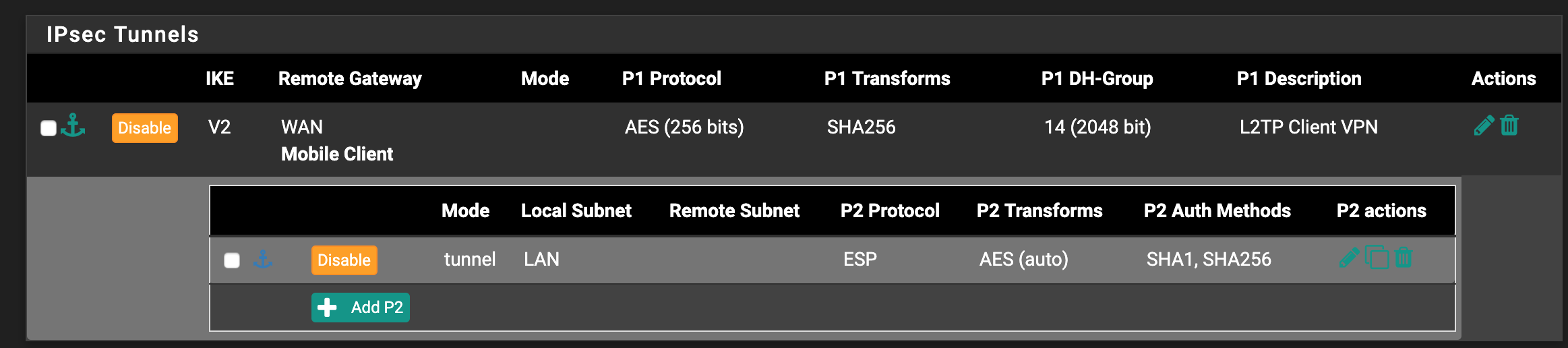
IPSEC won't connect beyond Phase 1
-
I am new to pfsense but am looking to move to it as a more robust firewalling solution. I have been working for about two days now trying to get a simple L2TP client vpn setup between the box (2.4.4.2) and a Mac client running the latest OSX version. In short, the client logs show that the connection is not getting past Phase 1 in the initiation process. I have posted an output of the logs as well from the pfsense box. I have changed just about every setting I can in the Phase 1 criteria to no avail.
Apr 15 18:40:25 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 18:40:25 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 18:40:25 charon 15[IKE] <20> IKE_SA (unnamed)[20] state change: CREATED => DESTROYING Apr 15 18:40:25 charon 15[MGR] <20> checkin and destroy IKE_SA (unnamed)[20] Apr 15 18:40:25 charon 15[MGR] checkin and destroy IKE_SA (unnamed)[20] Apr 15 18:40:25 charon 15[NET] <20> sending packet: from 144.202.66.15[500] to 170.225.9.140[401] (40 bytes) Apr 15 18:40:25 charon 15[ENC] <20> generating INFORMATIONAL_V1 request 2897491614 [ N(NO_PROP) ] Apr 15 18:40:25 charon 15[IKE] <20> no IKE config found for 144.202.66.15...170.225.9.140, sending NO_PROPOSAL_CHOSEN Apr 15 18:40:25 charon 15[CFG] <20> ike config match: 0 (144.202.66.15...%any IKEv2) Apr 15 18:40:25 charon 15[CFG] <20> looking for an IKEv1 config for 144.202.66.15...170.225.9.140 Apr 15 18:40:25 charon 15[ENC] <20> parsed ID_PROT request 0 [ SA V V V V V V V V V V V V ] Apr 15 18:40:25 charon 15[NET] <20> received packet: from 170.225.9.140[401] to 144.202.66.15[500] (788 bytes) Apr 15 18:40:25 charon 15[MGR] created IKE_SA (unnamed)[20] Apr 15 18:40:25 charon 15[MGR] created IKE_SA (unnamed)[20] Apr 15 18:40:25 charon 15[MGR] checkout IKEv1 SA by message with SPIs 1c5b03cba65ebed5_i 0000000000000000_r Apr 15 18:40:25 charon 15[MGR] checkout IKEv1 SA by message with SPIs 1c5b03cba65ebed5_i 0000000000000000_r Apr 15 18:40:22 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 18:40:22 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 18:40:22 charon 15[IKE] <19> IKE_SA (unnamed)[19] state change: CREATED => DESTROYING Apr 15 18:40:22 charon 15[MGR] <19> checkin and destroy IKE_SA (unnamed)[19] Apr 15 18:40:22 charon 15[MGR] checkin and destroy IKE_SA (unnamed)[19] Apr 15 18:40:22 charon 15[NET] <19> sending packet: from 144.202.66.15[500] to 170.225.9.140[401] (40 bytes) Apr 15 18:40:22 charon 15[ENC] <19> generating INFORMATIONAL_V1 request 1338941332 [ N(NO_PROP) ] Apr 15 18:40:22 charon 15[IKE] <19> no IKE config found for 144.202.66.15...170.225.9.140, sending NO_PROPOSAL_CHOSEN Apr 15 18:40:22 charon 15[CFG] <19> ike config match: 0 (144.202.66.15...%any IKEv2) Apr 15 18:40:22 charon 15[CFG] <19> looking for an IKEv1 config for 144.202.66.15...170.225.9.140 Apr 15 18:40:22 charon 15[ENC] <19> parsed ID_PROT request 0 [ SA V V V V V V V V V V V V ] Apr 15 18:40:22 charon 15[NET] <19> received packet: from 170.225.9.140[401] to 144.202.66.15[500] (788 bytes) Apr 15 18:40:22 charon 15[MGR] created IKE_SA (unnamed)[19] Apr 15 18:40:22 charon 15[MGR] created IKE_SA (unnamed)[19] Apr 15 18:40:22 charon 15[MGR] checkout IKEv1 SA by message with SPIs 1c5b03cba65ebed5_i 0000000000000000_r Apr 15 18:40:22 charon 15[MGR] checkout IKEv1 SA by message with SPIs 1c5b03cba65ebed5_i 0000000000000000_rIPSEC Configuration
-
@gh0stwr1ter
Hey
You use IKEv2 in IPSEC Mobile client settings
A Mac OS L2tp/IPSEC client (RACOON) uses IKEv1 (PFSense side)
Try to configure so- Server side
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/l2tp-ipsec.html
Or is it better to configure the bundle MacOs/pfsense is also using IKEv2
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.htmlI use Apple configurator 2 to create a VPN profile
- Server side
-
Thanks for the quick reply. I tried your suggestion above using AC2 and found the Mac now gets past Phase 1. However, per the client output logs it still gets hung up and fails.
Client Logs:
Mon Apr 15 15:33:07 2019 : IPSec connection started Mon Apr 15 15:33:07 2019 : IPSec phase 1 client started Mon Apr 15 15:33:07 2019 : IPSec phase 1 server replied Mon Apr 15 15:33:08 2019 : IPSec phase 2 started Mon Apr 15 15:33:08 2019 : IPSec phase 2 established Mon Apr 15 15:33:08 2019 : IPSec connection established Mon Apr 15 15:33:08 2019 : L2TP sent SCCRQ Mon Apr 15 15:33:28 2019 : L2TP cannot connect to the serverServer Logs:
Apr 15 20:34:09 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:34:09 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:34:09 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:34:09 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:37 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:33:37 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:33:37 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:37 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:29 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:33:29 charon 15[MGR] IKE_SA checkout not successful Apr 15 20:33:29 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:29 charon 15[MGR] checkout IKEv1 SA with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:28 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 20:33:28 charon 15[MGR] checkin and destroy of IKE_SA successful Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> IKE_SA con-mobile[46] state change: DELETING => DESTROYING Apr 15 20:33:28 charon 15[MGR] <con-mobile|46> checkin and destroy IKE_SA con-mobile[46] Apr 15 20:33:28 charon 15[MGR] checkin and destroy IKE_SA con-mobile[46] Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> IKE_SA con-mobile[46] state change: DELETING => DELETING Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> IKE_SA con-mobile[46] state change: ESTABLISHED => DELETING Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> deleting IKE_SA con-mobile[46] between 144.202.66.15[144.202.66.15]...75.129.232.186[192.168.1.8] Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> received DELETE for IKE_SA con-mobile[46] Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> 16: 75 F9 79 D5 2A F3 05 43 74 B9 CF 2F 80 D5 57 24 u.y.*..Ct../..W$ Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> 0: 6A 3C 18 76 CF 3B 67 6D 30 28 82 CB DD CA A5 C4 j<.v.;gm0(...... Apr 15 20:33:28 charon 15[IKE] <con-mobile|46> Hash => 32 bytes @ 0x80d26bf00 Apr 15 20:33:28 charon 15[ENC] <con-mobile|46> parsed INFORMATIONAL_V1 request 2630936284 [ HASH D ] Apr 15 20:33:28 charon 15[NET] <con-mobile|46> received packet: from 75.129.232.186[4500] to 144.202.66.15[4500] (108 bytes) Apr 15 20:33:28 charon 15[MGR] IKE_SA con-mobile[46] successfully checked out Apr 15 20:33:28 charon 15[MGR] IKE_SA con-mobile[46] successfully checked out Apr 15 20:33:28 charon 09[MGR] <con-mobile|46> checkin of IKE_SA successful Apr 15 20:33:28 charon 09[MGR] checkin of IKE_SA successful Apr 15 20:33:28 charon 09[MGR] <con-mobile|46> checkin IKE_SA con-mobile[46] Apr 15 20:33:28 charon 09[MGR] checkin IKE_SA con-mobile[46] Apr 15 20:33:28 charon 15[MGR] checkout IKEv1 SA by message with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:28 charon 15[MGR] checkout IKEv1 SA by message with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:28 charon 09[CHD] <con-mobile|46> CHILD_SA con-mobile{6} state change: DELETED => DESTROYING Apr 15 20:33:28 charon 09[CHD] <con-mobile|46> CHILD_SA con-mobile{6} state change: DELETING => DELETED Apr 15 20:33:28 charon 09[IKE] <con-mobile|46> closing CHILD_SA con-mobile{6} with SPIs c0c415ba_i (700 bytes) 08c2fcd3_o (0 bytes) and TS 144.202.66.15/32|/0[udp/l2f] === 75.129.232.186/32|/0[udp/63956] Apr 15 20:33:28 charon 09[CHD] <con-mobile|46> CHILD_SA con-mobile{6} state change: INSTALLED => DELETING Apr 15 20:33:28 charon 09[IKE] <con-mobile|46> received DELETE for ESP CHILD_SA with SPI 08c2fcd3 Apr 15 20:33:28 charon 09[IKE] <con-mobile|46> 16: BC FC 0C 02 74 FC 73 CC C6 6C 9D 4B 01 57 5C E4 ....t.s..l.K.W\. Apr 15 20:33:28 charon 09[IKE] <con-mobile|46> 0: 7D 9D 0C B1 34 02 2B CD 90 77 AF 64 5D E0 60 27 }...4.+..w.d].`' Apr 15 20:33:28 charon 09[IKE] <con-mobile|46> Hash => 32 bytes @ 0x80d257020 Apr 15 20:33:28 charon 09[ENC] <con-mobile|46> parsed INFORMATIONAL_V1 request 1527961049 [ HASH D ] Apr 15 20:33:28 charon 09[NET] <con-mobile|46> received packet: from 75.129.232.186[4500] to 144.202.66.15[4500] (92 bytes) Apr 15 20:33:28 charon 09[MGR] IKE_SA con-mobile[46] successfully checked out Apr 15 20:33:28 charon 09[MGR] IKE_SA con-mobile[46] successfully checked out Apr 15 20:33:28 charon 09[MGR] checkout IKEv1 SA by message with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r Apr 15 20:33:28 charon 09[MGR] checkout IKEv1 SA by message with SPIs 317d0b7c69adf824_i 1a5ca99ec89858e2_r -
Documentation PFSense is also written that the possible problems with connection of L2TP/IPsec clients behind a NAT. And it is recommended to use IKEv2.
received packet: from 75.129.232.186[4500] to 144.202.66.15[4500] (92 bytes)I also recommend setup remote access using IKEv2
For example,
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/configuring-an-ipsec-remote-access-mobile-vpn-using-ikev2-with-eap-mschapv2.html