OpenVPN installed, iOS client connects, but no internet or local resources
-
Hi,
I'm not a firewall expert. Had another solution implemented, it worked well, but I upgraded internet speed and that last solution only recognized one of my intel pro1000 gigabit NICs.
Installed pfSense and was happy that it recognized both.
I went through the wizard, got OpenVPN configured, exported ovpn for client, imported ovpn in iOS, connected successfully.
But when connected from iOS to the OpenVPN:
I can't access internet.
I can't access local Plex server.However, I can actually see and login to pfSense at 192.168.1.1 when logged into VPN from cellular network on iOS.
What can I give you for you to be able to help me with this?
Thank you,
Dajo -
here's some things I found.
I connected again from iOS and got some logs:StatusSystem LogsOpenVPN:
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_GUI_VER=net.openvpn.connect.ios_3.0.2-894
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_VER=3.2
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_PLAT=ios
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_NCP=2
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_TCPNL=1
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 peer info: IV_PROTO=2
Apr 14 21:22:48 openvpn user 'dajo' authenticated
Apr 14 21:22:48 openvpn 49115 174.236.144.58:2017 [dajo] Peer Connection Initiated with [AF_INET]174.236.144.58:2017
Apr 14 21:22:48 openvpn 49115 dajo/174.236.144.58:2017 MULTI_sva: pool returned IPv4=192.168.2.2, IPv6=(Not enabled) -
@dajokahn said in OpenVPN installed, iOS client connects, but no internet or local resources:
I connected again from iOS and got some logs: ...
When using an iPhone, using the OpenVPN app, I have the same logs.
You could also "find" the log on the client, although it would probably not show the issue.What do you have here : Firewall => Rules => OpenVPN ?
-
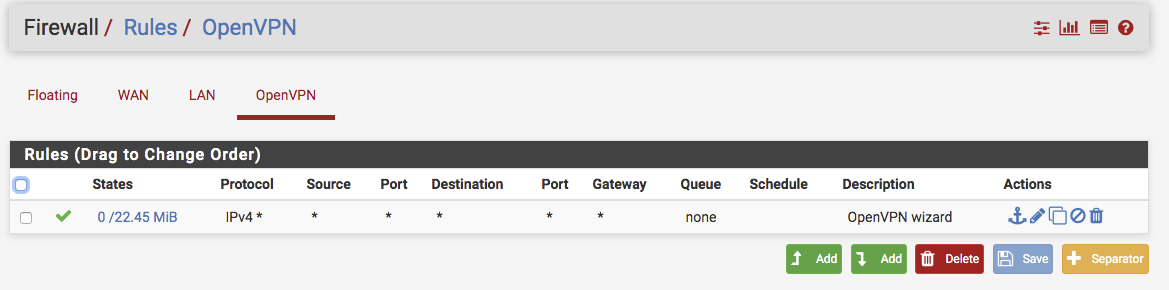
thank you!
-
Firewall rule looks fine.
Your OpenVPN setttings ?
Check also your settings with the official OpenVPN videos (Youtube => Netgate).
-
on your iphone you should see way more logs than that - like your routes being added, etc.. if no routes add then no your no going to go anywhere.
example just connected with my iphone XR running the same openvpn connect app
2019-04-15 07:33:40 Contacting [64.53.snipped]:1194/UDP via UDP 2019-04-15 07:33:40 EVENT: WAIT 2019-04-15 07:33:40 Connecting to [64.53.snipped]:1194 (64.53.snipped) via UDPv4 2019-04-15 07:33:40 EVENT: CONNECTING 2019-04-15 07:33:40 Tunnel Options:V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,cipher AES-128-CBC,auth SHA256,keysize 128,key-method 2,tls-client 2019-04-15 07:33:40 Creds: UsernameEmpty/PasswordEmpty 2019-04-15 07:33:40 Peer Info: IV_GUI_VER=net.openvpn.connect.ios 3.0.2-894 IV_VER=3.2 IV_PLAT=ios IV_NCP=2 IV_TCPNL=1 IV_PROTO=2 IV_AUTO_SESS=1 2019-04-15 07:33:40 VERIFY OK : depth=1 cert. version : 3 serial number : 00 issuer name : C=US, ST=IL, L=Schaumburg, O=Home, emailAddress=snipped, CN=openvpn subject name : C=US, ST=IL, L=Schaumburg, O=Home, emailAddress=snipped, CN=openvpn issued on : 2015-01-10 14:15:11 expires on : 2025-01-07 14:15:11 signed using : RSA with SHA-256 RSA key size : 2048 bits basic constraints : CA=true 2019-04-15 07:33:40 VERIFY OK : depth=0 cert. version : 3 serial number : 01 issuer name : C=US, ST=IL, L=Schaumburg, O=Home, emailAddress=snipped, CN=openvpn subject name : C=US, ST=IL, L=Schaumburg, O=Home, emailAddress=snipped, CN=pfsenseopenvpn issued on : 2015-01-10 14:15:12 expires on : 2025-01-07 14:15:12 signed using : RSA with SHA-256 RSA key size : 2048 bits basic constraints : CA=false cert. type : SSL Server key usage : Digital Signature, Key Encipherment ext key usage : TLS Web Server Authentication 2019-04-15 07:33:40 SSL Handshake: TLSv1.2/TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384 2019-04-15 07:33:40 Session is ACTIVE 2019-04-15 07:33:40 EVENT: GET_CONFIG 2019-04-15 07:33:40 Sending PUSH_REQUEST to server... 2019-04-15 07:33:40 OPTIONS: 0 [route] [192.168.9.0] [255.255.255.0] 1 [route] [192.168.2.0] [255.255.255.0] 2 [route] [192.168.3.0] [255.255.255.0] 3 [dhcp-option] [DNS] [192.168.9.253] 4 [route-gateway] [10.0.200.1] 5 [topology] [subnet] 6 [ping] [10] 7 [ping-restart] [60] 8 [ifconfig] [10.0.200.2] [255.255.255.0] 9 [peer-id] [0] 10 [cipher] [AES-128-GCM] 2019-04-15 07:33:40 PROTOCOL OPTIONS: cipher: AES-128-GCM digest: SHA256 compress: NONE peer ID: 0 2019-04-15 07:33:40 EVENT: ASSIGN_IP 2019-04-15 07:33:40 NIP: preparing TUN network settings 2019-04-15 07:33:40 NIP: init TUN network settings with endpoint: 64.53.snipped 2019-04-15 07:33:40 NIP: adding IPv4 address to network settings 10.0.200.2/255.255.255.0 2019-04-15 07:33:40 NIP: adding (included) IPv4 route 10.0.200.0/24 2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.9.0/24 2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.2.0/24 2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.3.0/24 2019-04-15 07:33:40 NIP: adding DNS 192.168.9.253 2019-04-15 07:33:40 NIP: adding match domain ALL 2019-04-15 07:33:40 NIP: adding DNS specific routes: 2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.9.253/32 2019-04-15 07:33:40 Connected via NetworkExtensionTUN 2019-04-15 07:33:40 EVENT: CONNECTED 64.53.snipped:1194 (64.53.snipped) via /UDPv4 on NetworkExtensionTUN/10.0.200.2/ gw=[/] 2019-04-15 07:33:41 RECONNECT TEST: Internet:ReachableViaWiFi/-R t------Right from the app you can email your logs to yourself... Then post the info here, and snipout any personal info like public IP, like I did above.
-
Ah, ok, I understand now :
@johnpoz said in OpenVPN installed, iOS client connects, but no internet or local resources:2019-04-15 07:33:40 NIP: adding (included) IPv4 route 10.0.200.0/24
2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.9.0/24
2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.2.0/24
2019-04-15 07:33:40 NIP: adding (included) IPv4 route 192.168.3.0/24I didn't have all these "adding (included) IPv4 route" for all my LAN's. I thought so : something is missing.
I have :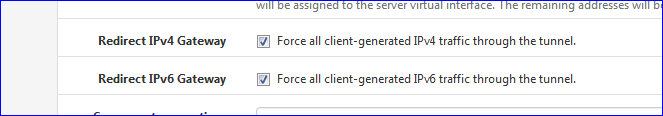
Which allows my clients to connect to "everything".
-
yeah you can do that if you want.. I don't - but he doesn't show that either in his log..
Also looks like he is using 192.168.2 as his tunnel - if that steps on his local network where he is connecting from - then also another bad day sort of thing.
-
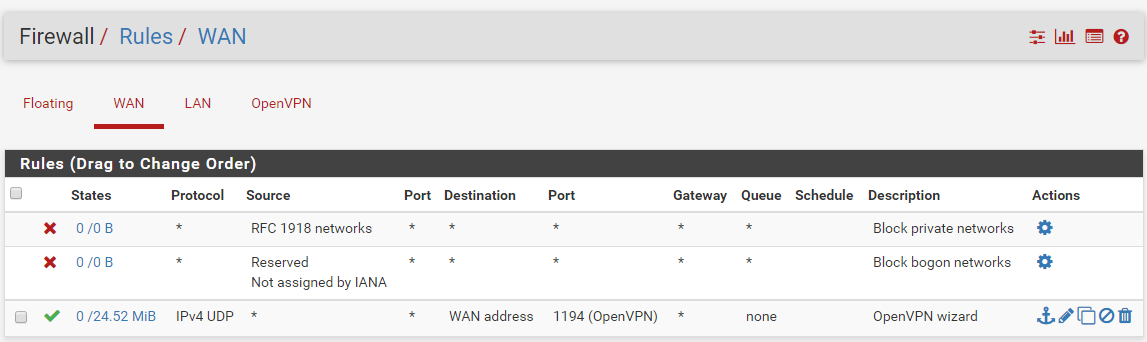
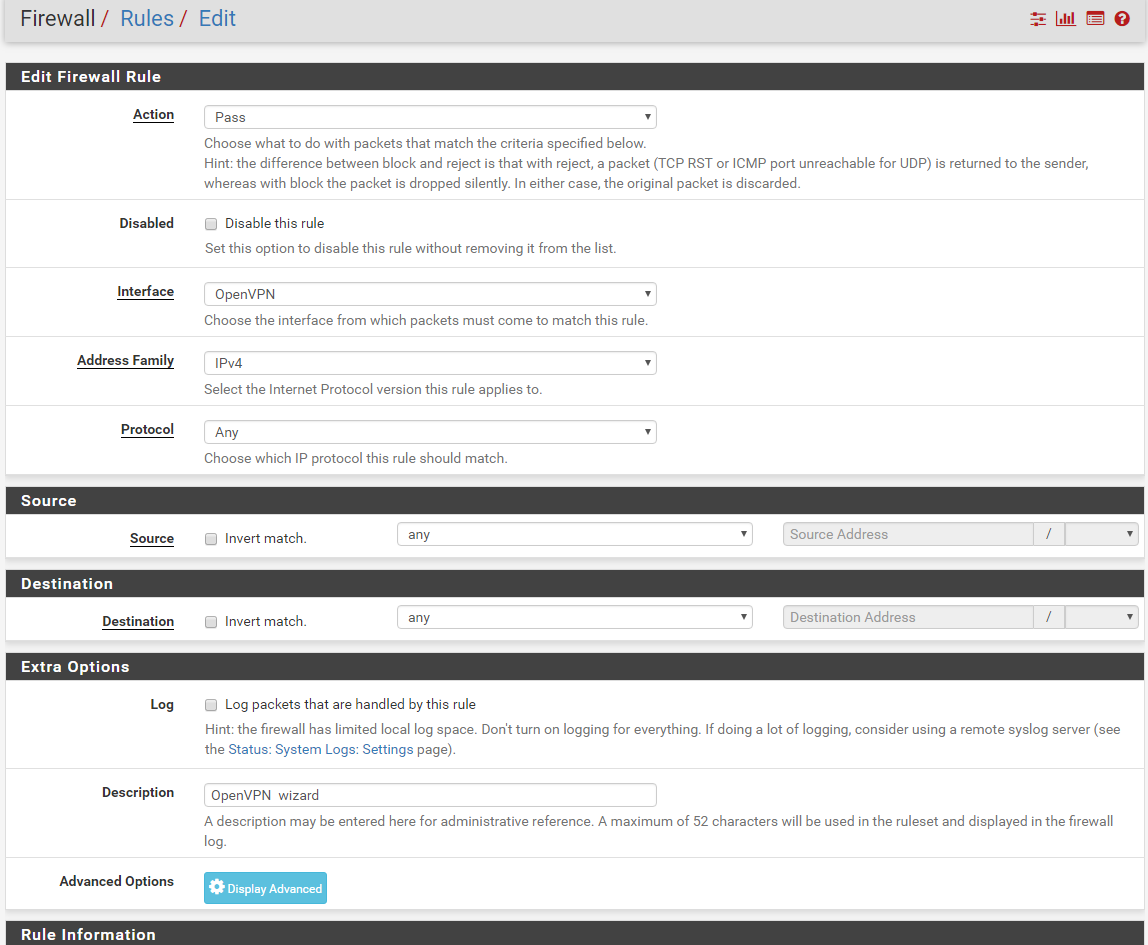
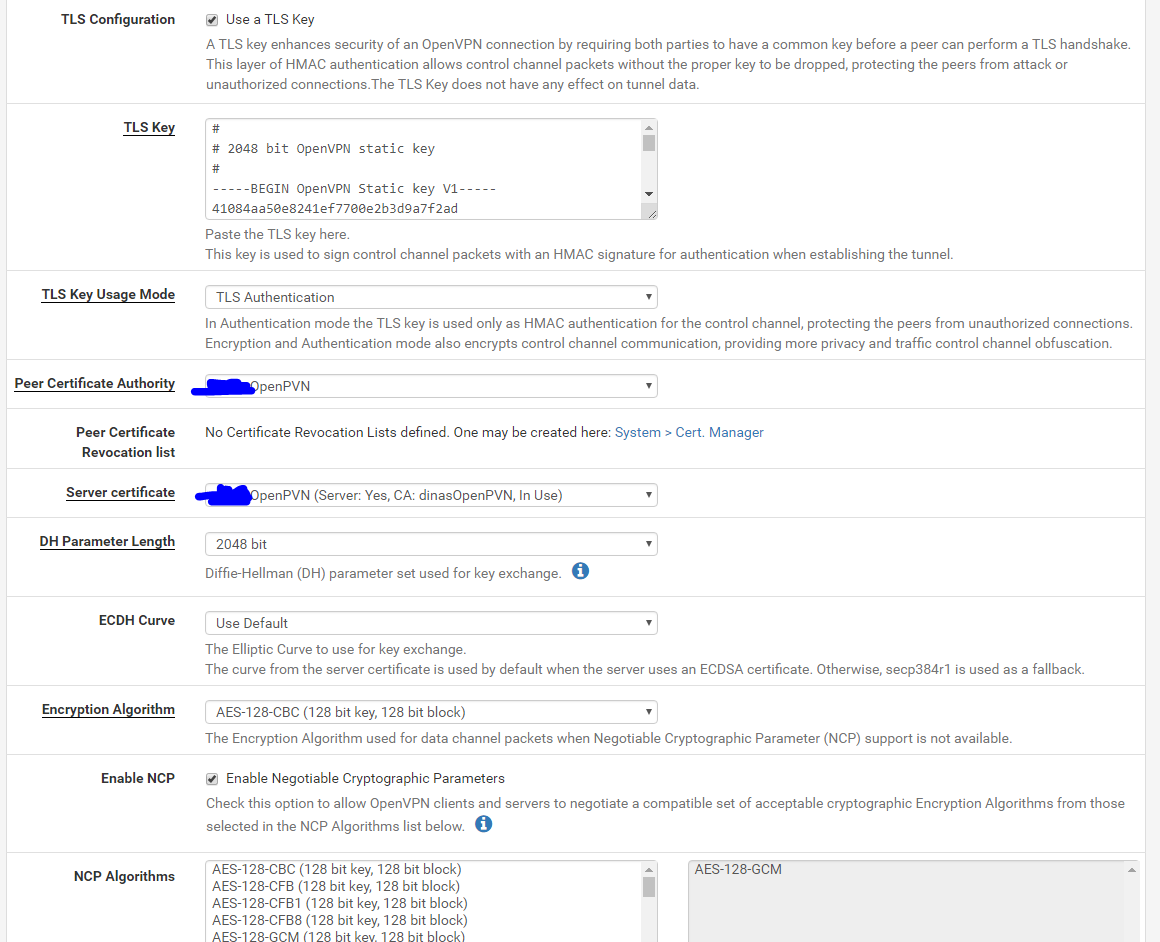
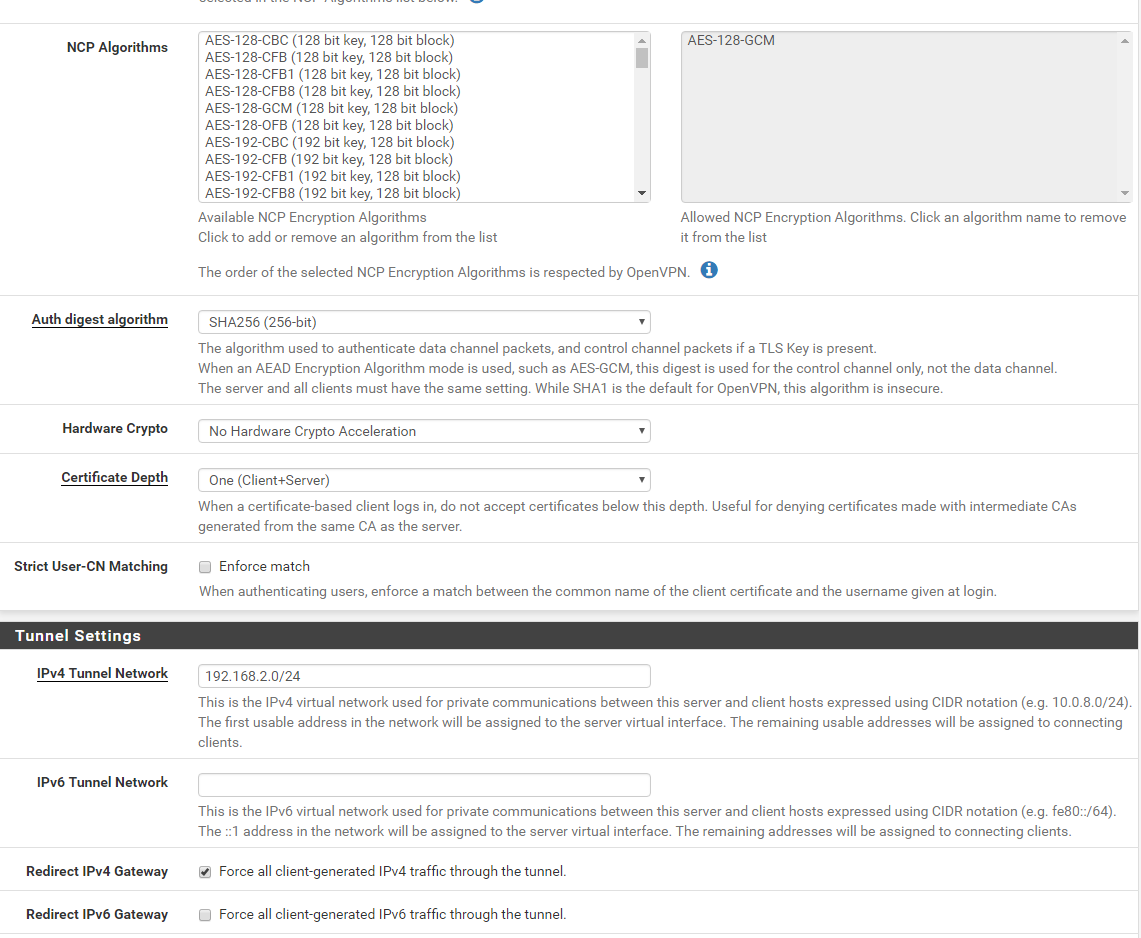
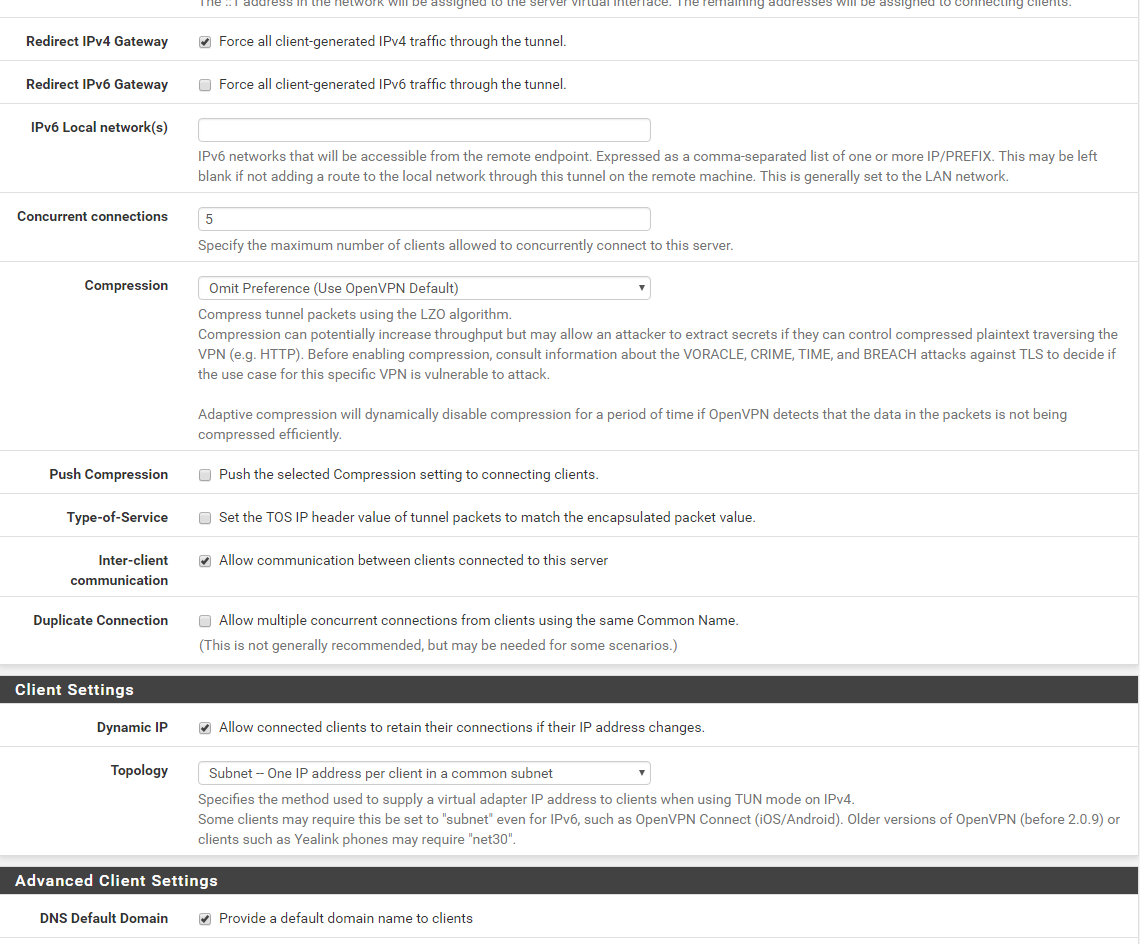
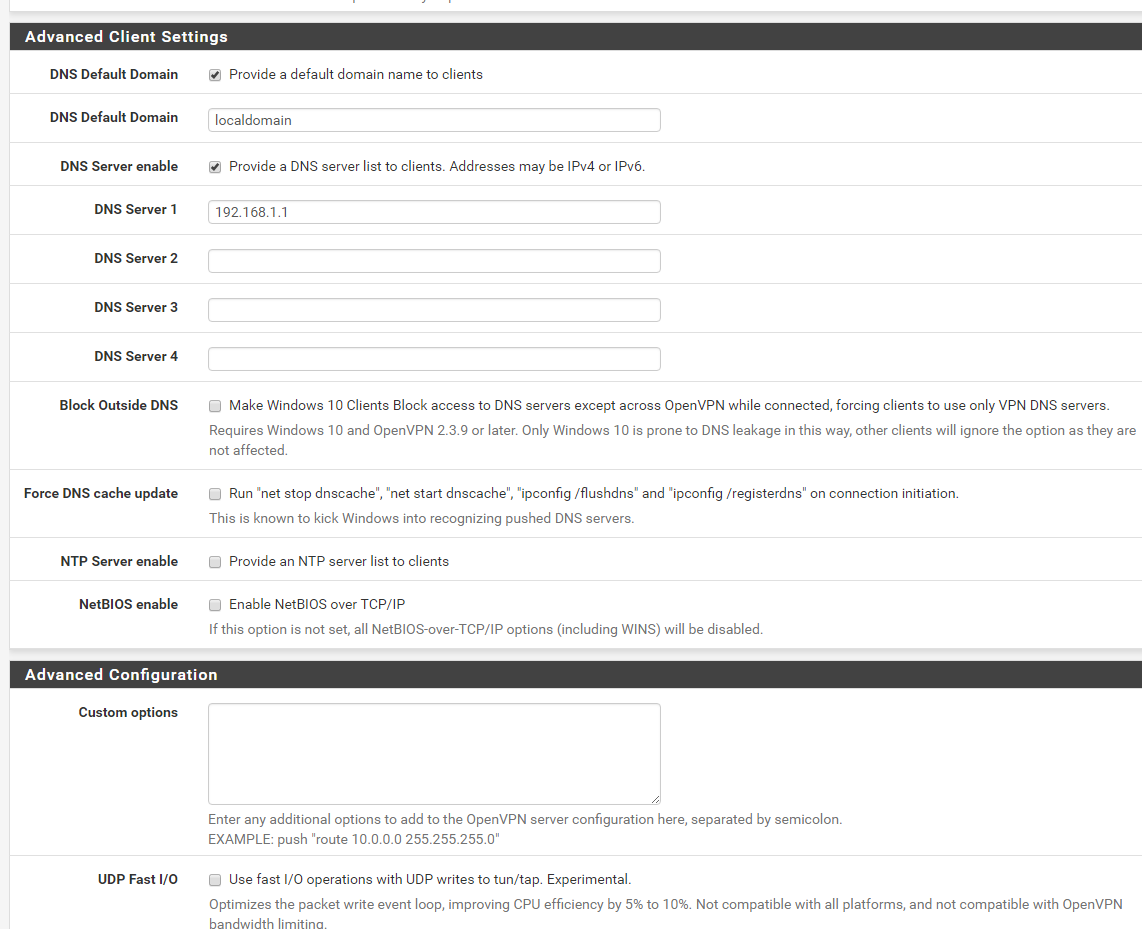
-
ok, guys, besides screenshots above and iOS openvpn connect app logs, please let me know if there i anything else I need to provide.
2019-11-15 20:11:15 1
2019-11-15 20:11:15 ----- OpenVPN Start -----
OpenVPN core 3.2 ios arm64 64-bit PT_PROXY built on Oct 3 2018 06:35:042019-11-15 20:11:15 Frame=512/2048/512 mssfix-ctrl=1250
2019-11-15 20:11:15 UNUSED OPTIONS
0 [persist-tun]
1 [persist-key]
4 [tls-client]
7 [lport] [0]
8 [verify-x509-name] [testOpenPVN] [name]2019-11-15 20:11:15 EVENT: RESOLVE
2019-11-15 20:11:15 Contacting [75.76.77.78]:1194/UDP via UDP
2019-11-15 20:11:15 EVENT: WAIT
2019-11-15 20:11:15 Connecting to [75.76.77.78]:1194 (75.76.77.78) via UDPv4
2019-11-15 20:11:15 EVENT: CONNECTING
2019-11-15 20:11:15 Tunnel Options:V4,dev-type tun,link-mtu 1569,tun-mtu 1500,proto UDPv4,keydir 1,cipher AES-128-CBC,auth SHA256,keysize 128,tls-auth,key-method 2,tls-client
2019-11-15 20:11:15 Creds: Username/Password
2019-11-15 20:11:15 Peer Info:
IV_GUI_VER=net.openvpn.connect.ios 3.0.2-894
IV_VER=3.2
IV_PLAT=ios
IV_NCP=2
IV_TCPNL=1
IV_PROTO=22019-11-15 20:11:16 VERIFY OK : depth=0
cert. version : 3
serial number : 01
issuer name : CN=testOpenPVN, C=US, ST=TN, L=City, O=test
subject name : CN=testOpenPVN, C=US, ST=TN, L=City, O=test
issued on : 2019-04-14 20:45:31
expires on : 2029-04-11 20:45:31
signed using : RSA with SHA-256
RSA key size : 4096 bits
basic constraints : CA=false
subject alt name : testOpenPVN
cert. type : SSL Server
key usage : Digital Signature, Key Encipherment
ext key usage : TLS Web Server Authentication, ???2019-11-15 20:11:17 SSL Handshake: TLSv1.2/TLS-ECDHE-RSA-WITH-AES-256-GCM-SHA384
2019-11-15 20:11:17 Session is ACTIVE
2019-11-15 20:11:17 EVENT: GET_CONFIG
2019-11-15 20:11:17 Sending PUSH_REQUEST to server...
2019-11-15 20:11:17 OPTIONS:
0 [dhcp-option] [DOMAIN] [localdomain]
1 [dhcp-option] [DNS] [192.168.1.1]
2 [redirect-gateway] [def1]
3 [route-gateway] [192.168.2.1]
4 [topology] [subnet]
5 [ping] [10]
6 [ping-restart] [60]
7 [ifconfig] [192.168.2.2] [255.255.255.0]
8 [peer-id] [0]
9 [cipher] [AES-128-GCM]2019-11-15 20:11:17 PROTOCOL OPTIONS:
cipher: AES-128-GCM
digest: SHA256
compress: NONE
peer ID: 02019-11-15 20:11:17 EVENT: ASSIGN_IP
2019-11-15 20:11:17 NIP: preparing TUN network settings
2019-11-15 20:11:17 NIP: init TUN network settings with endpoint: 75.76.77.78
2019-11-15 20:11:17 NIP: adding IPv4 address to network settings 192.168.2.2/255.255.255.0
2019-11-15 20:11:17 NIP: adding (included) IPv4 route 192.168.2.0/24
2019-11-15 20:11:17 NIP: redirecting all IPv4 traffic to TUN interface
2019-11-15 20:11:17 NIP: adding match domain localdomain
2019-11-15 20:11:17 NIP: adding DNS 192.168.1.1
2019-11-15 20:11:17 Connected via NetworkExtensionTUN
2019-11-15 20:11:17 EVENT: CONNECTED dajo@75.76.77.78:1194 (75.76.77.78) via /UDPv4 on NetworkExtensionTUN/192.168.2.2/ gw=[/]
-
I compared your settings with mine.
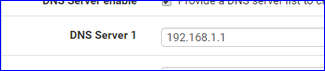
I have 192.168.2.1 as a DNS for VPN clients - not the LAN based DNS.
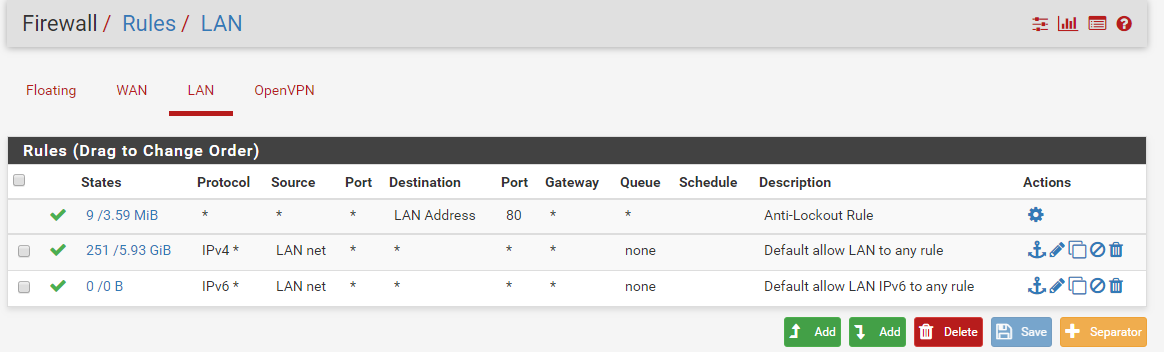
Your LAN rules : remove (temporality) the source "LAN Net" here.
You're not using IPv6 so "IPv4 only" seems more logic to me.
When you are connected, can you ping 192.168.1.1 ?
Can you ping a device on LAN, like your plesk server ?
Does DNS work ?
Test with Resolver in pure Resolver mode (1.1.1.1 and 1.0.0.1 aren't needed anyway). -
No internet - could just be that you can not resolve.. Did you set the resolver ACLs correctly? Out of the box it will auto allow your local networks, but not a tunnel network.
As to getting lan clients - do their firewalls allow access from your tunnel network?
No need to remove lan net as source - that has NOTHING to do with traffic from your vpn tunnel.. And is correct..
-
when connected to OpenVPN tunnel from a cellular network through iOS, yes I can actually use safari to log into pfSense firewall at 192.168.1.1.
as far as clients firewalls allowing access from tunnel network, I don't know. Using my previous firewall solution as soon as I connected to OpenVPN, I could access my plex server no problem. How can I allow access from "tunnel" network?
As far as setting resolver ACLs correctly, I have to learn how to do that.
Also, the routes that I see in johnpoz OpenVPN client logs: I don't see routing on mine...
-
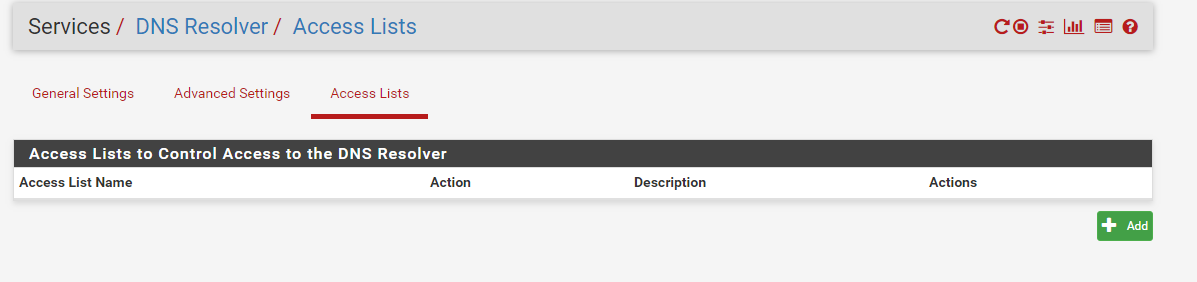
I assume this is the setting you're talking about, johnpoz... nothing there... -
So your using the automatic ALCs, which I do not believe adds your tunnel network.. So no you wouldn't be able to resolve anything. if your asking unbound on pfsense.
As to routing, if your using the default all through vpn your fine. But if you can not resolve this would explain no internet, and might also explain no plex access if your trying to resolve it vs access it by IP.
-
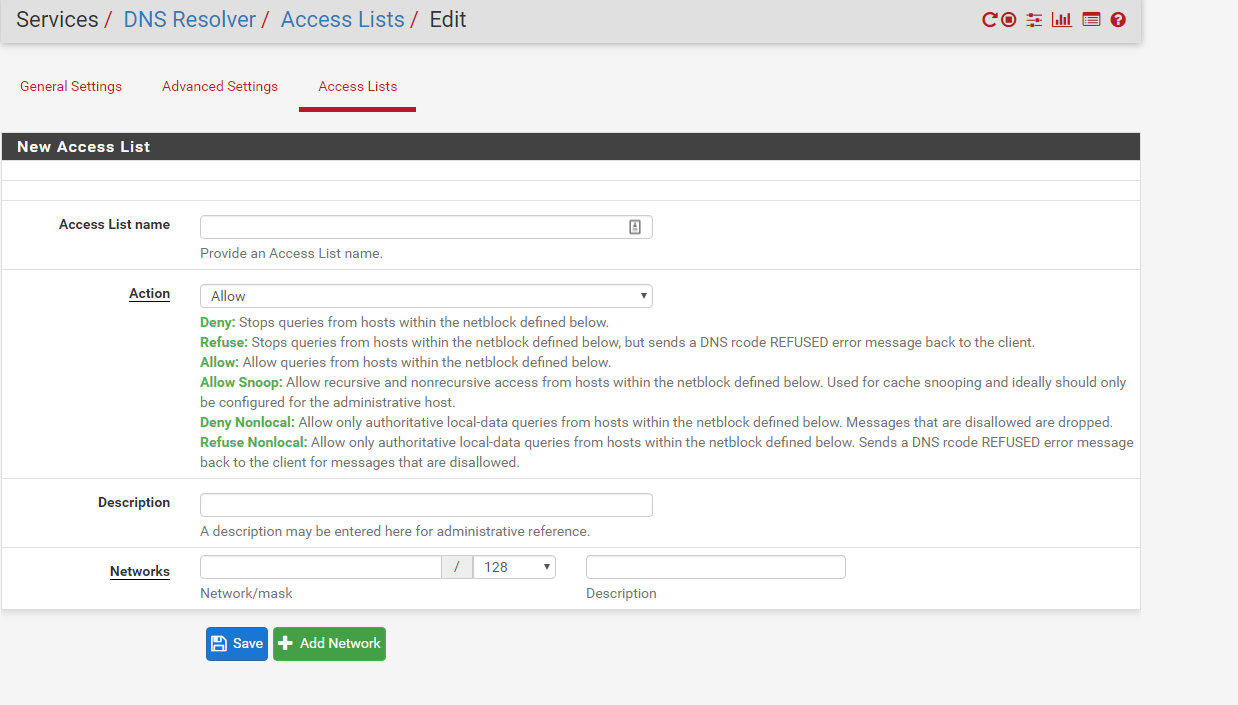
i understand now. Undernetworks in the above screenshot, should I add 192.168.2.0? -
Yes you should add your tunnel network and the correct mask for your tunnel network ie using /24 I do believe.
I disable the auto acls - so I manually add them
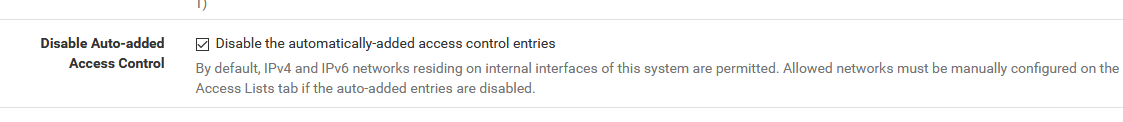
But default is enabled, so as you see only internal networks are allowed - not tunnel networks.
Should prob check any docs about setting up openvpn and make sure this mentioned, or make sure the tunnel networks are auto added, which I do not believe they are - but would have to double check that... The quick way to test is just do a simple query to your unbound running on pfsense from your vpn client. To validate if you can resolve or not.
-
thank you! adding the resolver settings for tunnel network fixed it.
I appreciate all of your help very much! -
I have this
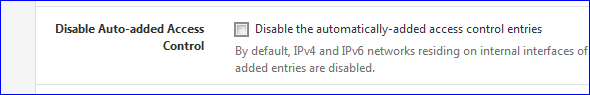
Isn't that default : non-checked ?
My Resolver ACL list is totally empty.
I can reach all my LAN's just fine from using the OpenVPN.A not working DNS should not impact a ping to a LAN IP, the Plesk device.
-
Non working dns doesn't stop a ping via IP, but stuff doesn't work if your trying to use fqdn to ping ;)