failing to connect with strongSwan
-
Hi all,
I'm on 2.4.4-RELEASE-p1
I've set up IPSec following Netgate pfSense Book dated Aug 2018.
A screenshot showing an overview of my settings attached:
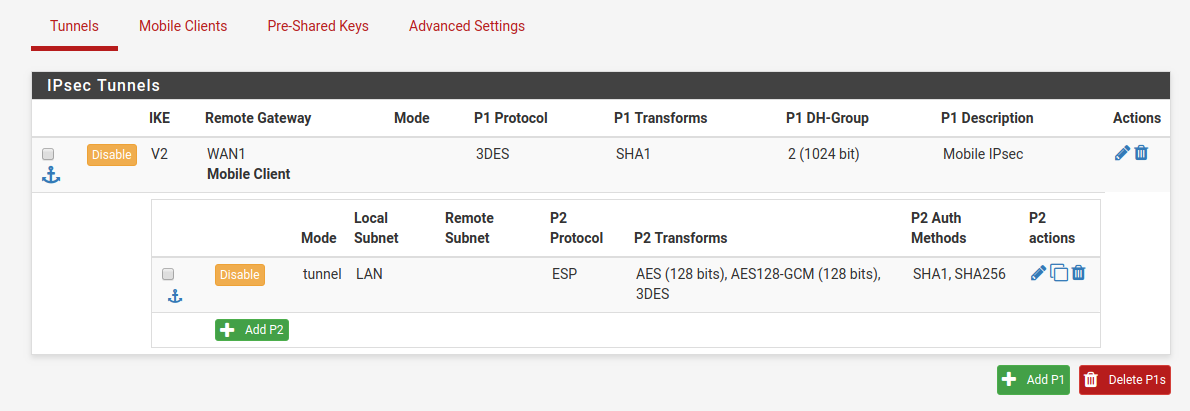
I can connect fine from Windows 10 with both routing and DNS working and from MacOSX with routing but without DNS as yet.
Unfortunately I can't get that far with strongSwan for Android (the latest version as of today).
I've triple checked my username and password and I'm using exactly the same as in Pre-Shared Keys (EAP type).
It works in other clients / OS'es anyway.server IP xxx.xxx.xxx.xxx
client IP yyy.yyy.yyy.yyyMy client side logs:
Mar 19 12:37:46 00[DMN] +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ Mar 19 12:37:46 00[DMN] Starting IKE service (strongSwan 5.7.2, Android 8.0.0 - R16NW.G935FXXS4ESAE/2019-02-01, SM-G935F - samsung/hero2ltexx/samsung, Linux 3.18.91-14843133-QB21795979, aarch64) Mar 19 12:37:46 00[LIB] loaded plugins: androidbridge charon android-log openssl fips-prf random nonce pubkey chapoly curve25519 pkcs1 pkcs8 pem xcbc hmac socket-default revocation eap-identity eap-mschapv2 eap-md5 eap-gtc eap-tls x509 Mar 19 12:37:46 00[JOB] spawning 16 worker threads Mar 19 12:37:46 06[IKE] initiating IKE_SA android[29] to xxx.xxx.xxx.xxx Mar 19 12:37:46 06[ENC] generating IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Mar 19 12:37:46 06[NET] sending packet: from 100.87.12.210[40815] to xxx.xxx.xxx.xxx[500] (716 bytes) Mar 19 12:37:46 10[NET] received packet: from xxx.xxx.xxx.xxx[500] to 100.87.12.210[40815] (297 bytes) Mar 19 12:37:46 10[ENC] parsed IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Mar 19 12:37:46 10[CFG] selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Mar 19 12:37:46 10[IKE] local host is behind NAT, sending keep alives Mar 19 12:37:46 10[IKE] received cert request for "CN=MyServer-CA, C=GB, ST=England, L=London, O=MyCompany" Mar 19 12:37:46 10[IKE] sending cert request for "CN=MyServer-CA, C=GB, ST=England, L=London, O=MyCompany" Mar 19 12:37:46 10[IKE] establishing CHILD_SA android{29} Mar 19 12:37:46 10[ENC] generating IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Mar 19 12:37:46 10[NET] sending packet: from 100.87.12.210[39158] to xxx.xxx.xxx.xxx[4500] (480 bytes) Mar 19 12:37:46 11[NET] received packet: from xxx.xxx.xxx.xxx[4500] to 100.87.12.210[39158] (80 bytes) Mar 19 12:37:46 11[ENC] parsed IKE_AUTH response 1 [ N(AUTH_FAILED) ] Mar 19 12:37:46 11[IKE] received AUTHENTICATION_FAILED notify errorServer side:
Mar 19 12:37:50 charon 10[NET] <52> received packet: from yyy.yyy.yyy.yyy[15296] to xxx.xxx.xxx.xxx[500] (716 bytes) Mar 19 12:37:50 charon 10[ENC] <52> parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) N(REDIR_SUP) ] Mar 19 12:37:50 charon 10[IKE] <52> yyy.yyy.yyy.yyy is initiating an IKE_SA Mar 19 12:37:50 charon 10[CFG] <52> received proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/CHACHA20_POLY1305/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Mar 19 12:37:50 charon 10[CFG] <52> configured proposals: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Mar 19 12:37:50 charon 10[IKE] <52> no matching proposal found, trying alternative config Mar 19 12:37:50 charon 10[CFG] <52> selected proposal: IKE:AES_CBC_128/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256 Mar 19 12:37:50 charon 10[IKE] <52> remote host is behind NAT Mar 19 12:37:50 charon 10[IKE] <52> sending cert request for "CN=MyServer-CA, C=GB, ST=England, L=London, O=MyCompany" Mar 19 12:37:50 charon 10[ENC] <52> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(MULT_AUTH) ] Mar 19 12:37:50 charon 10[NET] <52> sending packet: from xxx.xxx.xxx.xxx[500] to yyy.yyy.yyy.yyy[15296] (297 bytes) Mar 19 12:37:50 charon 10[NET] <52> received packet: from yyy.yyy.yyy.yyy[54459] to xxx.xxx.xxx.xxx[4500] (480 bytes) Mar 19 12:37:50 charon 10[ENC] <52> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) CERTREQ CPRQ(ADDR ADDR6 DNS DNS6) N(ESP_TFC_PAD_N) SA TSi TSr N(MOBIKE_SUP) N(NO_ADD_ADDR) N(MULT_AUTH) N(EAP_ONLY) N(MSG_ID_SYN_SUP) ] Mar 19 12:37:50 charon 10[IKE] <52> received cert request for "CN=MyServer-CA, C=GB, ST=England, L=London, O=MyCompany" Mar 19 12:37:50 charon 10[CFG] <52> looking for peer configs matching xxx.xxx.xxx.xxx[%any]...yyy.yyy.yyy.yyy[user@mycompany.com] Mar 19 12:37:50 charon 10[CFG] <bypasslan|52> selected peer config 'bypasslan' Mar 19 12:37:50 charon 10[IKE] <bypasslan|52> peer requested EAP, config unacceptable Mar 19 12:37:50 charon 10[CFG] <bypasslan|52> no alternative config found Mar 19 12:37:50 charon 10[IKE] <bypasslan|52> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Mar 19 12:37:50 charon 10[IKE] <bypasslan|52> peer supports MOBIKE Mar 19 12:37:50 charon 10[ENC] <bypasslan|52> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Mar 19 12:37:50 charon 10[NET] <bypasslan|52> sending packet: from xxx.xxx.xxx.xxx[4500] to yyy.yyy.yyy.yyy[54459] (80 bytes)Why is it failing and how to fix it?
Anything to do with choice of ciphers?Thanks,
Adam
Copyright 2025 Rubicon Communications LLC (Netgate). All rights reserved.