Additional Router Behind pfSense
-
Getting my feet wet with pfsense running on a VM. My primary goals are:
- IPS via Snort/Suricata with 1Gbps symmetrical performance.
- DMZ network for running public services.
- Private network sitting behind additional firewall/router (Internet -> pfSense -> DMZ Network -> firewall/router -> Internal Network)
- (Optionally), 100Mbps+ IPSec VPN
So far, I've got everything physically connected with Snort running and web access functional. However, I haven't yet moved my VMs into a dedicated VM network but I am trying to get outside access into them working (80/443/other) but can't seem to get it. Physical topology is modem>pfsenseIN>pfsenseOut>Internal router/firewall WAN port. Logically, pfsenseOut is the LAN interface in pfsense, 10.0.0.0/30 network with 10.0.0.1 assigned to the interface. Then on the internal router/firewall, I've got a static WAN configuration with an IP of 10.0.0.2. and then DHCP network on it's LAN interface as 192.168.1.0/24.
I've created a NAT rule for HTTP.
- Src: Any
- Dest: WAN Address
- Dest Port: HTTP
- Redirect IP: 10.0.0.2
- Redirect Port: HTTP
- Filter Rule Association: Create new associated filter rule
Port forwarding rules already exist on the internal firewall/router to redirect any requests to a specific IP on port 80. Unfortunately, I am unable to hit the HTTP endpoint from outside. I'm assuming there's some double-NAT'ing issues going on but I am not really sure. Any help would be greatly appreciated.
Alternatively, am I "over-engineering" this by creating a physical boundary between the DMZ and internal networks? Would I be just as well off having a single device handle routing for both networks? I was looking at it from a "defense in depth" perspective.
-
Is that second firewall/router NATing or just routing? It reads like it's NATing also which just makes things more complex.
I would say you probably don't need that second device there if you only have one subnet behind it.
192.168.1.X is the default pfSense LAN subnet. Are you using that in two places?
Steve
-
I'm also wondering about NAT. Do you need it? I run VirtualBox here and it can be configured to use either NAT or bridging interfaces. I use bridging, so that the VM is on the same network as the host computer. It's also the only way IPv6 works with it.
-
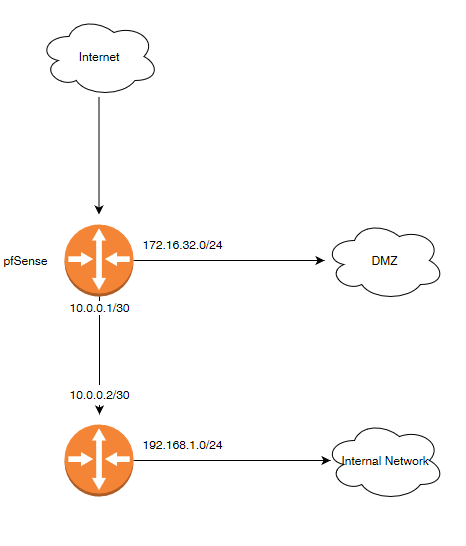
This is basically what I am looking at doing.
The internal router also NAT'ing, which is why I am thinking its a double NAT'ing issue, though I really don't know for sure. Would I bridge the WAN/LAN interfaces to make a transparent firewall and then leave the DMZ interface? Would that still allow routing to the 172 network? If I bridge the interfaces does IPS still function properly?
-
Why do you need a second router? PfSense is quite capable of handling both the DMZ and internal network.
I have similar here with my main network and a test network.
-
Yeah, the second router seems to be doing nothing useful here unless it has other functionality we are not seeing.
If you really want to keep it though I would disable NAT on the second router, make it route only. YOu would need to add a static route to 192.168.1.X via 10.0.0.2 in pfSense. That should add the required outbound NAT rule for 192.168.1.X as long as you have outbound nat in auto mode.
Steve
-
The thought was more of a "defense in depth". If something gets through pfsense, the second firewall may catch it (or vice versa).
I will take another crack at it tonight by shutting off NAT on the internal firewall.
Thanks for the timely responses all.