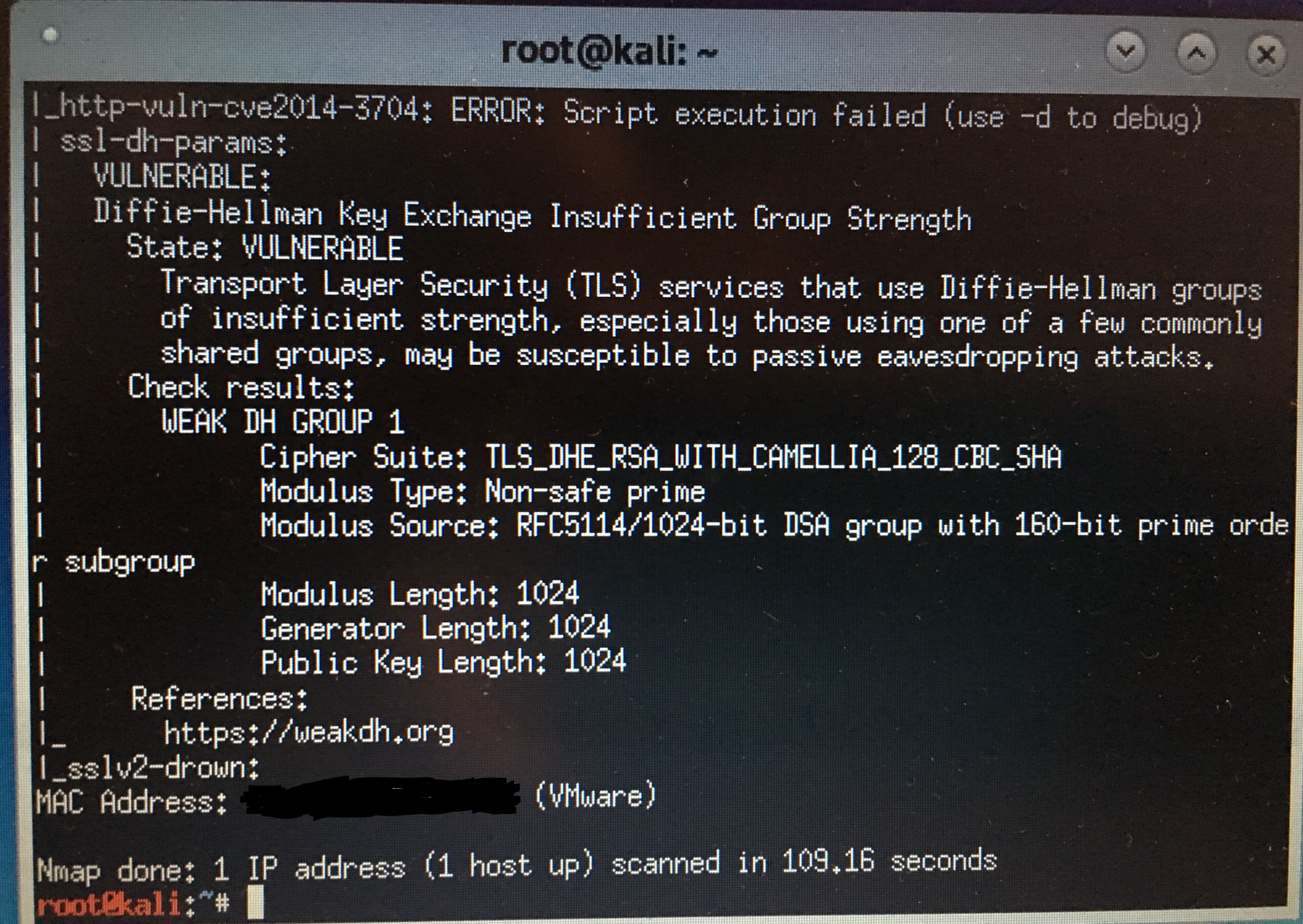
pfSense weak DH vuln found with Kali
-
It uses lighttpd not nginx that is used by the pfSense gui:
https://redmine.lighttpd.net/projects/lighttpd/wiki/Docs_SSLWould have to add the DH params to the dnsbl lighttpd conf file:
var/unbound/pfb_dnsbl_lighty.confThat file is auto created so changes will be overwritten. Don't have time to look at it atm.
-
Yeah my guess but can not seem to find it in the conf is this
ssl.dh-file="{path to dhparams.pem}"So not sure what its using if not called out?
To be honest this isn't really that big of deal - other than people doing such scans and thinking the problem is pfsense ;) hehehe
I set up pfSense and I was checking for general vulnerabilities.
No where did he mention installed "optional" packages xyz, and abc, etc..
-
Well to be fair he did discover something that should probably be updated, if only to prevent false positives as you say.
Steve
-
Edit the file (for pfBlockerNG-devel):
/usr/local/pkg/pfblockerng/pfblockerng.incAnd add the 6 "+" lines as depicted in this screenshot:

$SERVER["socket"] == "127.0.0.1:8443" { ssl.engine = "enable" ssl.pemfile = "/var/unbound/dnsbl_cert.pem" ssl.dh-file = "/etc/dh-parameters.4096" ssl.cipher-list = "EECDH+AESGCM:EDH+AESGCM:AES128+EECDH:AES128+EDH" ssl.ec-curve = "secp384r1" } $SERVER["socket"] == "10.10.10.2:443" { ssl.engine = "enable" ssl.pemfile = "/var/unbound/dnsbl_cert.pem" ssl.dh-file = "/etc/dh-parameters.4096" ssl.cipher-list = "EECDH+AESGCM:EDH+AESGCM:AES128+EECDH:AES128+EDH" ssl.ec-curve = "secp384r1" }Stop the pfb_dnsbl Service
Then remove the existing lighttpd config file.rm /var/unbound/pfb_dnsbl_lighty.confThen Force Update for it to be re-created with the new changes.
Please post back after running your vulnerability scans.
Thanks! -
As always @BBcan177 your johnny on the spot!
And also took the time to update the cipher list and curve.. Nice!
@stephenw10 agree its a good find, even if found in a round about way.
-
@BBcan177 said in pfSense weak DH vuln found with Kali:
rm /var/unbound/pfb_dnsbl_lighty.conf
mac-pro:~ andy$ nmap --script ssl-dh-params.nse 172.16.0.1
Starting Nmap 7.40 ( https://nmap.org ) at 2019-03-26 09:27 GMT
Nmap scan report for pfsense (172.16.0.1)
Host is up (0.0018s latency).
Not shown: 995 filtered ports
PORT STATE SERVICE
22/tcp open ssh
53/tcp open domain
443/tcp open https
8081/tcp open blackice-icecap
8443/tcp open https-altNmap done: 1 IP address (1 host up) scanned in 6.40 seconds
mac-pro:~ andy$Yea that fixed it :)
-
@NogBadTheBad said in pfSense weak DH vuln found with Kali:
Yea that fixed it :)
Thanks for testing... Will add it to the next release...
-
many thanks for checking /helping and fixing it, to all.
Really appreciated!