New installation strange behavior - I can access web interface. however, I can't ping to the device
-
Hi,
I have try reinstall pfsense (2.4.4-RELEASE-p2 (amd64) )few times and once I installed I can ping to the LAN IP address. however, ping only works for few minutes and then timed out.
I can access web interface.
Unfortunately, I can't test anything without try ping to the device.
Is that something I missing here and any advice will be much appreciated ?
-
Do you have any packages installed like Snort or Suricata? You should be able to ping the LAN interface literally forever.
-
I have got it working. Need a rule in firewall to allow ICMP and out the box pfsence disable icmp by looking at the config.
Problem solved.
-
What? Out of the box, you don't need any rules on LAN to allow all traffic to pass to anywhere. The default Allow LAN to Any rule passes all LAN traffic. If you were on an internal interface other than LAN then yes, you need to add at least one rule.
-
I have LAN interface. I thought you will need a rule (adding the rule it works for pinging from device in the same LAN)
I thought it should work as the same way you thinking. However, It is not working until I put up a rule in firewall > LAN to allow everything to LAN Addresses
My behavior was when I reboot the pfsense ping works for only for 5 pings and then request timed out after firewall load up on the pfsense screen.
-
Rules either allow or deny access. There is no way a rule would allow access for a little while and then deny it, with the exception of rules linked to a time schedule. Whatever. If you think it's working then great.
-
If he accesses the box on the LAN side but NOT from the LAN net configured (e.g. having a core switch behind and accessing from a different VLAN than say the LAN/transfer net) you'll get exactly that. The default LAN allow any rule only covers the LAN net, not any RFC1918 networks behind some switch/router. The anti-lockout rule has "any" as source configured because of that.
-
Hi,
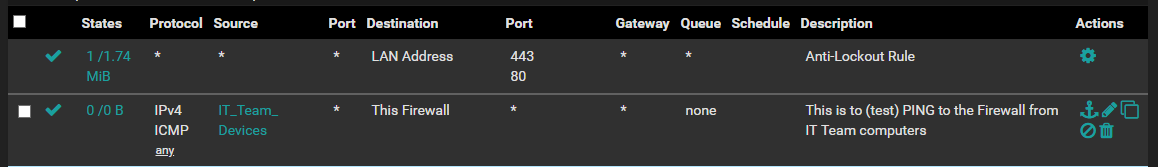
Thanks for the update.
I have to add second rule to get the ping working as the first rule preventing lan IP sending ICMP packets.
Hope this help to someone.
-
Again, that's what I wrote. Anti-Lockout is "globally" using any to give you any chance to still reach the box and not bugging out on you if you do some crazy things(TM). The default any-any allow rule after a new installation/firmware reset only covers the "LAN_net" e.g. the same network configured on the LAN side of pfSense. Your client not in there? You got no ping! :)
-
Thanks. :)
-
Dear JeGr,
In normal behavior rule disabling and enabling is instant affect on firewalls. Once I disable the above rule the firewall need a full power cycle to affect the rule. Is there any easy way of doing this may be restart services ???
Thanks in advanced
-
@popeel-SSH said in New installation strange behavior - I can access web interface. however, I can't ping to the device:
Once I disable the above rule the firewall need a full power cycle to affect the rule. Is there any easy way of doing this may be restart services ???
Which rule do you refer to? All normal pf-based firewall rules don't require a powercycle. In fact the only time I need to restart is an update?
-
@JeGr said in New installation strange behavior - I can access web interface. however, I can't ping to the device:
All normal pf-based firewall rules don't require a powercycle. In fact the only time I need to restart is an update?
Second rule on the picture ICMP any rule. Once I enable it I can ping and then I disable it . still I can ping to the firewall. However, with one reboot will stop ping that means the rule affected after reboot. Tried few different times.
-
you clearly do not need to reboot, your rules just need to be reloaded, which what happens when you click apply
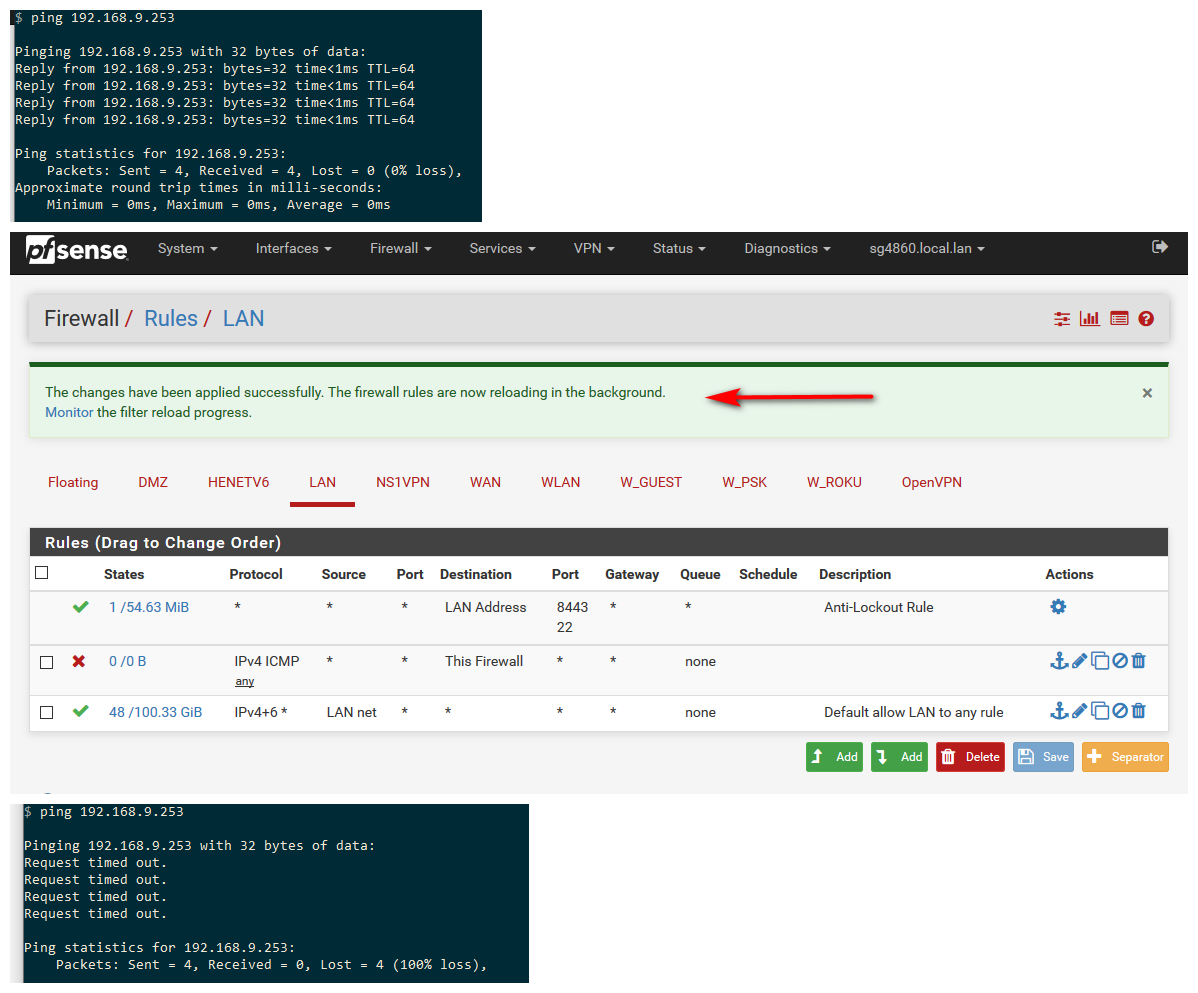
My guess is since your using an alias, which only get updated every 5 minutes you would have to wait for the alias to get populated.
You can also see that rule has been triggered by the counter next to the rule
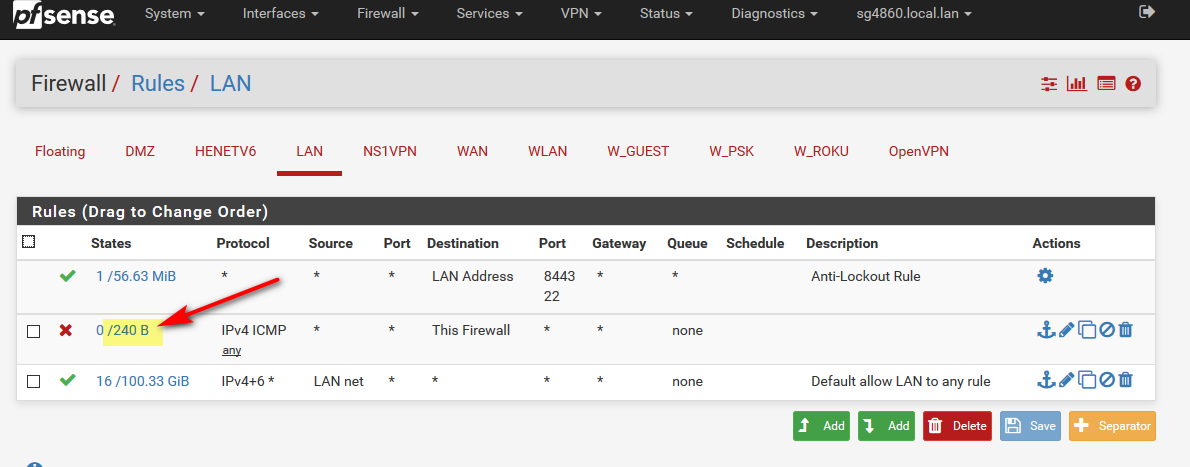
Other thing to keep in mind when adding/changing rules - is possible states that already exist, you would have to wait for the states to timeout, closed or kill them.
-
Unfortunately, mine isn't behave like that. I left for hours and still I can ping. Only solutions are either use States and reset or reboot.
-
Further for your info, It's not the alias causing this as I have already tried with one host IP and the behavior still the same.
-
When you click apply monitor the reload.. You sure your rules are actually being reloaded?
Look at you full rule set after you apply
https://docs.netgate.com/pfsense/en/latest/firewall/viewing-the-full-pf-ruleset.html -
@johnpoz said in New installation strange behavior - I can access web interface. however, I can't ping to the device:
You sure your rules are actually being reloaded?
Look at you full rule set after you applyIt has reloaded fine without any issues and output to pfctl -vvsr doesn't show the rule as I have already disable it.
Still I can ping to the firewall. What I have find was still there is a connection in States table for my ip to the firewall ip icmp connection.
Looks like pfsense doesn't remove existing connections with the firewall rule disabling. However, it does work when I enable rule to get the traffic pass through like I said before ping keep the connection until next reboot or reset states table.
I have tried this with 3 different hardware.
-
@popeel-SSH said in New installation strange behavior - I can access web interface. however, I can't ping to the device:
still there is a connection in States table for my ip to the firewall ip icmp connection.
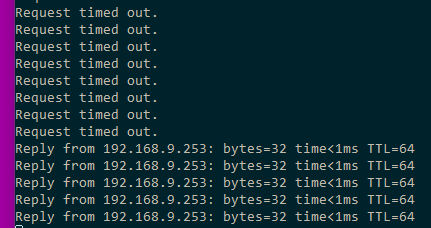
Yeah - if you have an existing rule that allowed the ping - state created... Then new rule that blocks, if the state is still there you have to remove that state!
States are looked at before rules - this is how a stateful firewall works!
here created a block rule for ping - pinging away... See the state.. Then delete the state and bam no more pings

now deleted the rule and bam pings start working again
auto flushing of states on rule changes/additions/deletions could be a BAD thing.. And cause all kinds of issues depending on the rules in place, etc.. You could kill the connections on things you did not mean to stop... So the person admin the firewall should understand this... And if some change to rules is made that might have states that allow - just be like surgeon and kill only the specific states. Or sure you could use a HAMMER and reset ALL of them... But this could really piss off a lot of users, etc.
-
@johnpoz said in New installation strange behavior - I can access web interface. however, I can't ping to the device:
And if some change to rules is made that might have states that allow - just be like surgeon and kill only the specific states. Or sure you could use a HAMMER and reset ALL of them... But this could really piss off a lot of users, etc.
This is what I understand of this pfsense firewall. However, I have used CISCO and Juniper before and the behaviour is diferent. They flush the connections (only related connections) as soon I disable the rule.
Pfsense do not do that as we might need to find the rule and delete that.
I am still learning this firewall and Thanks for your help and much appriciated.