[SOLVED] First time install. Need help!
-
Hello all!
I am very new in pfSense (just installed). I need to setup network based on this image:
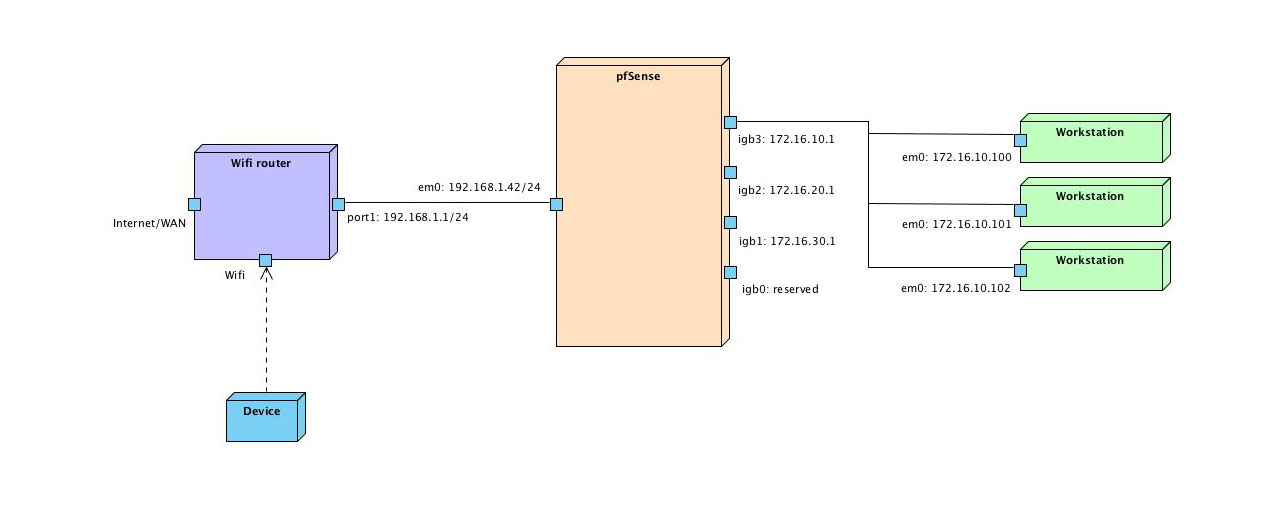
For now pfSense instance in default setup condition without any VLANs, NATs, RULEs or any other settings.
What I need to setup:
- On every igb[0,1,2,3] interface kind of subnetwork 172.16.[0,10,20,30].*/24 need to be
- Assign pfSense web UI only for igb3: 172.16.10.1
- Allow access to the internet from igb0, igb1, igb2, igb3 but block everything from internet to this interfaces.
- Make visible any hosts to each other in 172.16..
- Install inner DNS that will be only for 172.16..
- OpenVPN that will allow access to 172.16.. from Wifi devices thorough VPN connection only.
Any other suggestions about improving security is good too.
Could anyone help me?
-
This post is deleted! -
@KOM The problem is in my first time install of pfSense. I don't know what is automated by pfSense what should be done manually. I don't know the principle sequence of actions for getting done that described above. For now I have troubles with accessing to the internet from 172.16.10.* But from the side of WiFI devices I could access to 172.16.10.* There should be in opposite direction from inner network - ability to get internet. Everything described in image. I need to release this kind of network solution based on pfSense.
-
This post is deleted! -
@KOM said in First time install. Need help!:
Looks like you need to start reading, learning, experimenting and then come back when you have specific questions when you get stuck
Thanks for very-very-very useful assistance ...
-
Ok so by default traffic from WAN, em0, is blocked to any internal interfaces so 'block everything from internet to this interfaces' is taken care of already.
The default DNS Resolver, Unbound, listens on all interfaces but it blocked from WAN by default so #4 is already in place.
You should make your LAN interface igb3 as that has the anti-lockout rule that gives access to the webgui by default. It can be disabled but it's useful to have it there.
Then on the internal interfaces add rules in the following order:
pass from interface subnet to interface IP DNS traffic.
pass from interface subnet to interface IP NTP traffic.
block from interface subnet to 'This Firewall' all traffic.
pass all traffic.That should do everything you have outlined apart from OpenVPN but there are docs for that:
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/openvpn-remote-access-server.htmlSteve
-
@stephenw10 SUPER-MEGA-HUGE Thanks ... That what I need!
-
This post is deleted! -
Everyone remain calm!

-
@KOM In accordance to Aristotle - the first sign of real knowledge is ability to explain shortly the matter and teaching this matter. I wish you big money in your free time ... The information that I've got from @stephenw10 - all that I've been asking. For now all is working.