DMZ rules
-
Hello,
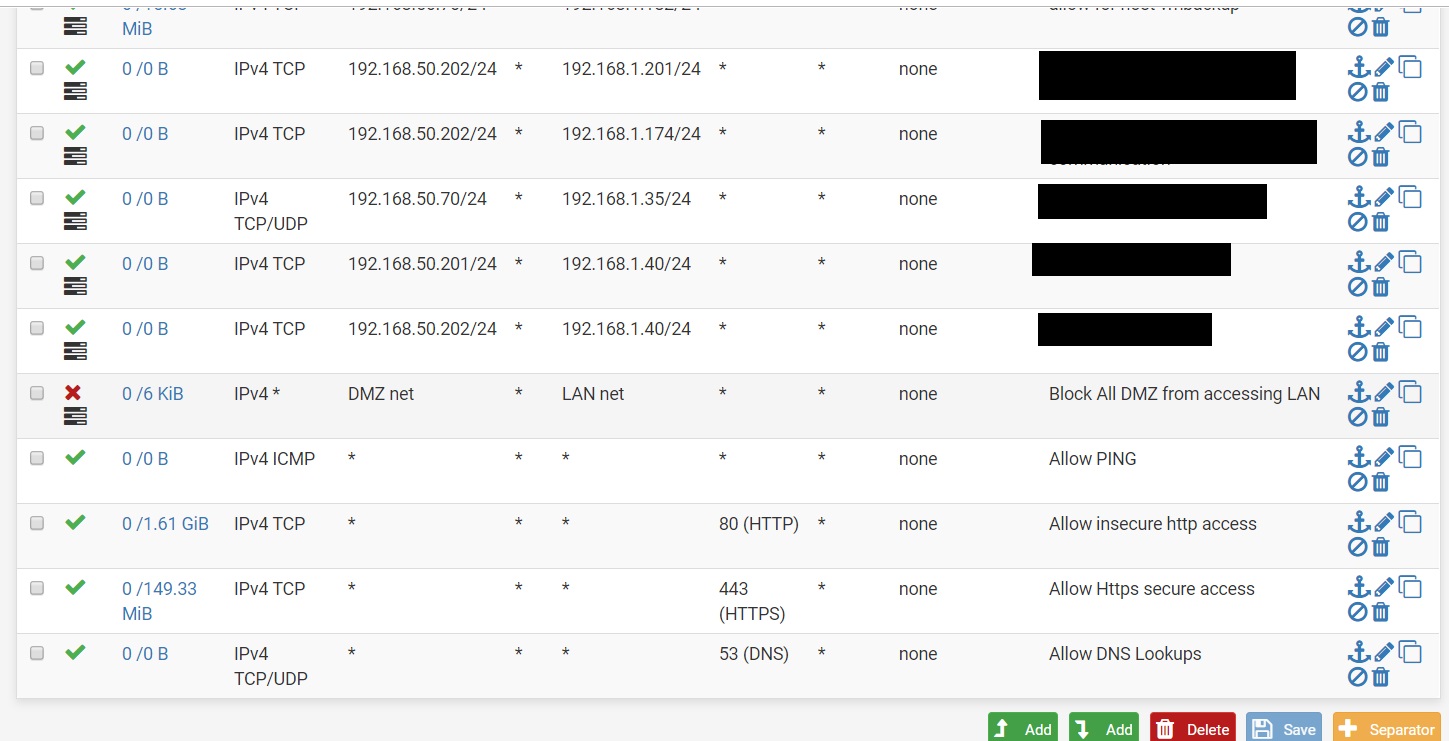
Question. Is our DMZ setup for rules appropriate? Please refer to attached image.
Thank you.
-
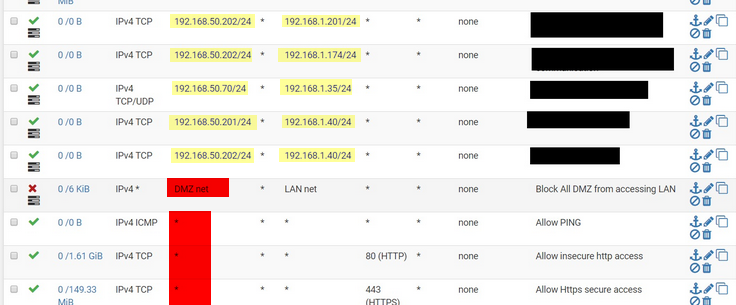
The yellow marked IPs are no network addresses. So they could not be used with a subnet mask.
If you want to apply that rules to subnets enter the correct network address.In a block rule you should use the "any" as source.
In pass rules on the other hand, "DMZ net" should be used instead of "any". -
I agree, makes no sense to define point to point rules (first 5) and then throw /24 behind it so the whole network can talk to each other. Also those rules are TCP only so if you are that specific, why not also include the ports instead of "all"?
I'd also sort the kind of infrastructure rules on top (allow DNS, Ping, NTP and 80/443 for updates or such likes) and make them more specific so it won't interfere with other rules. Normally if that's your DMZ I see no reason why my DMZ hosts should talk to any DNS out there if I have a resolver/forwarder with caching running myself. Same for NTP.
I would consider creating a RFC1918 Alias with all private IP space and use that instead of LAN net as a target so to reject all traffic from DMZ to other internal networks. If you specifically need a single IP or subnet, add that with a pass above the reject. So you can't accidentally introduce a new subnet on your firewall and open it up to network segments that it shouldn't be visible.
That are the basic thing's I'd consider.