Port forward via OpenVPN
-
Hey!
I'm having trouble creating a port forward over a VPN tunnel.
I have a pfSense instance running OpenVPN and an RaspberryPi connecting to it. The tunnel is configured as an peer to peer tunnel. Pinging the Pi works just fine. Even SSH from the pfSense system itself.
Now I want to create a port forward rule so that I can SSH to the IP of the pfSense system but end up on the RPi.
I already tried creating different rules but with no success at all. (NAT-Port-Forwards, Outbound rules, Rules in all different interfaces)
I assigned the OpenVPN "adapter" to an interface for rule creation.Does anybody have experience with that? Thanks a lot!
A rough diagram of my goal:
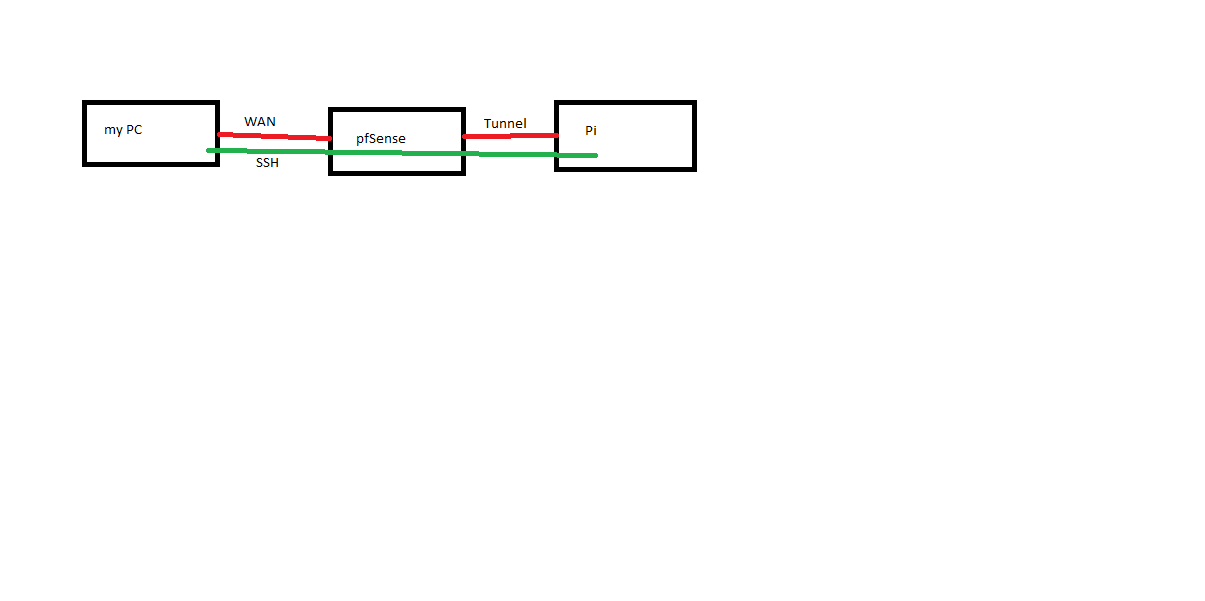
-
@mkapalla said in Port forward via OpenVPN:
Now I want to create a port forward rule so that I can SSH to the IP of the pfSense system but end up on the RPi.
Why want you do that with port forwarding?
Just set the routes and connect to the IP of the RPi . -
That would be possible if I also were connected to the pfSense system.
There is no direct route to this RPi. Imagine it like I want to access my webserver from a remote location with say my mobile phone. For that I need the port forward.The RPi is on a mobile network and I cannot connect to it directly. Therefore the VPN to this pfSystem. I want to access the RPi via pfSense.
-
So there is only a VPN between pfSense and RPi and you want to forward the pfSense WAN to it?
So on the RPi the default route has to point to the tunnel IP of pfSense. Is that given?
If you don't want that you have to use NAT (masquerading).
-
I don’t think the default route is set that way. But when I SSH into pfSense I can create a new SSH session from within the pfSense session to the RPi with ease. I don’t think that this is a problem.
I re-drawed my diagram to make it more understandable what my goal is:
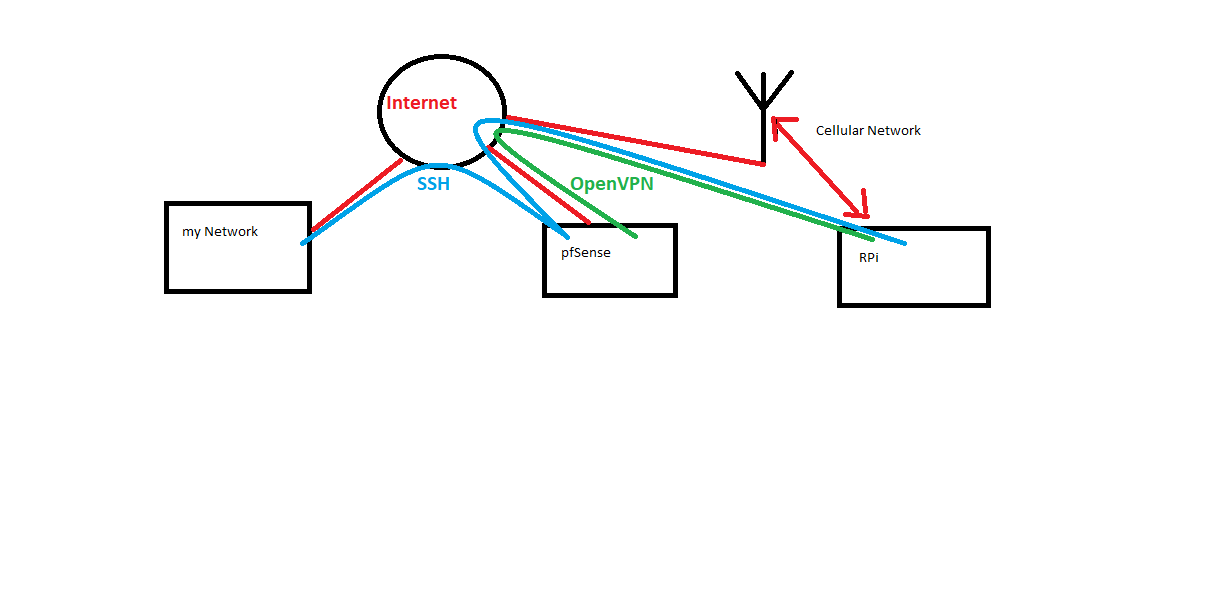
-
@mkapalla said in Port forward via OpenVPN:
I don’t think the default route is set that way.
So check it.
@mkapalla said in Port forward via OpenVPN:
But when I SSH into pfSense I can create a new SSH session from within the pfSense session to the RPi with ease.
pfSense and RPi are within the same network (VPN), your PC isn't.
So you need at least a route on the RPi for the source IP of your SSH connection directing packets back over the VPN to pfSense, or do masquerading at pfSense for that connection. -
The problem is probably that the Pi does not have the benefit of pf's reply-to which would automatically route reply traffic from arbitrary addresses back over the VPN.
You best bet is to perform outbound NAT at pfSense so the Pi sees those forwarded SSH connections as sourced from the OpenVPN tunnel address instead of the original source address of the client. It should then be able to route the reply packets properly.