Need some help with pfSense Site-to-Site IPSec VPN
-
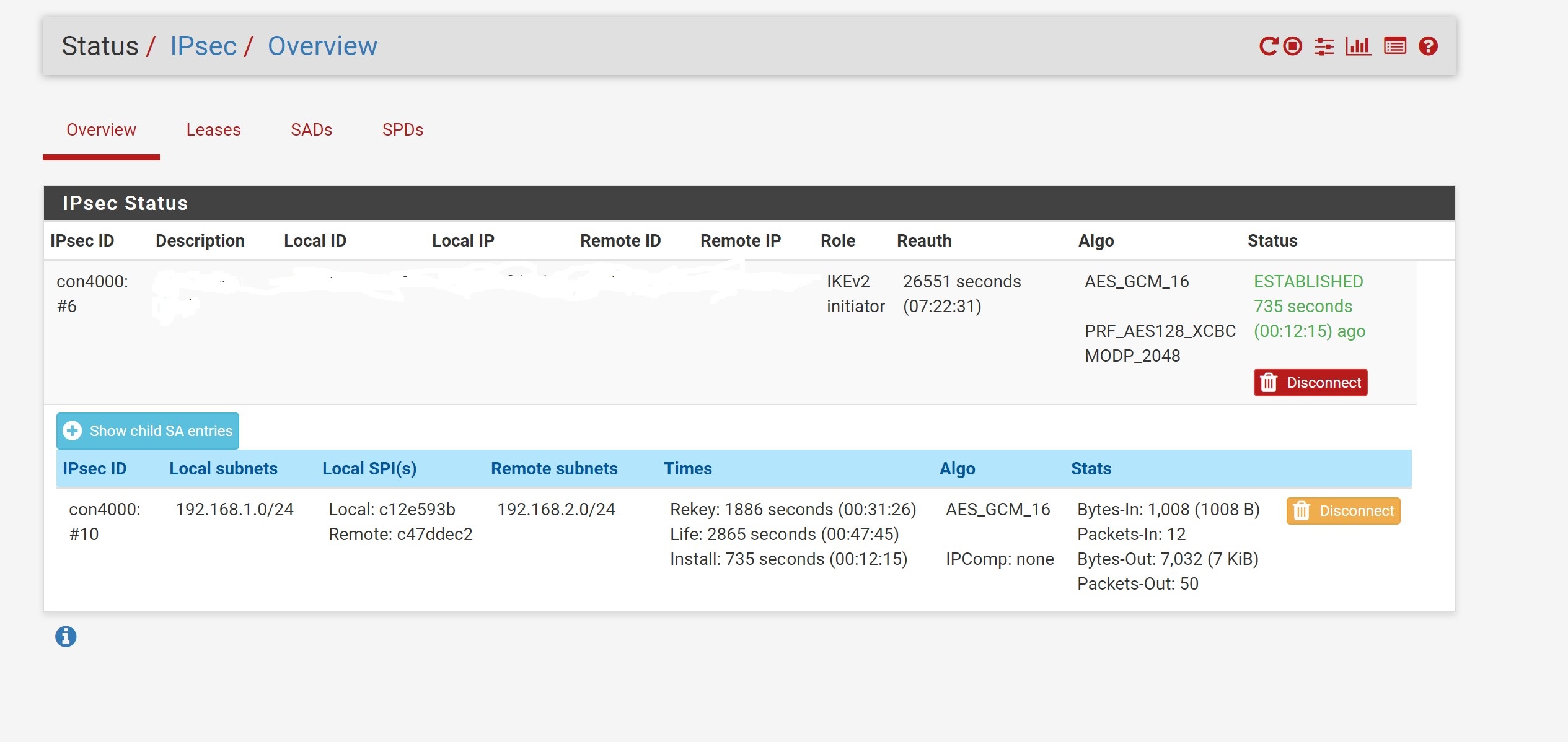
I'm having some trouble configuring a site-to-site IPsec VPN between two pfsense firewalls. The IPsec status screen shows that a Phase 1 connection is established. The Phase 2 status shows traffic leaving the firewall but here is a very little traffic returning, it appears this way on both firewalls.
I have both firewalls configured to allow ICMP which I've validated by pinging the firewalls public IP addresses. When I try to ping the local LAN address for the other firewall the request times out. I checked the firewall logs and there does not appear to be any traffic being blocked. Both firewalls are configured to allow ESP, as well as ports 500 and 4500. The IPsec firewall configuration is setup to allow any traffic to pass. I've also made sure both pfSense instances are using the same encryption and hashing settings for both phase 1 and phase 2.
The remote network for phase 2 is set to the other firewall's local network (192.168.1.0/24 and 192.168.2.0/24) Any suggestions on how to debug this from here?
I've attached the IPsec log and here's a photo of the status screen:
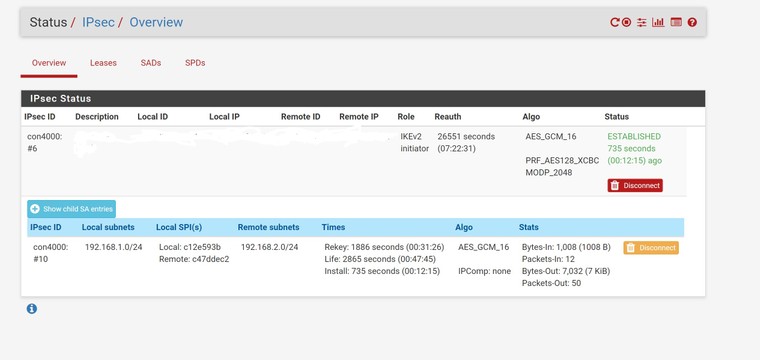
-
Hello,
Can you access remote hosts from your side? Do you have other issues rather than ping requests? Beside this, please attach here the screenshot of "Firewall / Rules / IPSec" of both sides.
-
I'll get back to you with the screenshots of the IPsec firewall rules for the remote tunnel, but both should be configured like the attached screenshot.
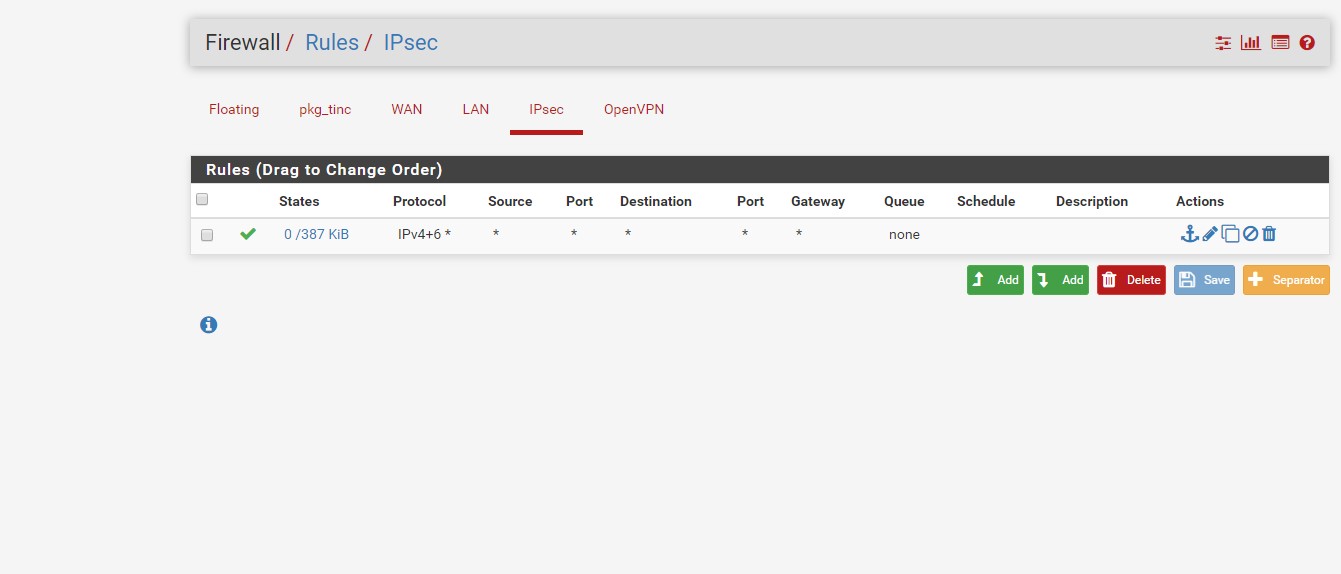
As of right now I'm not able to access any hosts on the remote network, I've tried hitting the remote pfSense console as well as some Web Applications but I haven't had any luck yet.
Thanks,
Zach -
How are you testing? Where are you pinging from? To?
You have to ping from something that has a source address in the local network and a remote address in the remote network.
For instance, if you ping using Diagnostics > Ping you have to set the source address to LAN.
-
Hi,
So I've been testing by pinging the remote gateway from a computer on the network as well as pfSense. I've also tried accessing SMB drives and Web Servers.
Here are some photos of the configuration, my instance is on the left side of the photos.
Thanks
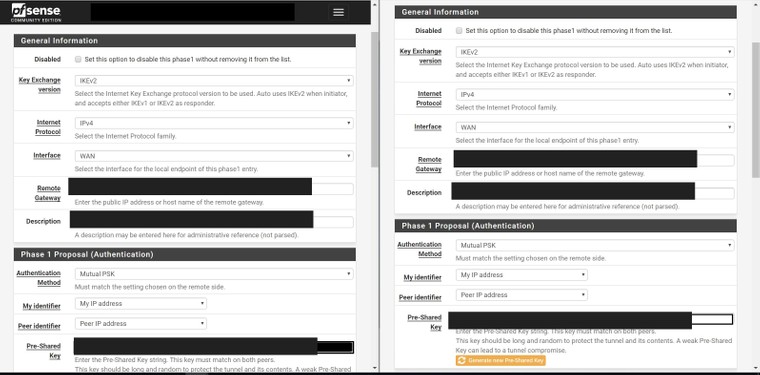
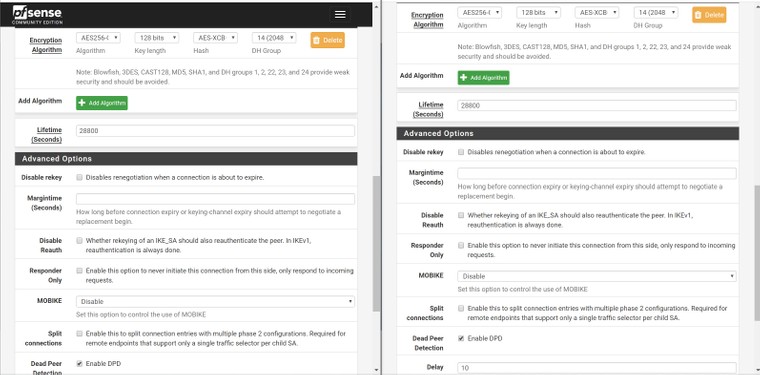
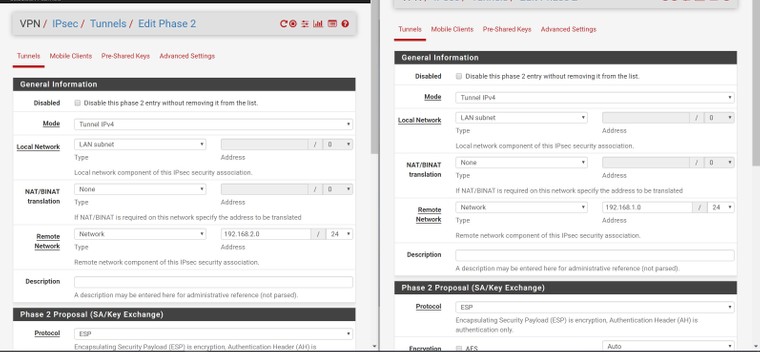
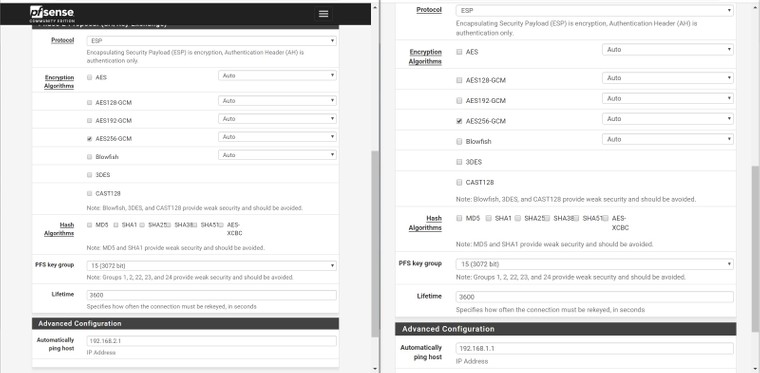
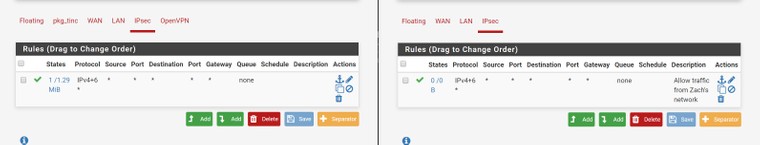
It's also worth mentioning that I'm seeing these messages in the remote gateway:
Mar 28 01:32:05 charon 05[ENC] <con1000|8> parsed INFORMATIONAL response 11 [ ]
Mar 28 01:32:05 charon 05[IKE] <con1000|8> activating new tasks
Mar 28 01:32:05 charon 05[IKE] <con1000|8> nothing to initiate
Mar 28 01:32:07 charon 05[CFG] vici client 540 connected
Mar 28 01:32:07 charon 05[CFG] vici client 540 registered for: list-sa
Mar 28 01:32:07 charon 16[CFG] vici client 540 requests: list-sas
Mar 28 01:32:07 charon 06[CFG] vici client 540 disconnected
Mar 28 01:32:13 charon 06[CFG] vici client 541 connected
Mar 28 01:32:13 charon 06[CFG] vici client 541 registered for: list-sa
Mar 28 01:32:13 charon 12[CFG] vici client 541 requests: list-sas
Mar 28 01:32:13 charon 06[CFG] vici client 541 disconnected -
@zachelks
Hey
Hey
These log messages indicate that you have been to the Webgui page /Status/IPSEC
Show the rules for Lan interfaces on both sides of the tunnel
and try disabling tinc on the left side of the tunnel. -
Hi,
I've disabled the tinc VPN now, but still no luck.
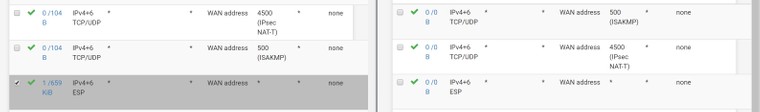
Here is a screenshot of my rules:
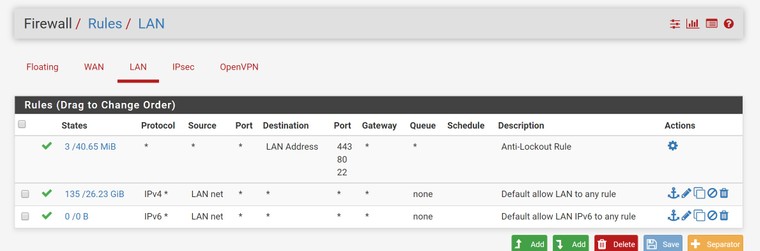
And of the remote gateway:
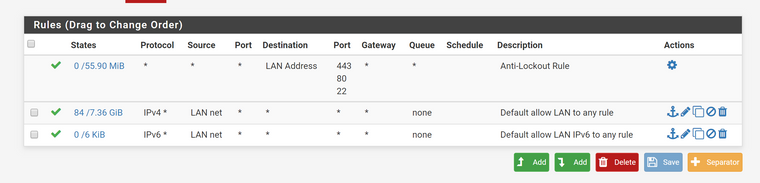
-
@zachelks
Hey
What type of traffic do you have a problem with ?
Screenshots show that everything is configured correctly
Try to reduce MSS ( for example , make it equal to 1360)
VPN/IPsec/Advanced Settings
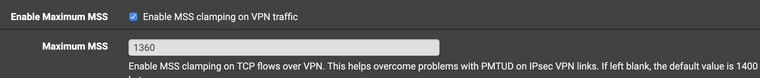
or Try to use a Packet Capture to find the place where the IP packets are being lost
-
@zachelks said in Need some help with pfSense Site-to-Site IPSec VPN:
So I've been testing by pinging the remote gateway from a computer on the network as well as pfSense. I've also tried accessing SMB drives and Web Servers.
That means nothing to anyone but you. Please detail exact tests that are not working. Details like:
Source IP address
Destination IP address
Protocol (get pings (ICMP) working first) -
So the tunnel is mostly working now, I unplugged the AT&T modem and plugged it back in and the tunnel came up. Thanks for your help!
The tunnel is mostly working fine, but I'm now seeing the tunnel drop for a couple minutes every hour, I'm thinking it has something to do with the re-keying. I have ping option set to keep the tunnel alive (it's set to 192.168.1.1 and 192.168.2.1) and the Phase 1 and Phase 2 lifetimes are set to the same value.
I've attached the log from the period where the tunnel is dropping, any ideas how to address this issue?
-
You need to check how many CHILD_SA were active at the time of the rekeying. Judging by the logs there were 2 numbers 180 and 181 . Instead, 2 new active CHILD_SA numbers 182 and 183 were created.
I understand this is a problem because there must be one CHILD_SA for each connection.
Try using The make before break option on the /IPSEC/Advanced settings tab
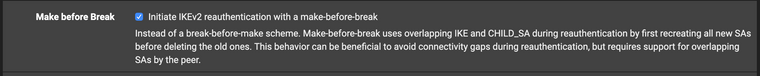
-
@zachelks said in Need some help with pfSense Site-to-Site IPSec VPN:
The tunnel is mostly working fine, but I'm now seeing the tunnel drop for a couple minutes every hour, I'm thinking it has something to do with the re-keying.
So look at the IPsec logs surrounding and including one of these time periods and see what is happening.
-
Hi,
So I ended up resolving this issue, for those who are interested it was an issue with the AT&T modem.
I have the Arris BGW-210 on both sides of the tunnel. The modem has a setting under Advanced Firewall called ESP ALG, this setting should be disabled if both sides of your tunnel are not behind NAT (pfSense has a public IP).
Thanks for your help getting this resolved, the tunnel is working great, I'm seeing over 300 mbps between the networks.