DNS resolve for internal hosts in HA and peer-to-peer OpenVPN
-
Hi!
I'm going to try to explain this.
The question is how to get internal resolving when the HA has failed over to the backup.Config:
- pfSense, 2.4.4-RELEASE (amd64) built on Thu Sep 20 09:03:12 EDT 2018
- HA
- Two physical machines running Windows 2016 Hyper-V. pfSense as guest-vm in respectively machine.
- Machine #1: pfSense #1 master, Windows AD #1
- Machine #2: pfSense #2 backup, Windows AD #2
Main Office:
- Windows AD controllers with DNS, domain is host.sub.domain.tld
- HA pfSense, working great. Fail-over works as intended, client doesn't notice anything when Machine #1 and/or pfSense #1 goes down.
- pfsense DNS are set to external DNSs (1.1.1.1 ...)
- OpenVPN server peer-to-peer.
- DHCP is handled by the domain controllers. DNS given out is pointing to the AD-DNS #1 and #2.
- Domain override of the internal DNS for sub.domain.tld with destination #1 of the AD-DNS (it's here I would like to be able to provide an option to make it go for AD-DNS #2 if #1 not available)
Name resolving here is not a problem for the client as they got the AD-DNS #1 and #2. The problem is pfsense own resolving of internal address when AD-DNS #1 is not answering.
Branch Office:
- Single pfSense
- OpenVPN client peer-to-peer (which reconnect beautifully after a short timeout when HA master goes down)
- DHCP give out DNS to this pfense
- pfsense DNS are set to external DNSs
- Domain override of the internal DNS for sub.domain.tld with destination #1 of the AD-DNS (it's here I would like to be able to provide an option to make it go for AD-DNS #2 if #1 not available)
If AD#1 is not available at the same time as the HA is on the backup (scenario when Machine #1 is down) I get no name resolving as I've found no way to make the Branch Office pfsense to ask AD-DNS #2 in an Override.
Phju, that allot of explaining in an effort to make this understandable.
Need some guidance and/or suggestion how to make this work, if possible. Maybe I'm looking at this the wrong way?
Brgs,
-
Hi,
what about setting the Branch Office pfSense' DNS to the LAN VIP of the Main Office site? That way you always ask the current "master" and therefore should get an answer of a working DNS as the main office pfSense boxes have both DNSes configured, it should get an answer of AD-DNS#2.
Edit: almost forgot! You can add another overwrite for the exact same domain/Host and add another IP that way the DNS forwarder on the branch office will ask both of them. So you should definitly get an answer from one of them.
Greets
-
Hi and thanks for answering.
I do hope that I understand what to say here.
And setting the branch office pfsense DNS to point to a DNS on the other side of the VPN is problematic if the main office is offline, then they get no working DNS at all.
That it is a solution to get the name resolution work, either giving out the AD DNSs to the client at the branch office or set the DNS in the branch office pfsense to the AD DNSs. But then they need that peer-to-peer to always being connected.pfSense domain override can only point to one IP as I understand it. Host overrides though can be multiples, but then you get some round-robin behavior so you end up not knowing which IP that is returned.
The goal here is to make pfSense ask more than one DNS for a domain override as I see it.
Maybe, an idea right now - not tested, something using a HA NAT rule that don't sync, unique for each pfsense, that redirect incoming traffic for DNS to them selves or specific AD DNS.
-
@iorx said in DNS resolve for internal hosts in HA and peer-to-peer OpenVPN:
pfSense domain override can only point to one IP as I understand it. Host overrides though can be multiples, but then you get some round-robin behavior so you end up not knowing which IP that is returned.
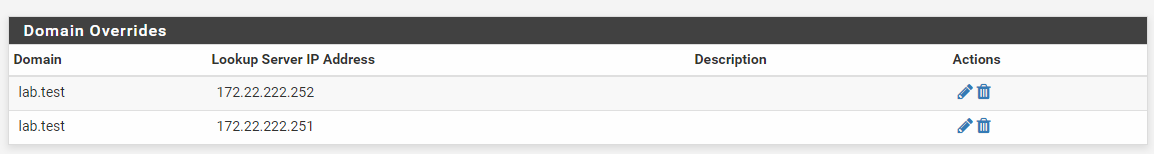
As you see in the screenshot (even if it's from the DNS resolver), you can add two entries for domain overrides without problems. I tested it and if e.g. 252 is down, 251 will supply the address and vice versa.
So just add both AD-DNS servers to your local DNS domain overrides and you should be good. :)
-
Hi
I though I read up thoroughly on the subject and somewhere I got to have picked up the wrongfull info that domain overrides couldn't be done like that. That one stuck so I even didn't try it, such a brain-fart
 .
.Now I successfully have created a a double domain override as you showed, but got to wait until to night to test it as the customers system are active for the moment. Going to bring machine#1 down and check the functionality from the branch office.
I'll report back my findings and if it works as intended.
Thanks allot for being the crutch on this matter.
Edit:
Also created double reverse lookup entries in domain overrides, works like a charm. 25.168.192.in-addr.arpa pointing at the AD-DNSs.
Will test these too in a HA fail test.Brgs,
-
@iorx said in DNS resolve for internal hosts in HA and peer-to-peer OpenVPN:
Thanks allot for being the crutch on this matter.
Glad to be of service

-
Hello -
I will add that I would not run Resolver on the firewall at all in that case. I would:
Set OpenVPN to give the clients the AD addresses for DNS
Set both pfSense cluster nodes to use the AD addresses for DNS (System > General)
Check the Disable DNS Forwarder box in System > General so the firewall does not try to use itself to resolve names.
Disable DNS Resolver on the cluster nodes.While that solution looks good, there is no pressing requirement for a DNS cache to be running on the firewall cluster at all.
This way everyone is always getting the answers AD thinks it should be getting for everything.
-
Hi!
Thanks for contributing. There are no road-warriors, connecting users, involved here only peer-to-peer site connections.
But you're right, giving road-warriors the AD-DNSs is a good working solution.The DNS on pfSense is needed in my case. A couple of guest (VLANs) networks use that exclusively, don't and won't use the AD-DNSs for that

Brgs,
-
They are still getting forwarded to AD for the AD domain unless you have done custom ACLs.
-
Yes you're right, it's a bit of security by obscurity in that case. Users on guestlans need to know which suffix to probe in that case, host.sub.domain.tldm.
I'll see if I find a cleaver way to prevent that. I planing to implement some kind of filtering also, but I haven't come around checking how stable pfblocker is in a HA environment yet. -
Success!
Tried it out live now.
Shutdown machine #1. Branch Office lost its connection to the Main Office for about 10 seconds. This is OpenVPN reconnecting.After OpenVPN peer-to-peer reconnected.
Resolving from AD DNS works! TIL: So, multiple domain overrides is the way to go for internal name resolution in this scenario with AD DNSs.Goal achieved with HA, AD DNS and OpenVPN peer-to-peer.
- Branch Office is not a sitting duck when Main Office is not available. Normal DNS function maintained.
- Branch Office AD DNSs reach-ability is kept when HA is failed over.
Kudos to all!
Brgs,