which would not be using tls.
A better setting for this would prob be to set the forwarders directly in unbound, vs setting them in general.. That way you can pfsense only use loopback - which would then not be possible to ask dns directly
-
Correct I see no traffic using 853 only 53. I have redirects so all DNS queries undertaken by clients always go to pfsense loopback address.
I have tried dns lookup from clients and from pfsense but still get the same result.
I think I need to investigate if DNSThingy is incepting DNS queries, so I have logged a ticket with them.
-
Well its click click... You actually sure unbound restarted? I just showed you how easy it is to turn on and off... I personally don't do it - because its just stupid.. Its like how can I slow down my dns.. OH yeah - let me throw it inside a tls tunnel and hand all my dns queries to company X, etc.
You sure unbound is even running and your not running the forwarder, etc.
Unbound will show you what its doing, set the log to level 2 in the advanced tab
Mar 17 14:22:46 unbound 60954:0 info: reply from <.> 9.9.9.9#853
Look in your conf... Do you see the forwarding section in there
2.4.4-RELEASE][admin@sg4860.local.lan]/: cat /var/unbound/unbound.conf
# Forwarding forward-zone: name: "." forward-tls-upstream: yes forward-addr: 9.9.9.9@853Now clicky clicky back to resolving like any sane human would want to do ;)
You sure your not redirecting to 9.9.9.9 directly? Lets see your redirect rule, etc.