Add New Interface for all my IoT devices and DMZ - no Internet access
-
Hello,
I want to add 2 news interfaces DMZ and IoT.
I've already added it but infortunatelly I can't have access to internet from this new's interfaces, neither from the LAN to this interfaces. don't know what to do now.
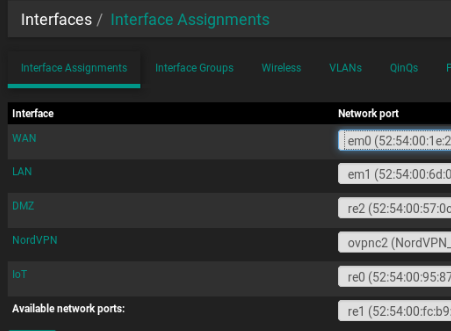
can you please help me?
Thank you
-
There are several things to look for, some of which are already in place:
-
Are there firewall rules in place allowing outbound traffic on the IoT and DMZ interface? Looks like it.
-
Are the hosts configured correctly?
-
Using PFsense as the default gateway?
-
Using the correct mask?
-
Have an IP in the correct subnet?
-
-
Is there a downstream L3 switch on the network?
-
Are you using Automatic outbound NAT or Manual Outbound NAT?
- If using Manual Outbound NAT, did you add NATs for the two new subnets?
-
Are you using the Resolver with ACL's configured?
- If so, did you configure an ACL to allow queries from the two new subnets?
neither from the LAN to this interfaces. don't know what to do now.
I believe this is working as intended as you have blocked the return traffic.
You basically need to isolate whether there's actually a networking issue getting to the internet or if you're just having problems resolving DNS, then steer your troubleshooting accordingly.
-
-
https://doc.pfsense.org/index.php/Connectivity_Troubleshooting
-
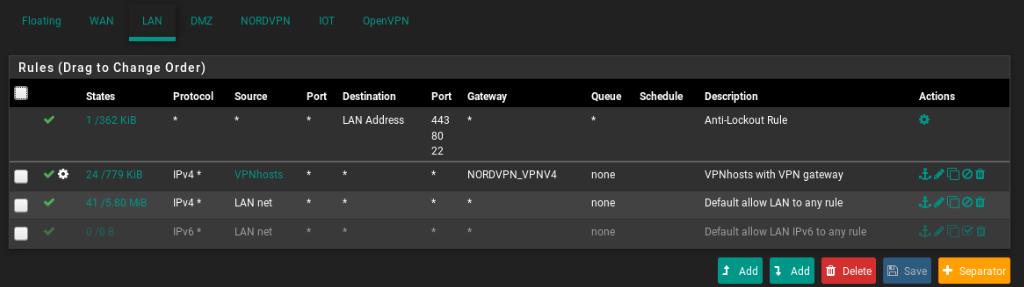
It doesn't work from LAN because you're policy routing all that traffic via OpenVPN. You need a rule above that to pass traffic from LANnet to IoT or DMZ.
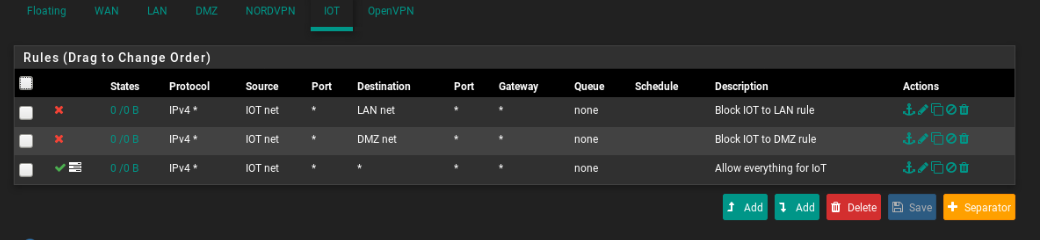
There are no states/traffic showing on the pass rules on IoT or DMZ so nothing is trying to get out. Are devices on that interface even configured correctly?
Steve
-
@stephenw10 Can you help me creating that rule?
not all my devices have the openvpn gateway, but I want to be able (from the devices with openvpn gateway) to access the others interfaces.
Concerning the Nat outbound (Thank you for your help @marvosa ) it was on manual (tutorial to add nordvpn to pfsense, tells to pout it on manual) I put it on hybrid and now the devices without openvpn as gateway can "see" the others interfaces.
Thanks for your help
-
It just needs to be a pass rule from source LANnet to destibation IoTnet and it needs to be above the "VPN hosts with VPN gateway" rule. If those "VPN hosts" need to reach the IoT subnet.
Steve
-
@stephenw10 Perfect :)
is this correct?
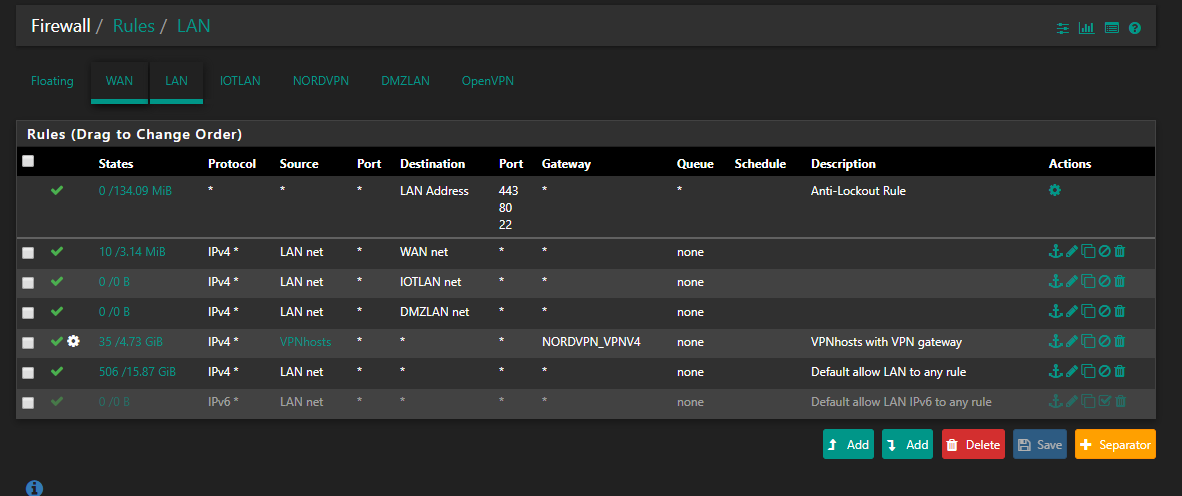
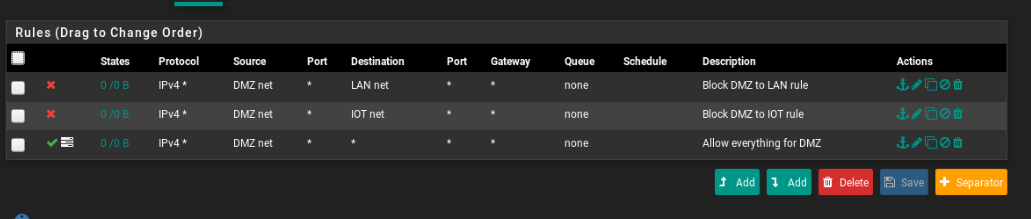
Concerning the DMZ and iot interface, for security reasons do you think I need more then this rules??
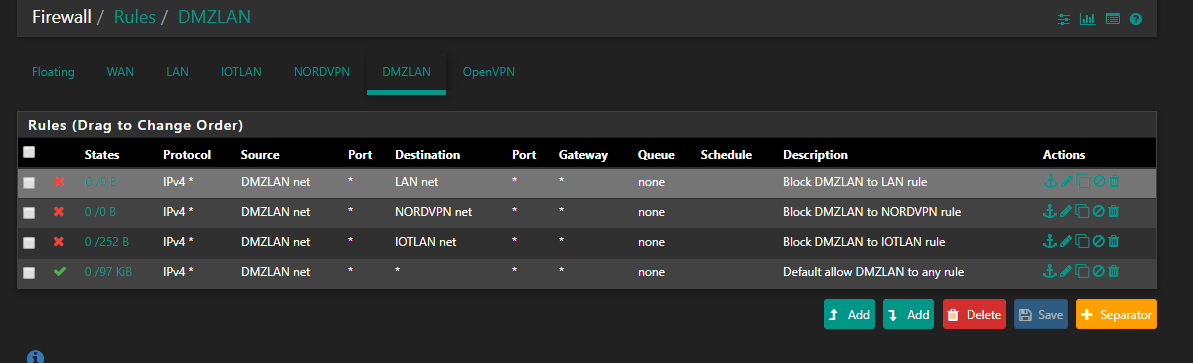
I tried to block all and only allow access to internet, but I dind't manage to do it.
In the iot interface I want to create a rule to block some IP's to access internet too (only local, subnet access), can't find how to do it. Can you help me too?
Thanks a lot for your help
-
Unless you have other devices in the actual WAN subnet you need to reach you probably don't want that LANnet to WANnet rule in LAN.
If you want to allow access to only the internet from DMZ I would include pass rules for DMZnet to DMZ address for UDP port 53 and 123 to allow clients DNS and NTP access. Then a deny rule for destination 'This Firewall'.
That would prevent DMZ clients accessing the pfSense webgui and other services using the WAN IP.
Steve