DNS Resolver (unbound) with TLS, still utilizing 53 outbound
-
All:
I've configured my pfSense installation to utilize TLS to Cloudfare DNS and Quad 9. Double checked the configuration many times. In Status> DNS Resolver everything looks fine. Three DNS servers running on 853. Now here's the problem. Running packet capture on external interface filtering on 53, and run a dig <domain.name> on a client; I see UDP/53 transiting ext int to 1.1.1.1. Now if I filter on 853; I see ext int passing TCP/853 to Quad 1. That's expected. Since I have it configured for TLS, why am I seeing 53 traffic leaving pfSense and headed to Quad 1 on the external interface?
-
Its most likely pfSense itself. Nothing to worry about. Do you have a NAT rule to redirect DNS traffic back to the gateway? That would catch naughty clients who set some other server. What I have done is this. Turn off that TLS option. Add the custom lines to unbound to forward queries to the servers of your choosing over port 853. Set the DNS server in the general setup to 127.0.0.1. Using packet capture I see zero port 53 traffic on the WAN interface. Details on the exact rules to use and the custom config lines for unbound can be found with a few simple searches in the forum and the online documentation.
-
Like this:
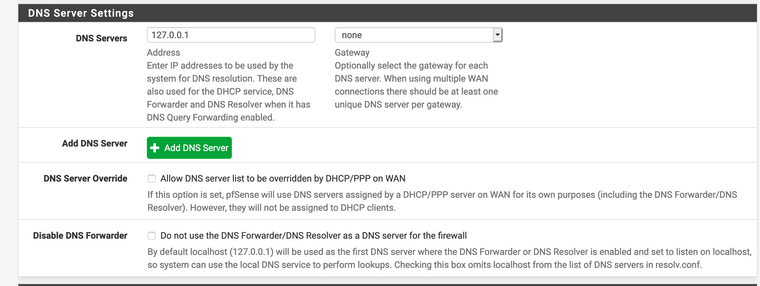
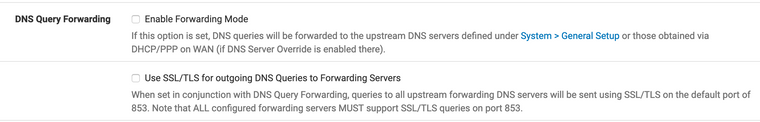
I use cloudflare, it looks like this:
server:
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 1.1.1.1@853
forward-addr: 1.0.0.1@853
forward-addr: 2606:4700:4700::1111@853
forward-addr: 2606:4700:4700::1001@853and lastly:
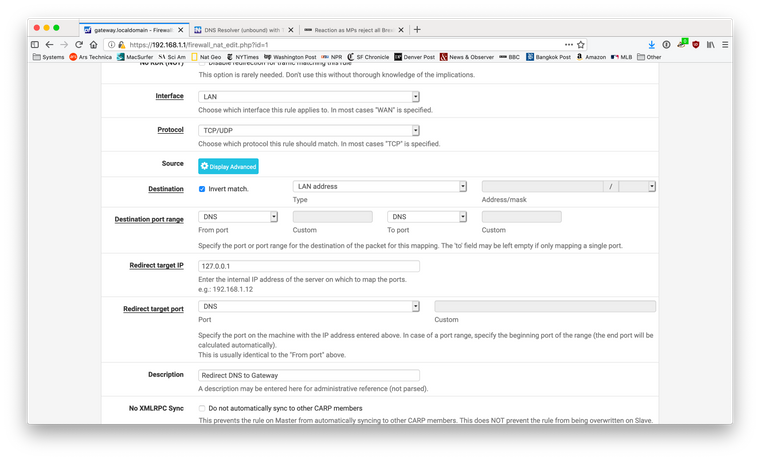
-
JWJ: Thanks so much. This works like I wanted. Not sounding like I am crying, but after these changes, I had to delete ntopng, it didn't want to play nicely anymore. Miss the Status>DNS Resolv> Cache TTL/RTT stats, but realize I am not running a resolver locally anymore. Cant believe I didn't see more people complaining about the "posted how to's" for CF>TLS on pfSense still passing clear text udp requests out the WAN. Don't people verify things after making changes? Trust but verify. Again, thank you for this solution.
-
You could go back to running unbound as a resolver and then send all the queries to the authoritative servers out over a VPN. That involves a few more moving parts and maybe the additional cost of a VPN service. That should give you the same outcome as DNS over TLS in terms of privacy. Of course you would have to balance how much you trust your ISP vs some VPN provider. I would ask myself if this is much to do about nothing given how many other ways you're being surveilled. Everyone's needs and concerned are different. I'm not a dissident in some authoritarian place, I will do easy things to stop surveillance capitalism when the opportunity presents itself.