Totally stumped
-
Totally Stumped :( :(
I am running PFsense 2.4.4 p2. I run all my connections through my VPN. The odd thing is My LAN connection routes through the VPN not issues. The problem is my DMZ routes through the WAN even though I have an manual outbound NAT telling it to route out the VPN exactly like the LAN. This was working perfectly till I moved from 2.4.3 to 2.4.4
Not sure what else to do besides go back to my old firewall.
Packages installed
pfblocker
NTOPAny ideas...
Thanks
Randy
-
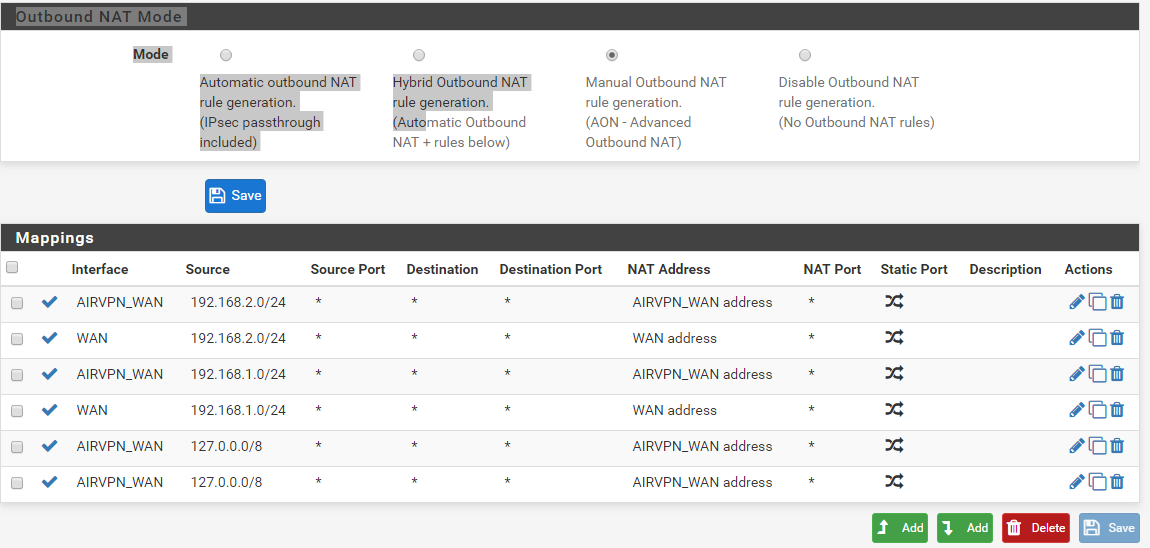
Post your firewall rules.
Why are you NATing 127.0.0.0/8 ?
https://en.wikipedia.org/wiki/Localhost
-
Because that would be the firewall itself going out... 127/8 is part of automatic nat rule set as well.
Lets see your rules on lan and dmz interfaces.
Do you have policy route sending dmz out your vpn? In you rules?
-
Yes, the outbound NAT rules do not determine which interface traffic will use. They only determine what translation will happen there if/when traffic exits by that interface.
Your policy routing rule on the DMZ interface is probably either missing or not catching the traffic as intended.Steve
-
LAN Rules
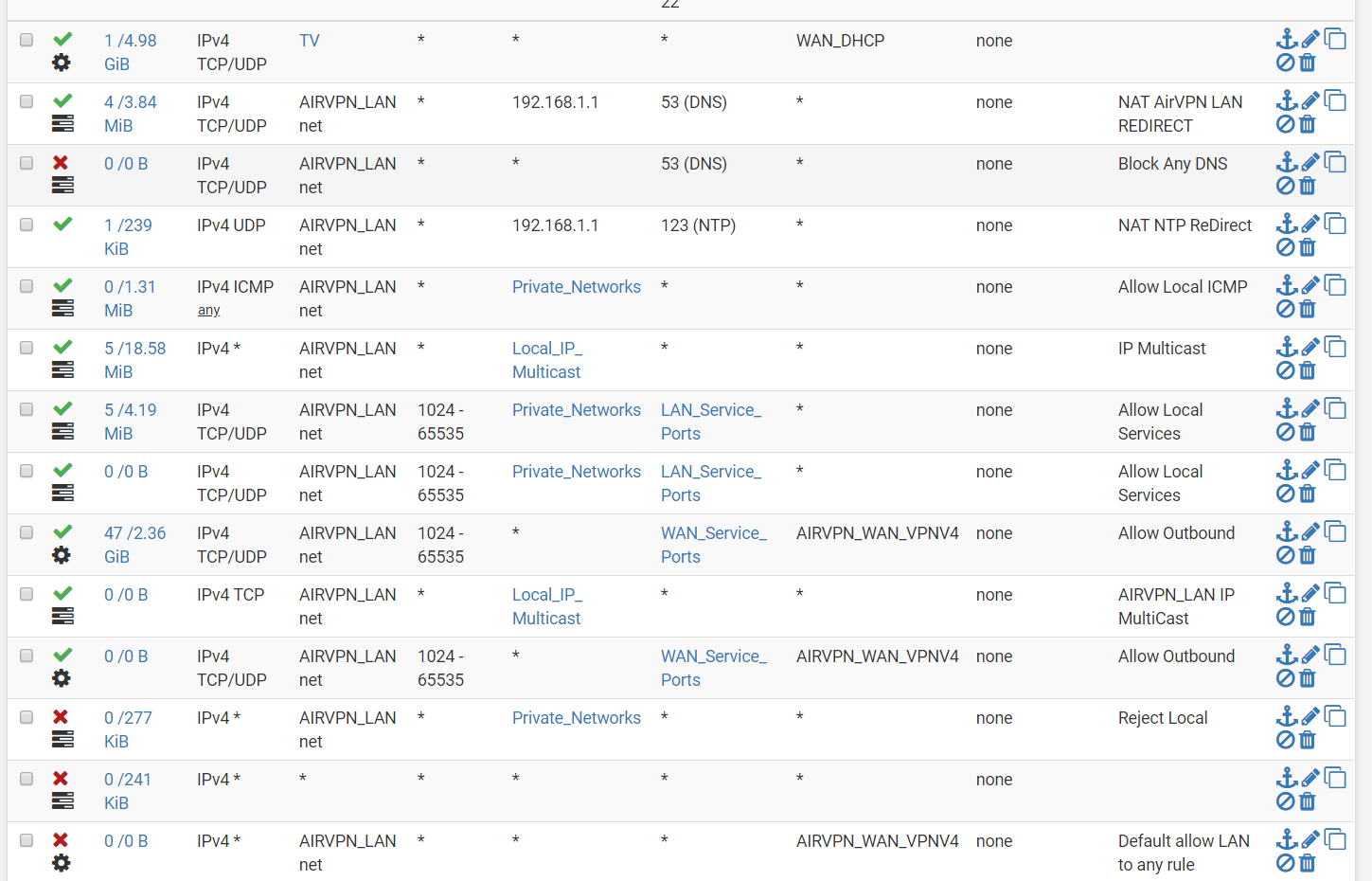
DMZ Rules
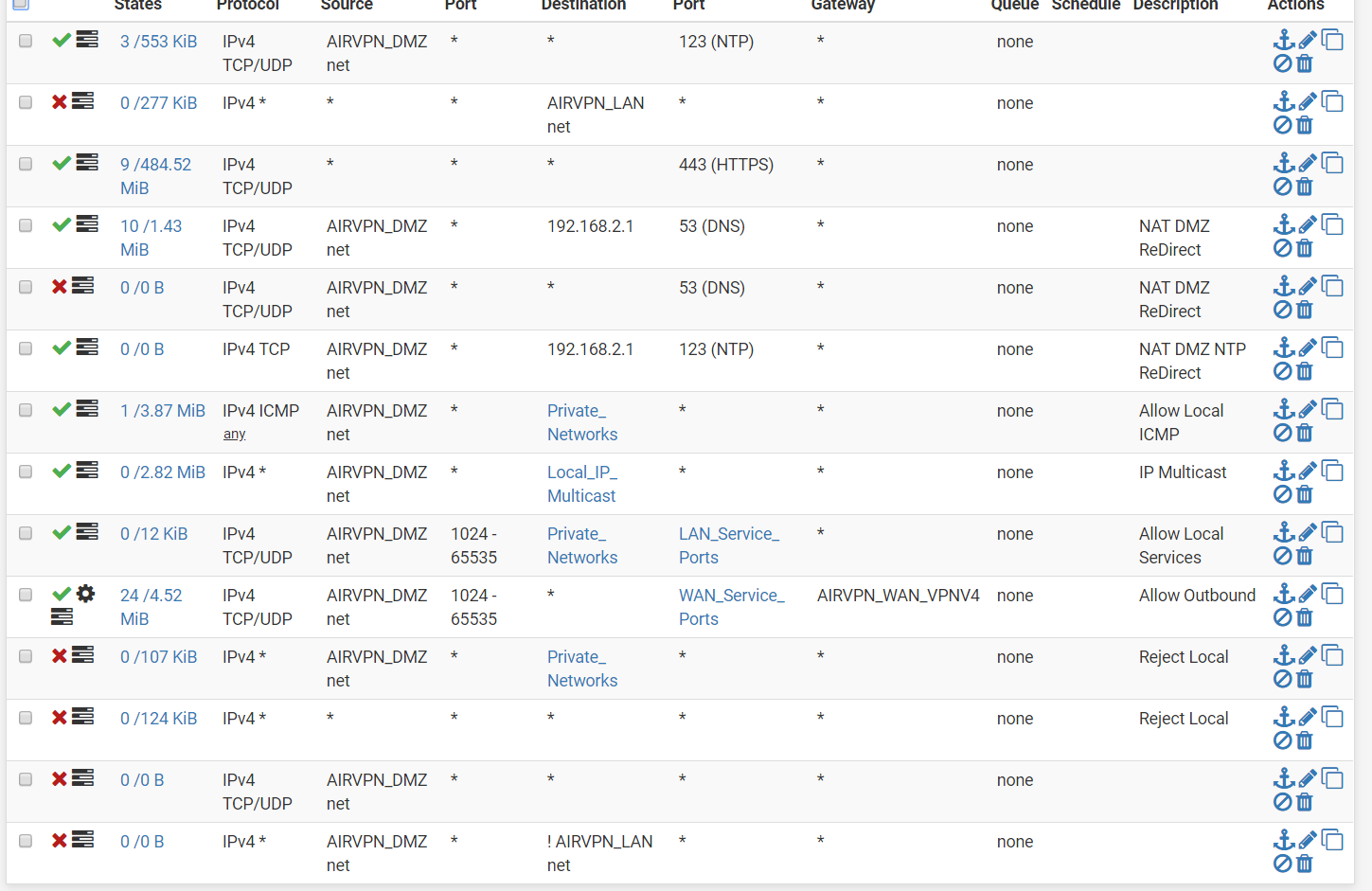
-
Guys;
This is the exact config from my 2.4.3 build . I just restored my config on my 2.4.4 build. I didn't make an changes.
All that you see is from AirVPN setup guide guide. It worked fine until the upgrade
ThanksRandy
-
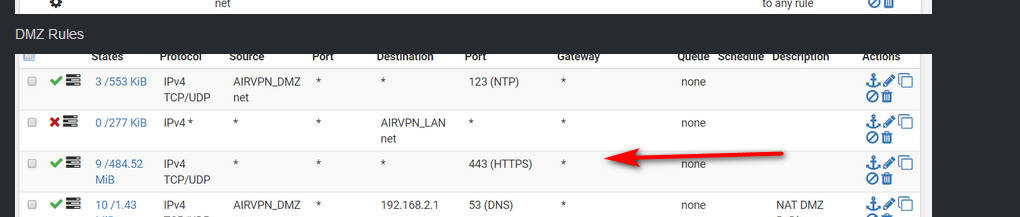
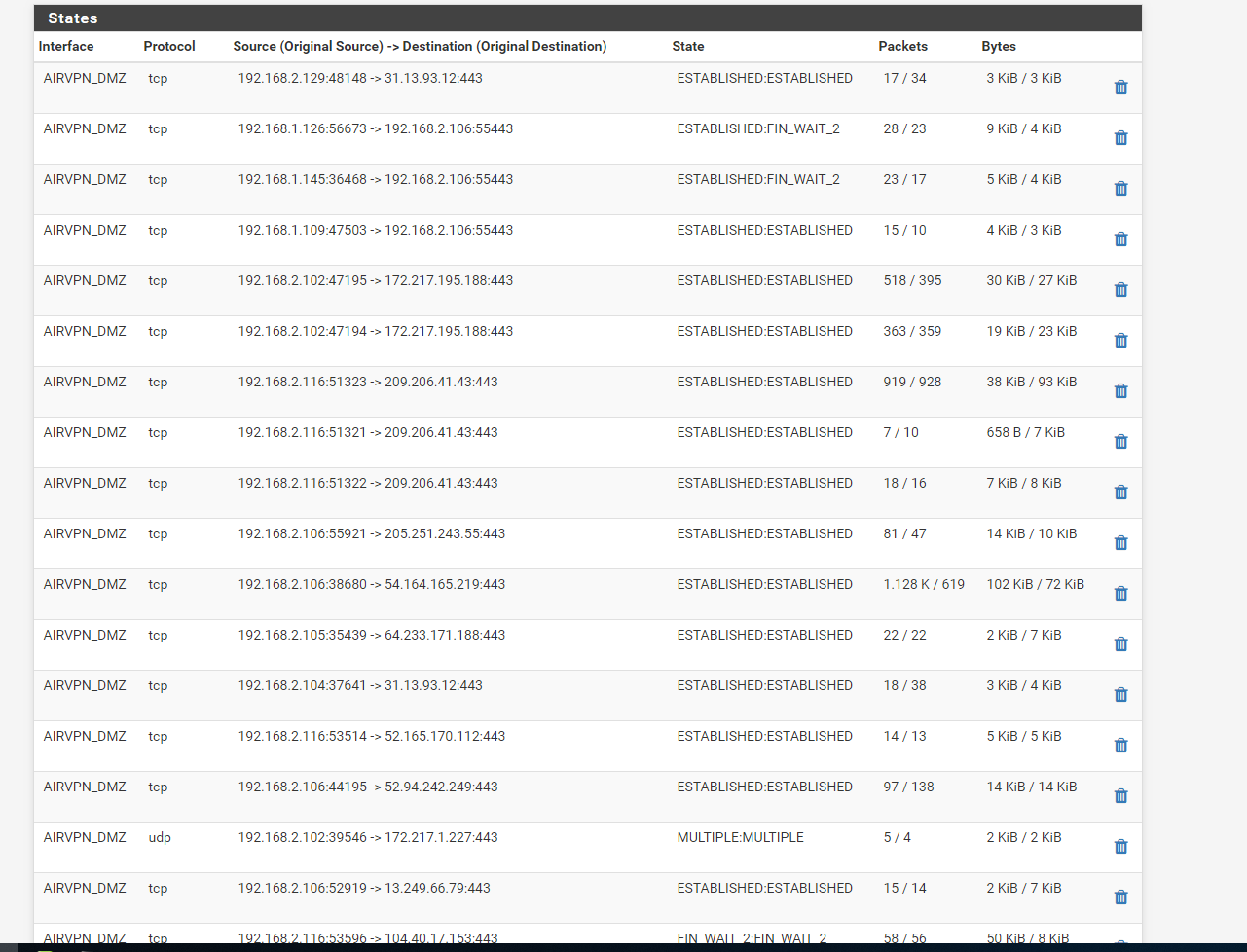
And what traffic exactly do you see going out your wan vs your vpn? Lets see your state table.
Your rules allow anything going out 443 to just use wan..
-
I'm not sure why I added the rule. I may have been troubleshooting and forgot to remove it.
Thanks
Randy
-
looks like all 443 traffic to me ;)
-
Yeah it does. I need to figure out why :(
If I do a What is my IP on a machine in the DMZ, It gives me back my WAN IP? I need all my traffic to go through the VPN.
-
Well you have a rule that says going to 443, just use default routing - so yeah going to go out the normal wan..
-
Yup.

Coming from 2.4.3 you should check your default gateway/route though. The handling of that changed significantly in 2.4.4 and it was possible to end up without a default route in some edge cases.
The VPN connection may have been previously setting a new default route when it connected. That's generally undesirable, better to specify exactly which gateways should be used.Steve
-
I changed that 443 rule to use the VPN gateway an now my What is my IP is returning my VPN address like I wanted. The odd thing is my LAN always returned my VPN address.
My gateway is set to my WAN by default. Should I make the VPN the default?
Thanks a lot
-
The best option when wanting to use vpn services is NOT to pull routes from them!!! I repeat - while they might list it in their guide to pull routes, etc. set them as default..
The better option is to NOT PULL ROUTES from your vpn service, and just policy route how you want - if you want everything to go out vpn, its simple rule.. If you want x to use wan and y to use vpn, again its very simple and straight forward with policy routing... Not so much when they are overriding your default route, etc. etc..
-
Do you recommend me changing the gateway to making the VPN the default not the WAN?
-
Nope. Do what johnpoz said above. Once the VPN client is not changing your default route when it connects you can better control exactly what traffic you want going where using policy routing.
Your LAN rules look to be policy routing everything over the VPN including port 443. It looks like that rogue 443 rule on DMZ was your issue.
Steve
-
The AirVPN guide has the Do not pull routes checked so that is what I do. I do override the VPN to allow Netflix to work and also my email server but that is it.
I learned something today.
Thanks guys. Much appreciated
Randy