public services access with NAT to the interal IP
-
Hi,
I am a new learner for pfsense.
I have public IP which will need to connect to internal IP with port 80 and 443 for web services.
How to archive this in the best way. It was very easy on CISCO ASA as there is a public service and add the public ip and service then add private ip and the service.
Any help will be much appreciated.
-
@popeel-SSH said in public services access with NAT to the interal IP:
I have public IP which will need to connect to internal IP with port 80 and 443 for web services.
a public IP on the WAN interface or an additional public IP on the WAN?
Otherwise you are simply talking (I think) about a "port forward". Go to NAT / Port forward, source any, destination "wan address", port 80, redirection IP <your internal IP> port 80 and do that again for 443.
Some basic documentation reading is highly recommended though!
https://docs.netgate.com/pfsense/en/latest/
https://docs.netgate.com/pfsense/en/latest/book/ -
Thanks. These docs are really helpful.
Thanks. :)
-
I have following rule from ASA to implement in pfsense. Not sure where I have done wrong. Please help and then I am done with this.
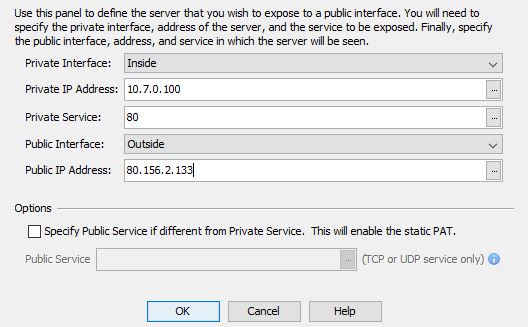
This is the rule I will need to implement in pfsense.
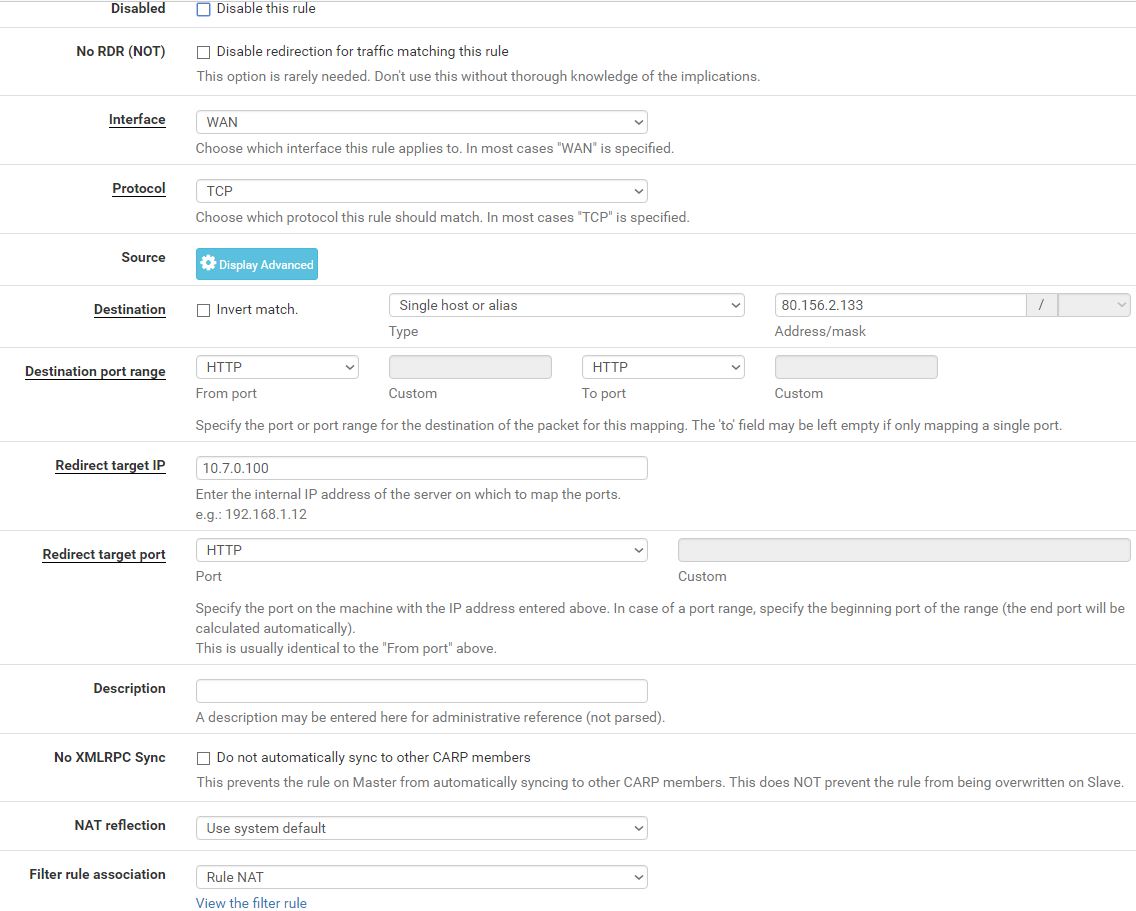
Not sure where I have done wrong and this isn't working.
-
On ASA you configured the rule on the inside / private interface so I assume the rule should allow the internal IP .100 to access port 80 on 80.156.2.133 on the internet?
If that's the case you have to set it up on the LAN interface in pfSense as well, not on the WAN as you did.Or what is it, you try to achieve with that rule?
Edit: Ah just saw it afterwards, that it's not a filter but a NAT rule. So you are trying to forward that 80... IP to 10.7.0.100 on the inside? Are you sure, that
- 80.156.2.133 is actually configured in your pfSense setup (if it's not your WAN IP, is it configured as an Alias/VIP?)
- If it's your actual WAN address: why don't you use <WAN address> or <This Firewall> as your Destination?
-
Well I have an web server in internal network (10.7.0.100) and webserver external IP is 80.156.1.133.
I would want firewall to redirect http traffice from 80.156.1.133 to internal ip 10.7.0.100 for external and internal people to access the website.
Hope this make sense.
-
Sure. But did you read my edit? Is the IP .133 actually configured on the firewall? Or is that a subnet you're getting routed to you? Or is it the actual IP of the pfSense WAN IF?
-
@JeGr said in public services access with NAT to the interal IP:
Is the IP .133 actually configured on the firewall? Or is that a subnet you're getting routed to you? Or is it the actual IP of the pfSense WAN IF?
This ip is part of the subnet of the WAN interface.
-
@popeel-SSH said in public services access with NAT to the interal IP:
This ip is part of the subnet of the WAN interface.
What's that? So you get something like .131 as your Gateway, .132 is pfSense and .133 you want to use for that web server? (as an example)?
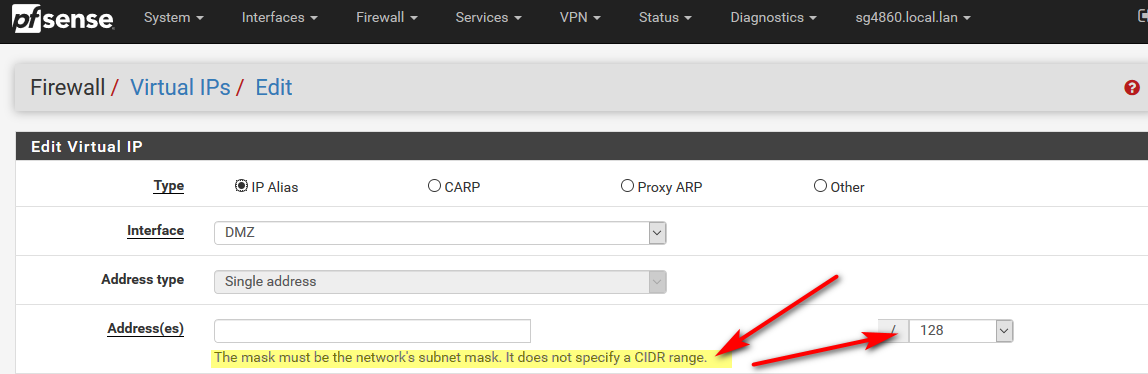
Then you have to configure .133 as an Alias via Firewall/Virtual IP before the firewall can actually get traffic for it!
-
IP is not the correct IP. I made that up for an example. Sorry not more specific.
OK. Please see see the below example.
IP address of the firewall 80.156.1.161
WAN Gateway 80.156.1.174Public IP that will connect to the private server via port 80 is 80.156.1.163
-
@popeel-SSH said in public services access with NAT to the interal IP:
Public IP that will connect to the private server via port 80 is 80.156.1.163
Did you set that up as a VIP on pfsense wan IP.. You can not forward from an IP that pfsense doesn't think is his..
-
This post is deleted! -
Right. got it working.
Setup virtual IP and then create NAT rule match the virtual IP and not type the IP Address.
Thanks for the help. You are a real star.
Thanks again
-
So /32 is not correct.. Should be using the mask of your netblock
Then also run through the troubleshooting guide.
https://docs.netgate.com/pfsense/en/latest/nat/port-forward-troubleshooting.htmlFirst thing I would do is actually validate traffic is hitting your wan with dest to that IP, with a packet capture.
edit: Oh you got it working - you deleted your last post saying you were still having issues.
Glad to hear.