Firewall Logs
-
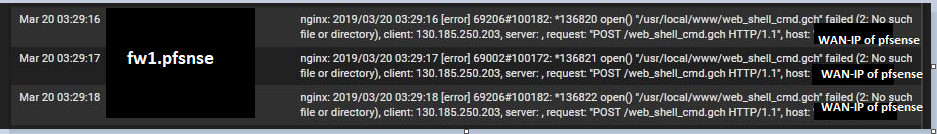
Hi, need inputs here can someone explain to me what's this logs all about? is this an example of attacks?
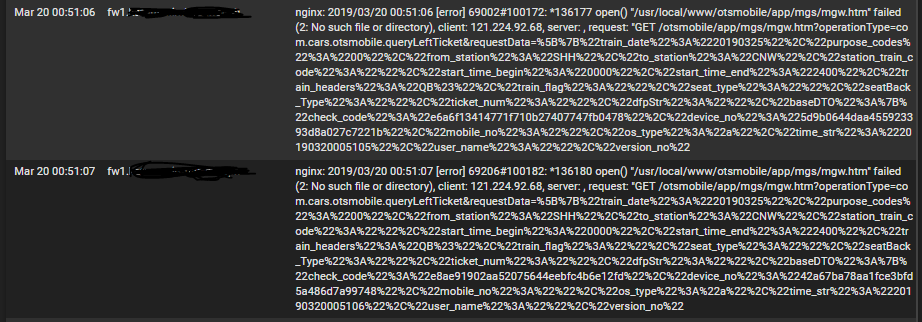
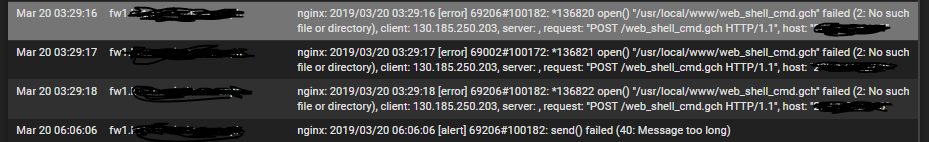
Thank You
-
Attack ?
Can't tell, you've hidden all the info that's needed to answer.edit : If these web server requests come from LAN - one of your 'trusted' devices, then yes, not really an attack but it contains rather stupid software.
The "/usr/local/www/" path is the web root of the pfSense GUI.
It makes no sense that a page called /otsmobile/app/mgs/mgw.htm is called.
So local wifi mobile device connected with a rather brain dead OS or App.
Just locate the IP of this device- the host with le LAN IP (why hiding a LAN IP ??), find the guy that has this device in his hand and ask him to leave your site - or change Wifi codes and don't give him the new access. -
@Gertjan the erase info is the domain name and public IP of the box.
-
@Jawhead said in Firewall Logs:
public IP of the bo
Yep, just found the IP : 130.185.250.203 - dono who that is - and dono why the GUI can be reached by a remote IP like that.
Did you open the access to pfSense GUI from WAN ? If so, don't worry, this is normal - and things will get really worse very soon.
Or is one of these IP's your WAN IP, and some LAN device is hitting the pfSense GUI by it's WAN IP ?
-
Yes, Our pfSense is accessible publicly via domain and public IP. but only https port is open.
Do you think there are bad guys playing around?
-
Yeah something is trying to hit a page in the firewall that doesn't exist either maliciously or through poor config.
I would guess from those URLs they are trying to hit commonly exploitable pages.
If that's coming from the WAN why is that open?
If it's coming from the LAN something there maybe compromised. Could still just be something badly configured.
Lock down the GUI access.
Steve
-
@Jawhead said in Firewall Logs:
Do you think there are bad guys playing around?
Noop.
These page requests /posts are looking harmless.
For now.Having the GUI open and accessible from the Internet is pure madness.
-
@stephenw10 Hi Steve, thanks for the inputs, We use to manage remotely the firewall. What would you recommend for locking down the firewall? Is there a guide for hardening a pfSense?
-
In one word : OpenVPN.
-
@Gertjan Yes, we have used OpenVPN to access internal server, any other options aside from OpenVPN.
-
If you are already using OpenVPN, you have two choices :
Modify the current setup, so you can access the GUI from LAN, when you are connected to the "internal server".
Or, activate an independent OpenVPN server on pfSense - use another port number if 1194 is already natted to your "internal server".
I guess you have already all the knowledge needed to access the GUI over OpenVPN. The big advantage is that only the people user credentials and/or certs can access the GUI. -
@Jawhead said in Firewall Logs:
Yes, Our pfSense is accessible publicly via domain and public IP. but only https port is open.
Yeah that is just plain moronic to be honest.... Yeah your logs are going to be full of shit for starters..
As suggested vpn in to manage, or atleast lock down the access to the gui from your source IP your going to be managing from.
-
That looks like the kind of stuff you see from captive portal redirecting requests from unauthenticated clients to the web server.
-
Thank you for the inputs guys really appreciate it, for the meantime, I just disable the public access and push to use OpenVPN instead.